July 2020 Platform Release: Asset Tag Selection and New Age Criteria in VMDR, and More
Last updated on: October 1, 2020
Table of Contents
The Qualys Cloud Platform July 2020 releases include Qualys Cloud Suite 3.1 and 10.2.1 releases, which contain new features in Qualys AssetView, Continuous Monitoring (CM), Policy Compliance (PC), Vulnerability Management (VM), Vulnerability Management, Detection and Response (VMDR), Security Assessment Questionnaire (SAQ), Unified Dashboard, and Web Application Scanning (WAS).
Feature Highlights
AssetView
External ID Read-Only for EC2 Connectors
AWS recommends the External ID should be read-only field as one of its best practices. Qualys has now standardized the EC2 connector creation process adhering to the best practices.
Qualys generates a unique External ID, and auto-populates it during EC2 connector creation. It is now a read-only field and you cannot edit the External ID field, thereby enhancing the security of your AWS account.
Continuous Monitoring
New Threat Protection RTIs – Wormable and Predicted High Risk
With this release, you can configure a ruleset to get alerts on active security threats using these Threat Protection Real-Time Threat Indicators:
Wormable – Wormable has been associated with this vulnerability. The vulnerability can be used in “worms” – malware that spreads itself without user interaction.
Predicted High Risk – Predicted High Risk has been associated with this vulnerability. Qualys Machine Learning Model predicted this vulnerability as a High Risk based on various data sources including NVD, Social network, Dark web, Security Blogs, Code repository, Exploits etc.
Policy Compliance
Dynamic Discovery & Assessment of Web Servers via Cloud Agents
Qualys Policy Compliance now enables dynamic discovery and assessment of middleware technologies like webservers in your environment using PC agents.
For assessment of middleware technologies, the minimum agent version installed must be:
- Windows Cloud Agent 4.0.x or later
- Linux Cloud Agent 2.8.x or later
The following middleware technologies are supported:
Linux Agent 2.8.x
Apache Tomcat 7.x
Apache Tomcat 8.x
Apache Tomcat 9.x
Pivotal tc Server 3.x
vFabric tc Server 2.9.x
Docker 1.x Docker CE/EE
Windows Agent 4.0.x
Apache Tomcat 7.x
Apache Tomcat 8.x
Apache Tomcat 9.x
MS IIS 10.x
MS IIS 8.x
MS IIS 7.x
Security Assessment Questionnaire
Vendor On-Boarding
Qualys SAQ now has added the ability to onboard new vendors, track the existing ones, and keep record of their areas of business as well as gain accurate visibility into the vendors’ records and related areas.
Vulnerability Management
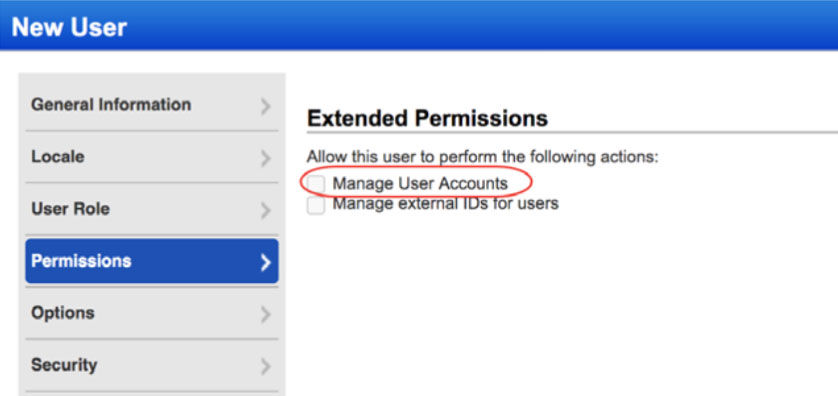
Ability to Manage User Accounts
The Manager Primary Contact (for the subscription) can now grant the Manage User Account permission to Managers, Unit Managers and User Administrators. When granted, the user can create, edit or delete users; however, they can’t grant this permission to other users.
