Qualys Windows Cloud Agent Update: Action needed to update DigiCert Trusted Root G4 certificate
Last updated on: August 28, 2023
Table of Contents
- Overview
- What Caused This Update
- What Functions Are Impacted
- Check the Digicert G4 Root Certificate Availability on the Asset
- Solution: Install the Certificate Manually
- How to Install the Certificate using Qualys Custom Assessment and Remediation
- How to Install the Certificate using Qualys Patch Management Follow These Steps (click to expand)
- How to Disable Auto-upgrade on Assets without DigiCert G4 Certificate Only (click to expand)
All public Certificate Authorities, including DigiCert are deprecating older root CA certificates to be compliant with evolving industry standards like Certification Authority Browser Forum. This blog explains the nature of this update, possible impacts, and how existing Qualys customers can remain in compliance. Multiple installations and update options exist, including using Qualys Cloud Platform services to address the need.
Update August 11, 2022 – Qualys has partnered with DigiCert to provide a solution that meets today’s security standards while also leveraging a certificate that is by default in the Windows Trusted Store. With the release of Windows Cloud Agent 4.9, the binary will require “DigiCert Assured ID Root CA” OR “DigiCert Trusted Root G4” to auto upgrade. This will allow the large majority of Windows Cloud Agents to upgrade to 4.9 preventing Patch Management and upgrade failures. Windows Cloud Agent 4.9 will be released in first half of September.
Update July 10, 2022 – Impacted Windows Cloud Agents will fail to upgrade and will continue to download the agent binary from the Qualys Cloud Platform causing unnecessary network usage. This will continue until the correct certificate is added. Qualys highly recommends disabling Auto-upgrade. Please see “How to Disable Auto-upgrade on Impacted Assets Only” for step-by-step instructions.
Update June 10, 2022 – Windows Cloud Agent version 4.8 will begin deployment toward the end of June 2022.
Update June 2, 2022 – Qualys has released Information Gathered QID 45535 “Required Certificate Not Present on Host for Windows Qualys Cloud Agent Version 4.8 and Later” in VULNSIGS-2.5.495-4 for Windows Cloud Agent only.
Overview
Starting May 28, 2021, DigiCert will require the code-signing certificate to be 3072-bit RSA keys or larger. DigiCert is one of the most trusted organizations that issues digital certificates for websites and other entities. This certificate change is required to be compliant with industry standards such as the Certification Authority Browser Forum, so IT organizations around the world are adopting it.
Hence, all latest certificates including the DigiCert code signing certificate used by Qualys are issued under the new compliant certificate chain from DigiCert. Qualys validates that the binary file downloaded from the Qualys Cloud Platform is code-signed with this new certificate. Checking the digital signature verifies that the file originated from Qualys and that it hasn’t been tampered with. Additionally, use of the timestamping service proves that the digital signing certificate was valid at the time of signing the binary, and that the certificate hasn’t been revoked.
Please refer to https://www.digicert.com/dc/code-signing/microsoft-authenticode.htm for more detailed information.
Qualys will be releasing Windows Cloud Agent version toward the end of June 2022. Digital signature validation of Qualys binaries may fail on some assets if those assets do not have the ‘DigiCert Trusted Root G4’ certificate in the Trusted root certification authority. Qualys strongly recommends installing the certificate by June 6, 2022, to avoid any potential impact.
What Caused This Update
DigiCert has provided a new certificate for timestamping that is signed by a different root certificate and has changed from what was used in previous Qualys Cloud Agent for Windows versions. The new CA name is ‘DigiCert Trusted Root G4’. The root certificate was released in 2013, therefore if you have enabled Windows Update at any point, you should have this certificate already.
Below, we provide steps to check the certificate using QID 45231, to install it manually, install it using Active Directory, install it on single assets, using PowerShell script, or using either Qualys Custom Assessment and Remediation or Qualys Patch Management.
What Functions Are Impacted
If DigiCert Trusted Root G4 is missing, the following Qualys functions will return errors:
- Patch Management – The status of patches will be displayed as “Failed” on the Patch Management UI as the patch service will fail to validate the digital signature of statusHandler.dll and will log the following error in the log file (C:\ProgramData\Qualys\QualysAgent\Log.txt):
Error: Patch: Failed to validate the signature of PE binary file…statusHandler.dll’, ensure that the ‘DigiCert Trusted Root G4’ certificate is available in the Trusted root certification authority.
- Auto Upgrade / Self-Patch of Windows agent – During self-patch, the new version of the binary is downloaded, and the upgrade is initiated. Before initializing, as a part of integrity verification, the binary’s digital signature is validated. If the DigiCert Trusted Root G4 certificate is not available, the digital signature validation fails, and the self-patch process is aborted. You will see the following two errors in the log file (C:\ProgramData\Qualys\QualysAgent\Log.txt):
Error: Setup file “C:\ProgramData\Qualys\QualysAgent\SelfPatch\f959b30c-3bd8-46a2-a67d-f99b96c58f95.exe” did not pass necessary security checks: (win32 code: -2146869243), “The timestamp signature and/or certificate could not be verified or is malformed.”
Error: SelfPatch has failed: (win32 code: -2146869243), “The timestamp signature and/or certificate could not be verified or is malformed.”