By default, this option is enabled. In case the POC manager wants to restrict any users from having these permissions then the POC manager needs to uncheck this checkbox.
< MgrAccount.PNG>
VMDR: Vulnerability Management, Detection and Response
Asset Tag Selection
The first step towards VMDR prioritization report is choosing the asset tags. You can confine the list of vulnerabilities associated with the assets you select.
<select_asset_tags.png>
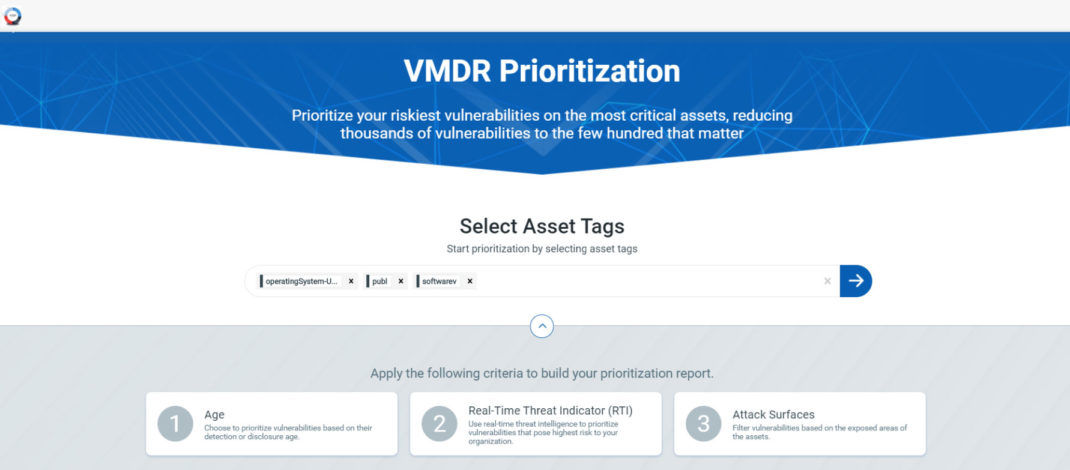
You need to select at least one asset tag before you proceed towards report creation. Select the Asset Tags to narrow down the assets and then click

New Age Criteria: Detection Age and Vulnerability Age
Age of a vulnerability can be a crucial factor in prioritizing. VMDR now has two new filters for age of the vulnerabilities that you can choose from:
Detection Age – Indicates the age from the day when the vulnerability was first detected.
Vulnerability Age – Indicates age from the day when the vulnerability was first disclosed. While it is important to understand how long a given detection has existed in your environment, the age of the vulnerability itself is also a key piece of information.
<age_filter.jpg>
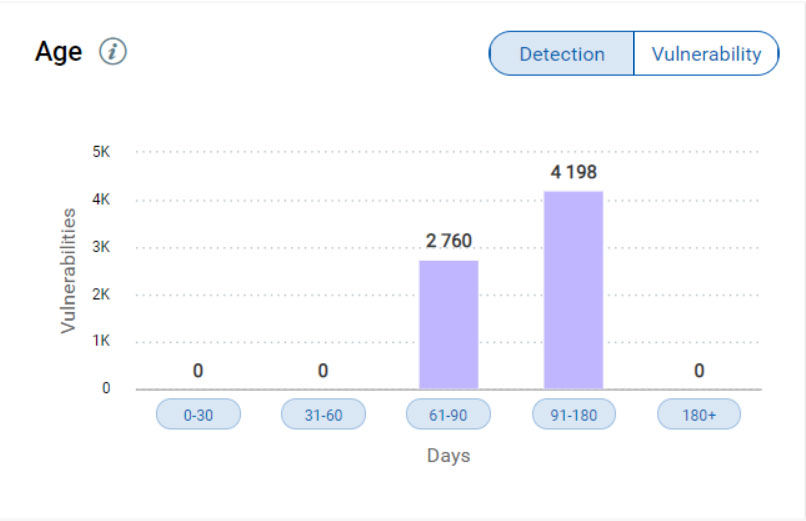
This can tell you if new systems are being built that have old vulnerabilities and can help to focus resources on making sure these vulnerabilities are removed from gold images.