Check the Digicert G4 Root Certificate Availability on the Asset
Using Qualys
Primary Method
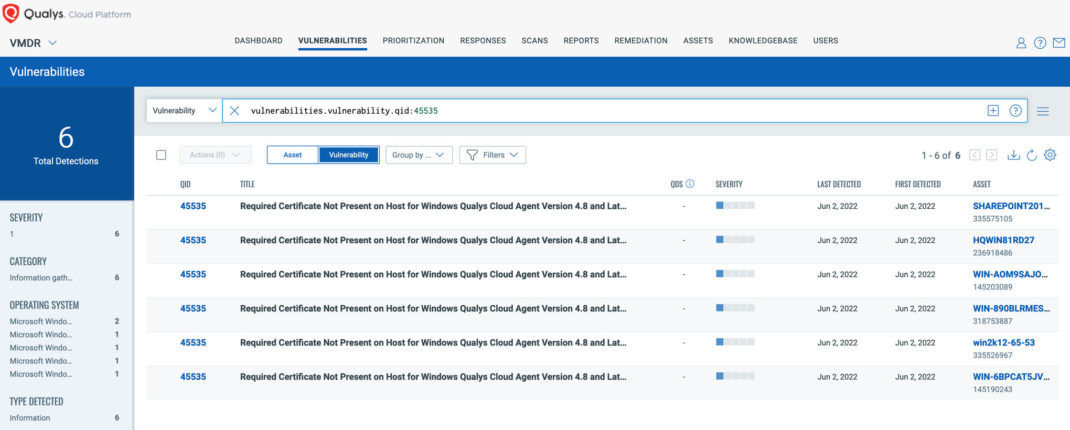
To quickly discover impacted assets, Qualys has released Information Gathered QID 45535 “Required Certificate Not Present on Host for Windows Qualys Cloud Agent Version 4.8 and Later” on June 2, 2022 in VULNSIGS-2.5.495-4 for Windows Cloud Agent only.
Information Gathered QID: 45535 Required Certificate Not Present on Host for Windows Qualys Cloud Agent Version 4.8 and Later
Vulnerability Signature package: VULNSIGS-2.5.495-4 and later
Secondary Method
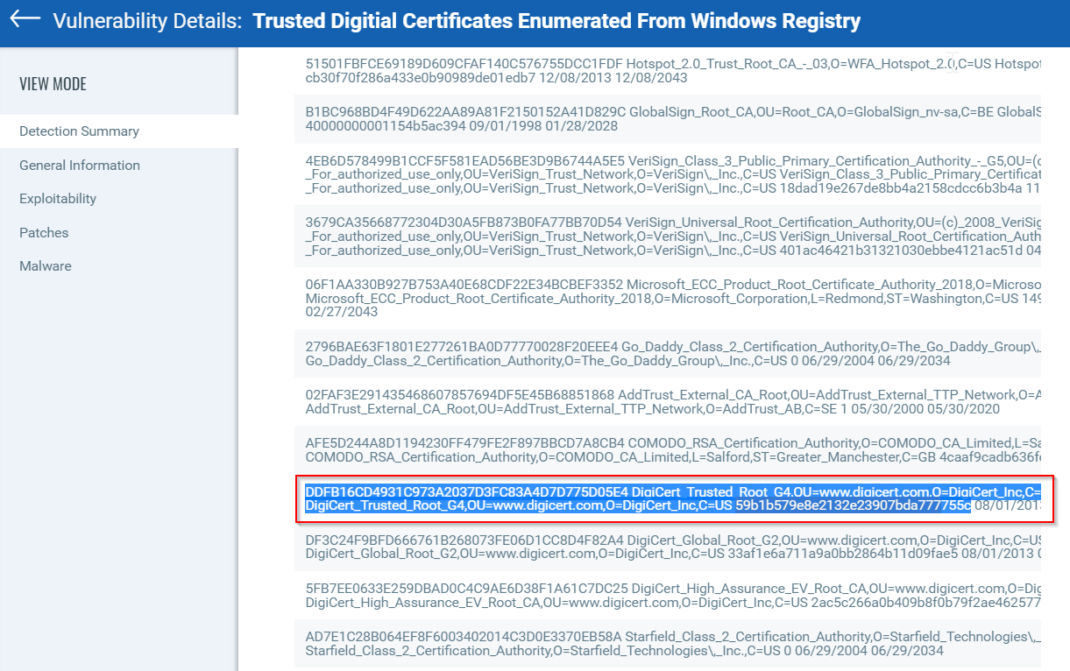
You can use information gathered by QID:45231 (‘Trusted Digital Certificates Enumerated From Windows Registry’) to check for the presence of the DigiCert G4 certificate. Please check for the following Serial Number and Thumbprint in the QID results section:
Serial Number: 59b1b579e8e2132e23907bda777755c
Thumbprint: DDFB16CD4931C973A2037D3FC83A4D7D775D05E4
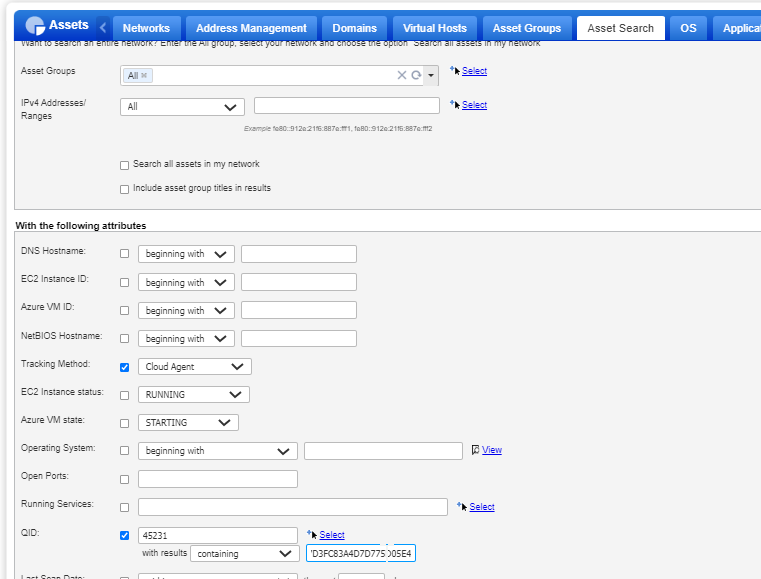
You may also search results for QID 45231 with results containing DDFB16CD4931C973A2037D3FC83A4D7D775D05E4 on “All” Asset group using Asset Search in VM module:
Directly on the Asset
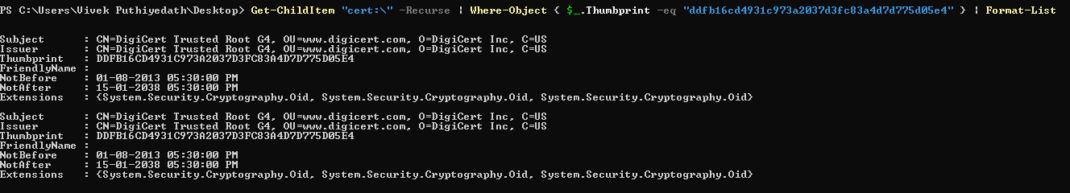
Use the following command to check whether the certificate is available on the asset:
Get-ChildItem “cert:\” -Recurse | Where-Object { $_.Thumbprint -eq “ddfb16cd4931c973a2037d3fc83a4d7d775d05e4” } | Format-List
Please Note: PowerShell version required is 2.0 or later.
- If the certificate is available, you will see DDFB16CD4931C973A2037D3FC83A4D7D775D05E4 in the Thumbprint section of the output
- If the certificate is not available, the output will be empty.
Solution: Install the Certificate Manually
If the required certificate is not available on the asset, you can install the certificate manually. Use one of the following ways to install/update the certificate on the asset:
- Using Active Directory: To update the certificate using Active Directory, follow the procedure detailed in Distribute Certificates to Client Computers by Using Group Policy using the certificate link.
- Manual update: If you are connected to the internet, use the following command to update the certificate manually:
certutil -urlcache -f http://cacerts.digicert.com/DigiCertTrustedRootG4.crt DigiCertTrustedRootG4.crt
certutil -addstore -f root DigiCertTrustedRootG4.crt
You can download the DigiCert Trusted Root G4 and add the certificate to the certificate store using the following command:
certutil -addstore -f root <downloaded cert path>
Option 1: To Update Certificate Manually – Follow These Steps (Click to expand)