Enhancements to RTIs and Attack Surface Filters
New features have been added to RTIs and Attack Surface filters, including the ability to match on Any or All selected RTIs, an easy toggle for Internet Facing vulnerabilities, and three new RTIs for fine-tuning your prioritization.
Now users can choose to increase or narrow the scope of vulnerabilities you want to prioritize and perform advanced queries such as “All Internet-Facing DoS vulnerabilities that have been reported as Actively Attacked.”
<rti_filter.jpg>
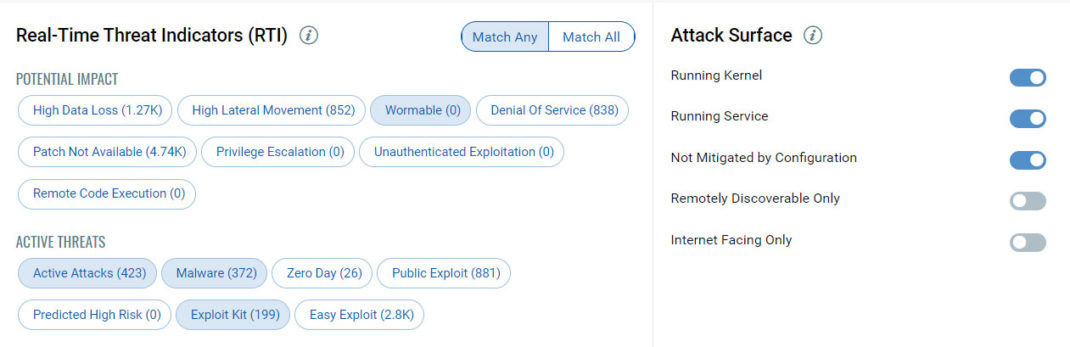
The following 3 new RTIs have been added:
- Privilege Escalation – Successful exploitation allows an attacker to gain elevated privileges.
- Unauthenticated Exploitation – Exploitation of this vulnerability does not require authentication.
- Remote Code Execution – Successful exploitation allows an attacker to execute arbitrary commands or code on a targeted system or in a target process.
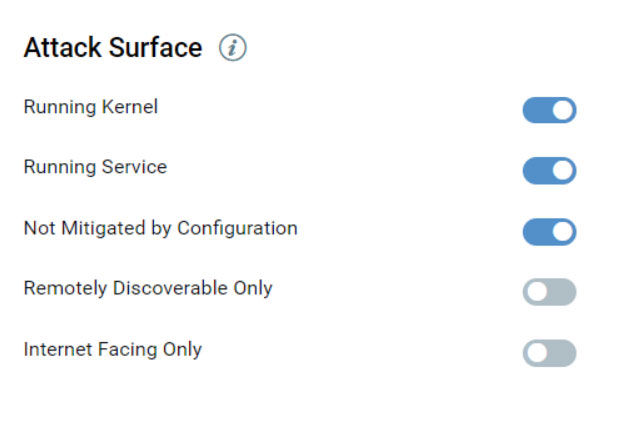
Internet Facing Only Attack Surface
A new attack surface named Internet Facing Only has been added. Toggle the filter to On to include assets with IP addresses that could be exploitable. By default, this filter is disabled. The attack surface primarily uses system-defined tag, named Internet Facing Assets (IFA). The tag includes pre-defined ranges of publicly routable IP addresses. This tag automatically tags assets with IPs that fall within the specified ranges.
<attack_surface.jpg>
Advanced Search
The search engine has been enhanced and is more powerful to help users with multiple property criteria such as vulnerability severity, detection age, and so on.