1. Visit Digicert and download DigiCert Trusted Root G4.
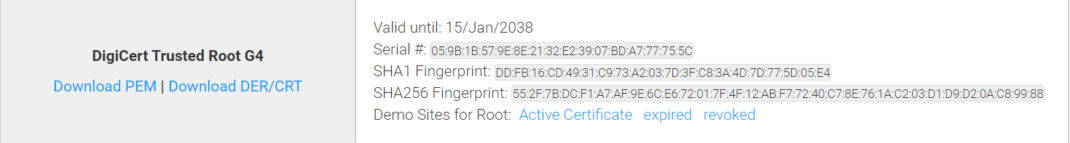
2. Open the downloaded file and click Install certificate.
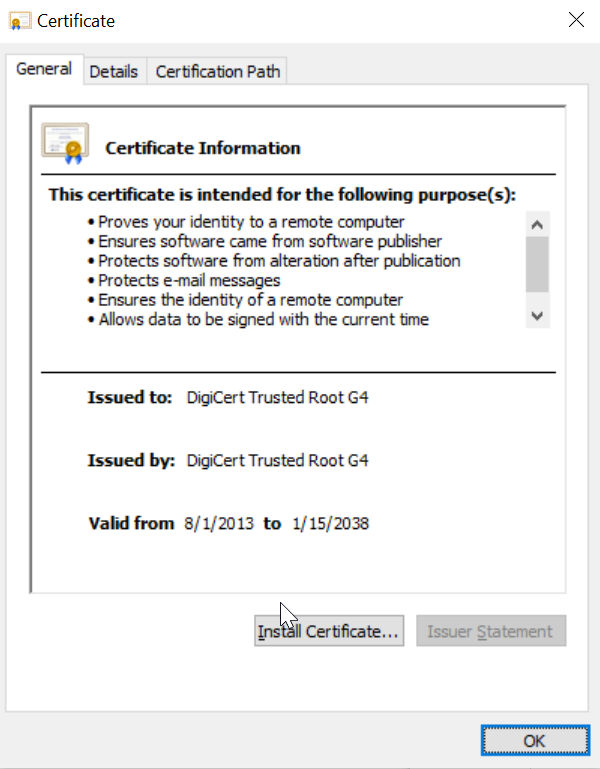
3. Select Local Machine and click Next.
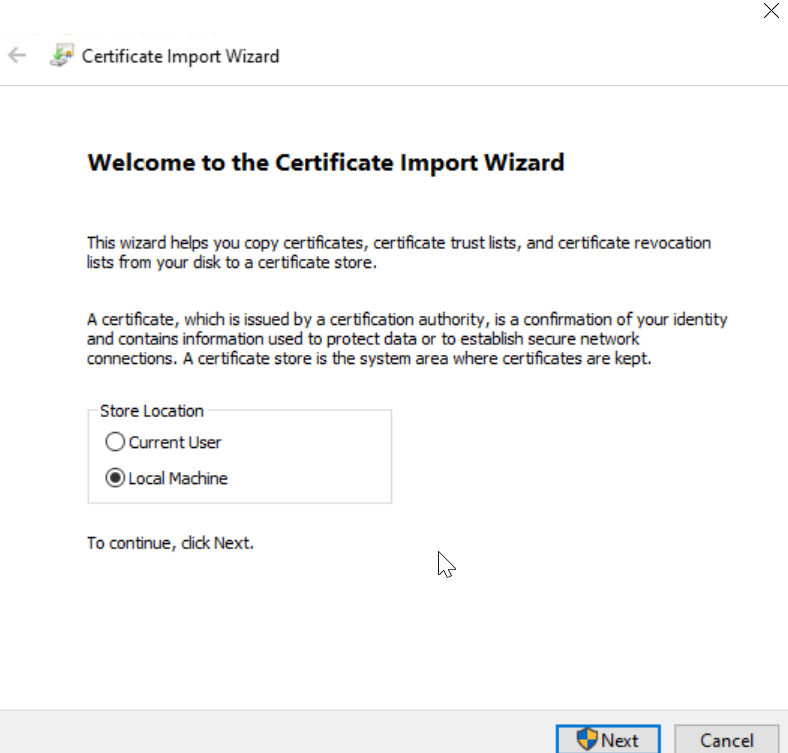
4. Select the option “Place all certificates in the following store” and click Browse.
5. Select Trusted Root Certificate Authorities and click OK.
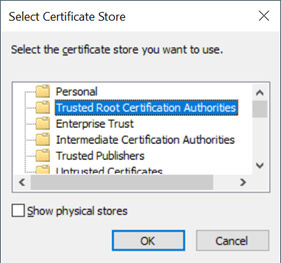
6. Click Next.
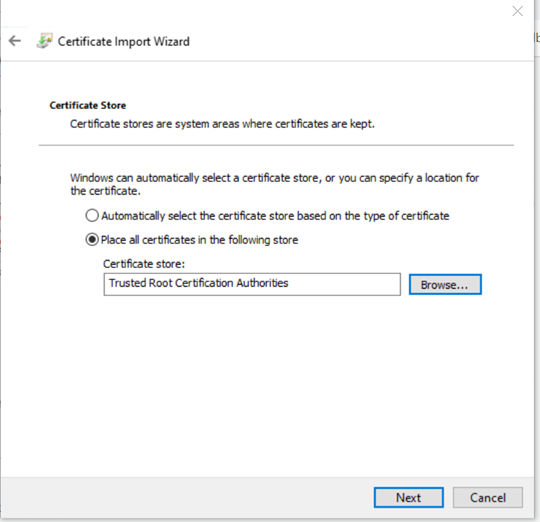
7. Click Finish.
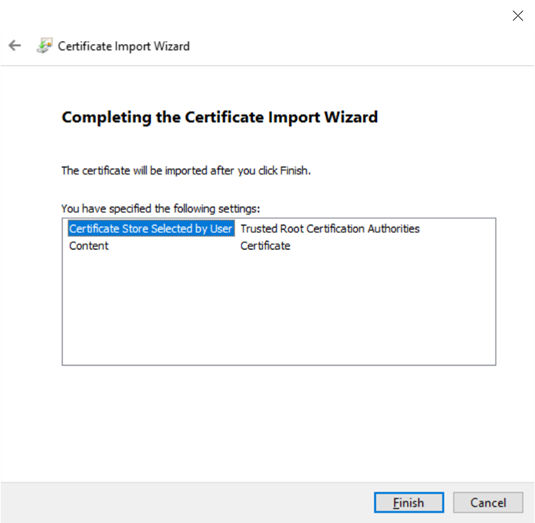
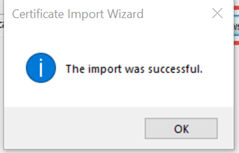
8. The Root certificate is installed.
Option 2: Install the Certificate using PowerShell Script
Qualys has also added a PowerShell script on https://github.com/Qualys/DigiCertUpdate that can be utilized to add the ‘DigiCert Trusted Root G4’ certificate to the Trusted Root Certification Authorities of the machine. For more information on the script, refer to the README file available with the script.
Option 3: Install the Certificates Automatically with Qualys
You can automate the certificate installation using either of the two Qualys cloud services:
- Qualys Custom Assessment and Remediation
- Qualys Patch Management
How to Install the Certificate using Qualys Custom Assessment and Remediation
You can use the PowerShell script “DigiCertUpdate” posted on the Qualys GitHub account to check the availability of the certificate and install the ‘DigiCert Trusted Root G4’ certificate on your scope of assets by using Qualys Custom Assessment and Remediation.
The following screen indicates where you can select an out-of-the-box script in the application.
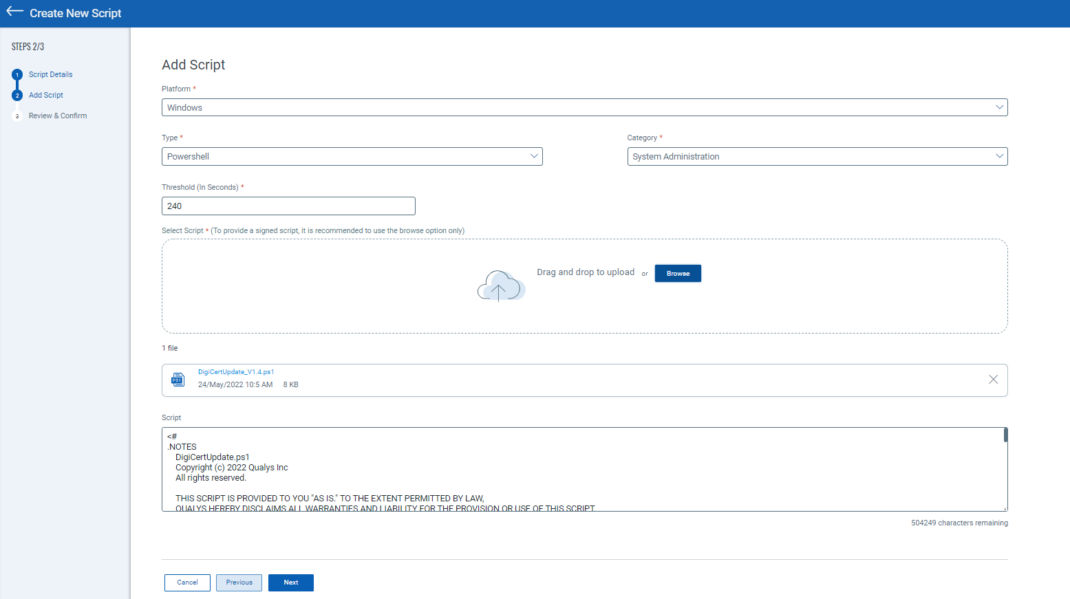
Modifying the script: If you want to add a certificate path in the script, edit the default values of the argument.
For example,
[string]$CertPath = ” C:\Users\DigiCertTrustedRootG4.crt”,
Or
[string]$CertPath = ” \\10.115.105.222\Share\DigiCertTrustedRootG4.crt”,
If you want to add a proxy setting in the script, you can edit the default values of the argument.
For example,
[string]$ProxyAddress = “10.115.27.54”,
[int]$ProxyPort = 3128,
Free Trial
Get started with a 30-day Free Trial
How to Install the Certificate using Qualys Patch Management – Follow These Steps (click to expand)
- Go to Qualys Patch Management portal, select Jobs tab.
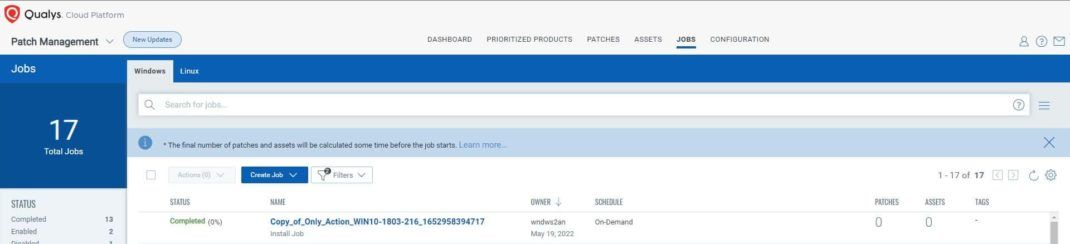
- Click Create Job and select Deployment Job.
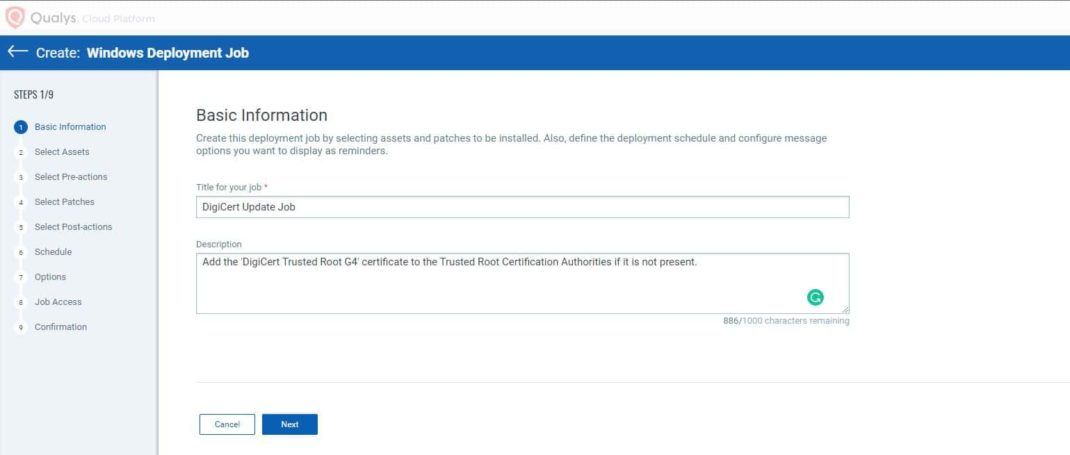
- Add Basic Information related to the job.