<search_1.jpg>
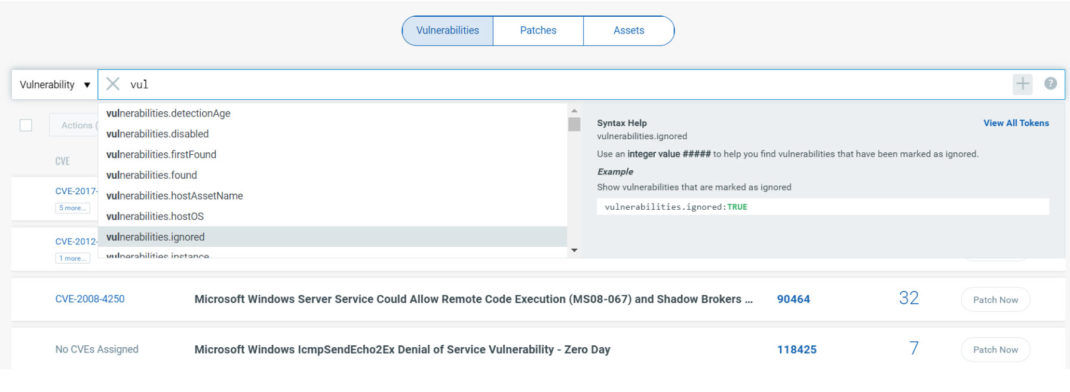
Users can also choose a combined Vulnerability and Asset search.
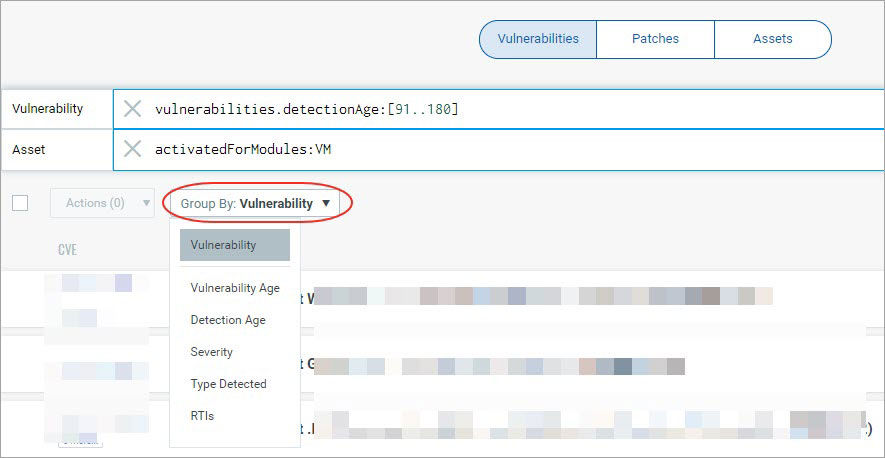
Grouping Report Data
Once the online VMDR prioritization report is generated, users can now organize the data further into logical groupings by using the several “Groups by” options such as detection age, vulnerability age, severity and more.
<group_by.jpg>
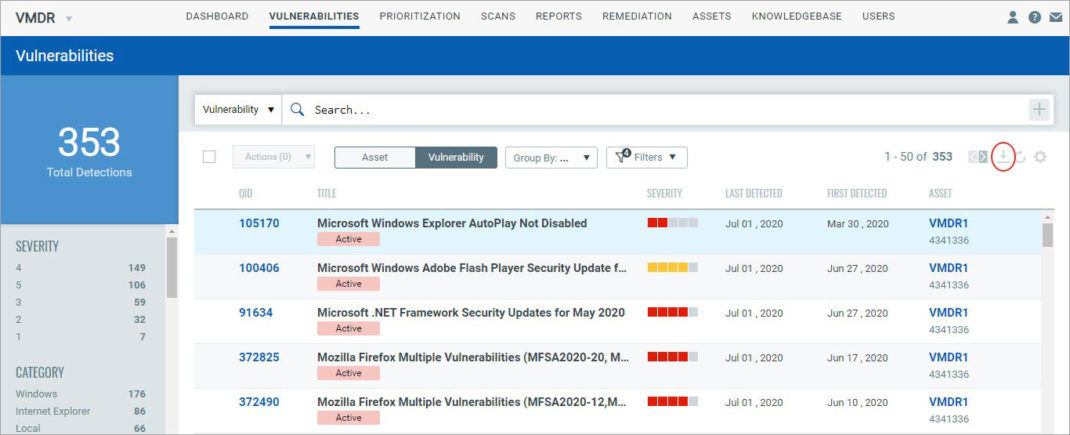
Save and Download Reports
You can save or save and download the VMDR prioritization report to your local system in a single click. On clicking Save, the VMDR prioritization report is saved to the reports list on Reports tab. On clicking Save & Download, the VMDR Prioritization report is saved to the report list and downloaded to your local system.