- Select Assets and click Next.
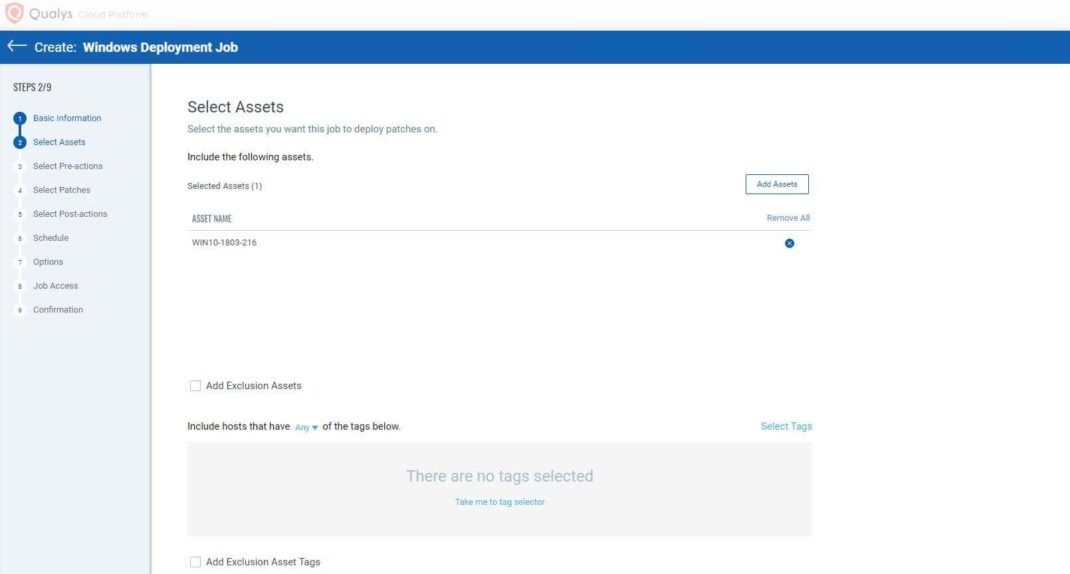
- Add Pre-Actions. Select action as Run Script. Give the action a name. Add the script to the custom script. If you want to add the parameters, modify the default parameters in the script. Click Add, then click Next.
Script link: https://github.com/Qualys/DigiCertUpdate
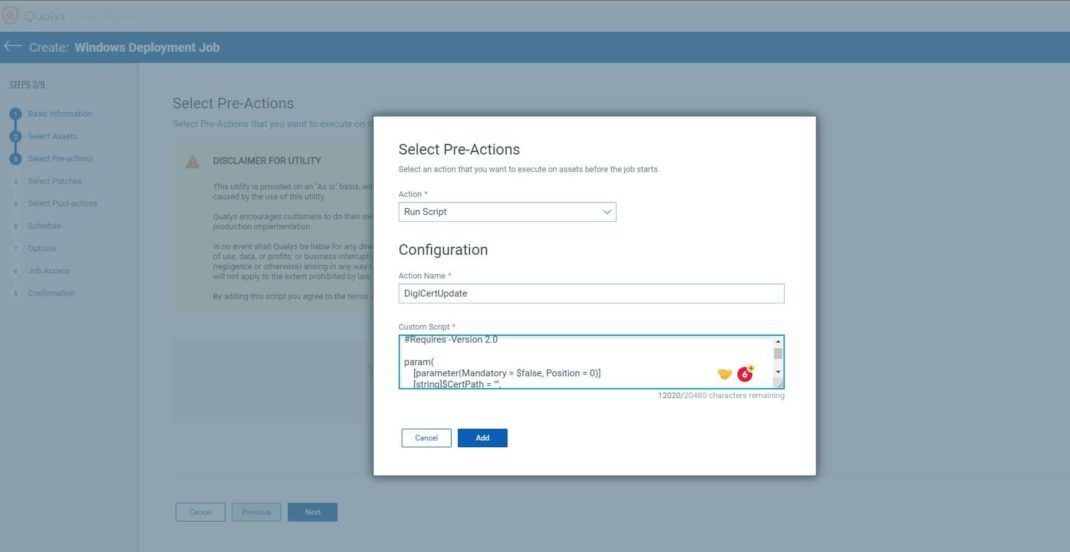
- Select Manual Patch download and click Next.