Vulnerability Status in CSV File
We have now introduced the status of vulnerabilities in the file you download from Vulnerabilities tab. When you download vulnerabilities in CSV format, we now include the status column, which indicates if the vulnerability is New or Active.
Go to Vulnerabilities tab and the vulnerabilities are displayed. You could type a search query to narrow down the list of vulnerabilities.
<vulns.jpg>
Upcoming Features in VMDR in 2020
This year, Qualys will be adding several major features to VMDR to make prioritization even more automated while keeping it simple and transparent. These features include Prioritization Scoring, Mitigating Control Mapping, and Mitigation Responses.
Prioritization Scoring
Our Prioritization Scoring will take in Asset, Vulnerability, and Threat information to produce a prioritization score for each detection. The formula will be completely customizable and transparent — no magic numbers.
Not all threats impact all types of hosts in the same way. Exploit Kits are used to attack workstations, not servers. Denial of Service vulnerabilities are often not prioritized, but what about internet-facing hosts? Because of this, Prioritization Scoring in VMDR will allow you to map specific threats to specific types of assets, using Dynamic Inventory Tags. We’ll have great out-of-the-box defaults to get you started, but every attribute of the score will be customizable.
Mitigating Controls
Not all vulnerabilities can be patched immediately. Sometimes a patch is not available, other times operational concerns require waiting to deploy the patch. For these cases, VMDR will be able to detect and deploy mitigating controls to reduce the risk of a vulnerability.
For example, if there is a new RDP vulnerability, we’ll show you if the impacted hosts have NLA, which could greatly impact an attacker’s attempt to exploit those hosts. If the control is not enabled, with a few clicks, you can implement those controls across multiple assets.
Unified Dashboard
New App Now Available
Update: Unified Dashboard is available in the Qualys Cloud Suite v3.2 release.
Qualys has introduced a new app named Unified Dashboard (UD) to enrich your dashboarding experience. Unified Dashboard (UD) brings information from all Qualys applications into a single place for visualization. UD provides a powerful new dashboarding framework along with platform service that will be consumed and used by all other products to enhance the existing dashboard capabilities. Dashboards can be used to convey relevant information to any audience at any time and in any place. The dashboards can be customized and shared with their intended end-users. Unified Dashboard provides greater agility and enriches capabilities of dashboards. Users can visualize data from other applications at a central place and get a better understanding of data. <ud_module_picker.jpg>
Integration with VMDR
Unified Dashboard is integrated with VMDR for quick accessibility.
Users can leverage the default VMDR dashboard provided by Qualys or easily configure widgets to pull information from other modules/applications and add them to your dashboard. Users can also add multiple dashboards to customize the vulnerability posture view.
Web Application Scanning
Delete Catalog Entries
Qualys WAS now provides the capability to delete catalog data to eliminate old or obsolete entries that are not valid any longer.
Performance Improvements
The performance and responsiveness of the dashboard, detection list, and UI-based reports have been improved, resulting in faster page loading.
Expanded XML Report
The glossary section of XML web application reports has been expanded to include details for Burp issues that have been imported into WAS.