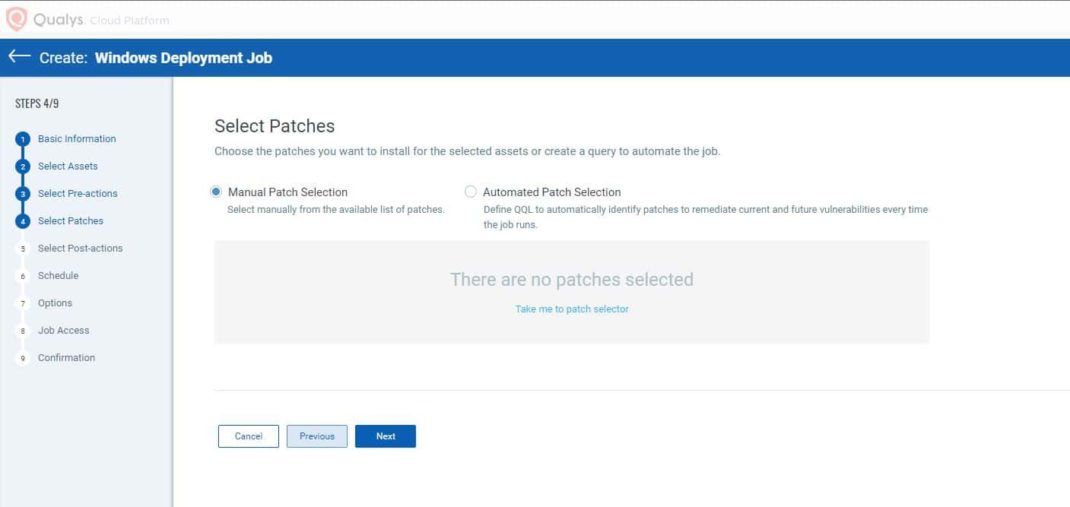
- Skip Post-Actions. Click Next.
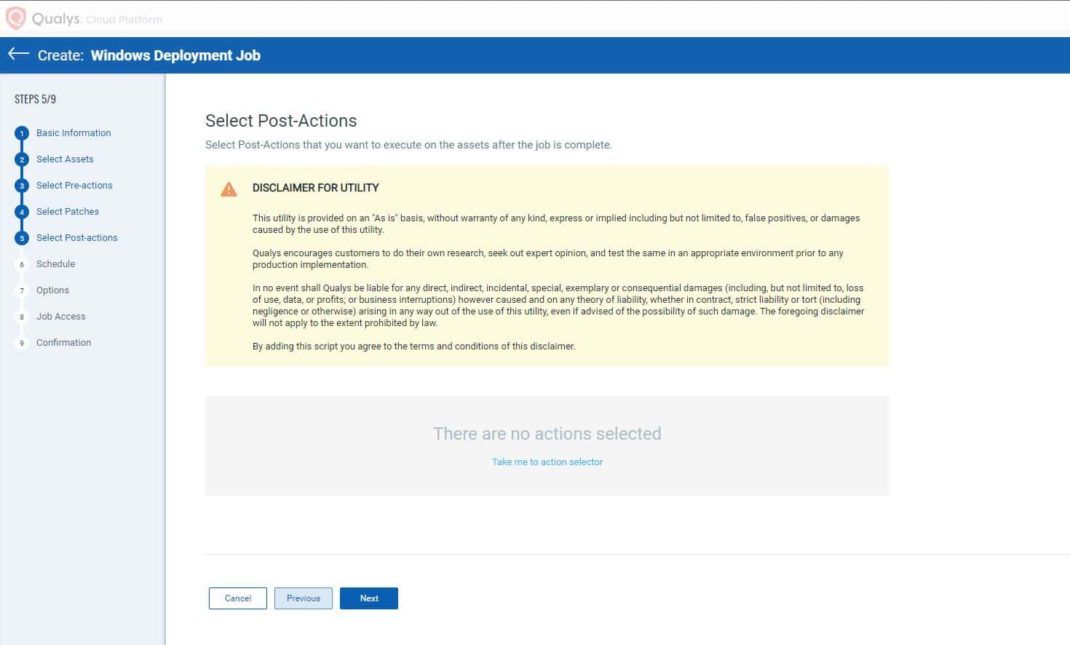
- Select On Demand from Schedule Deployment and select “None” as the Patch Window. Click Next.
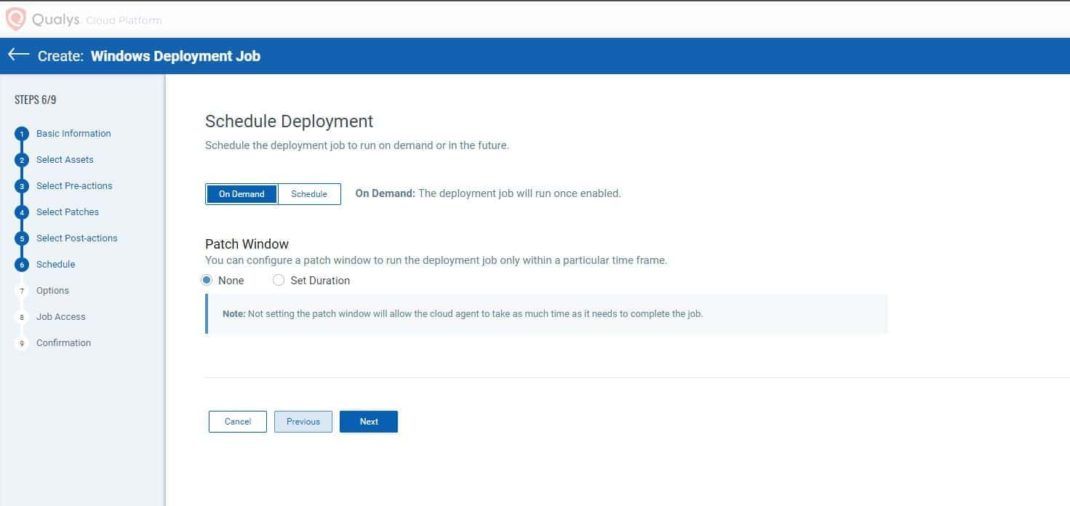
- Keep the Deployment Message options as shown in the below image. Click Next.
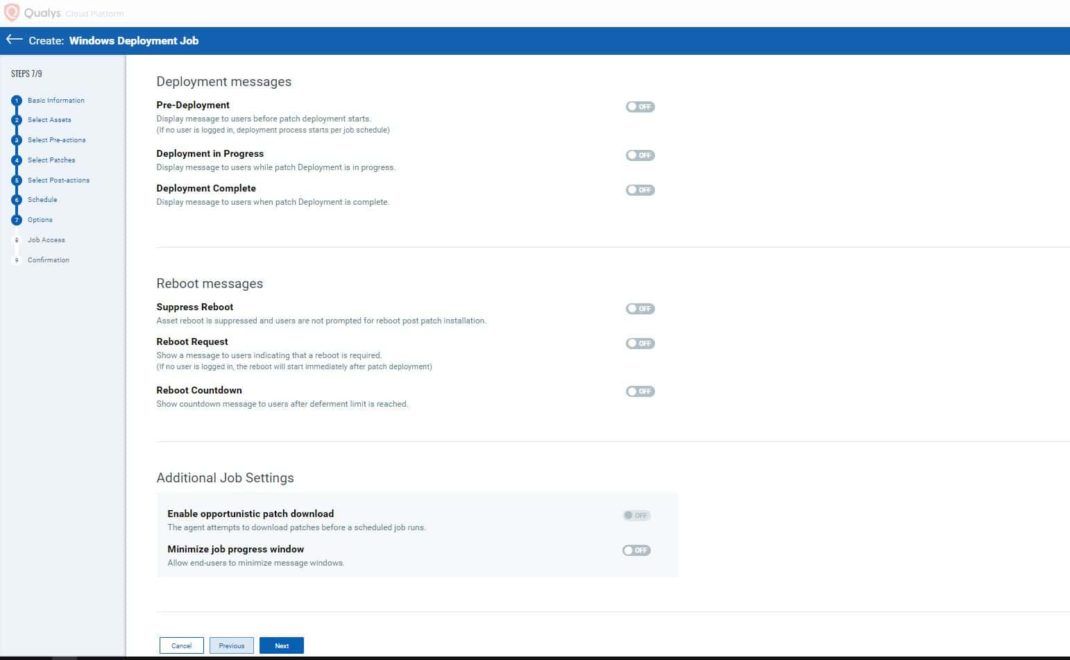
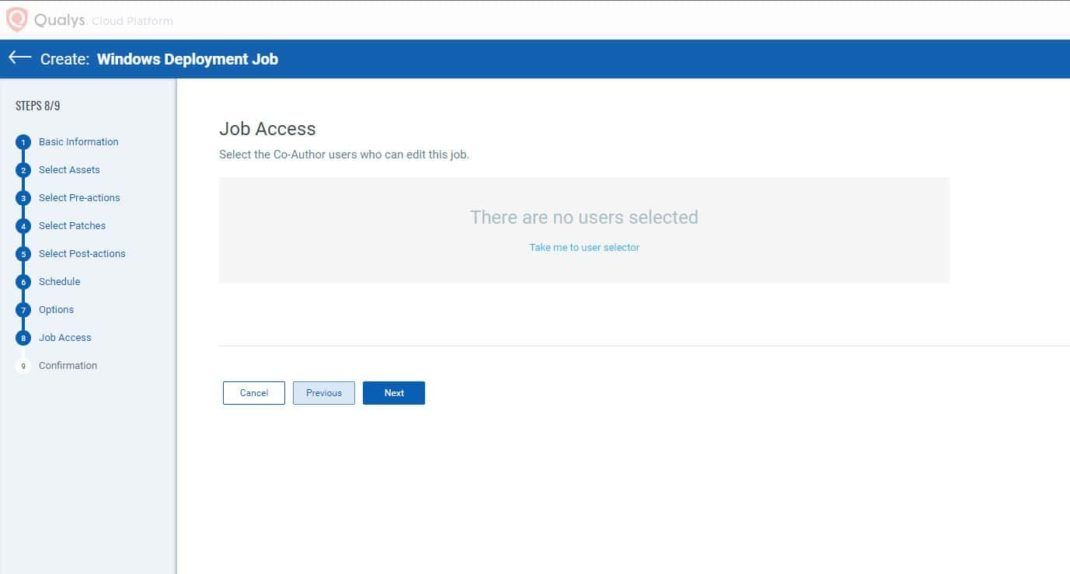
- If you want to provide Job Access to some other users, add the user details. Click Next.
- From the Confirmation page, verify all the details are correct and select “Save & Enable” from the Save options.
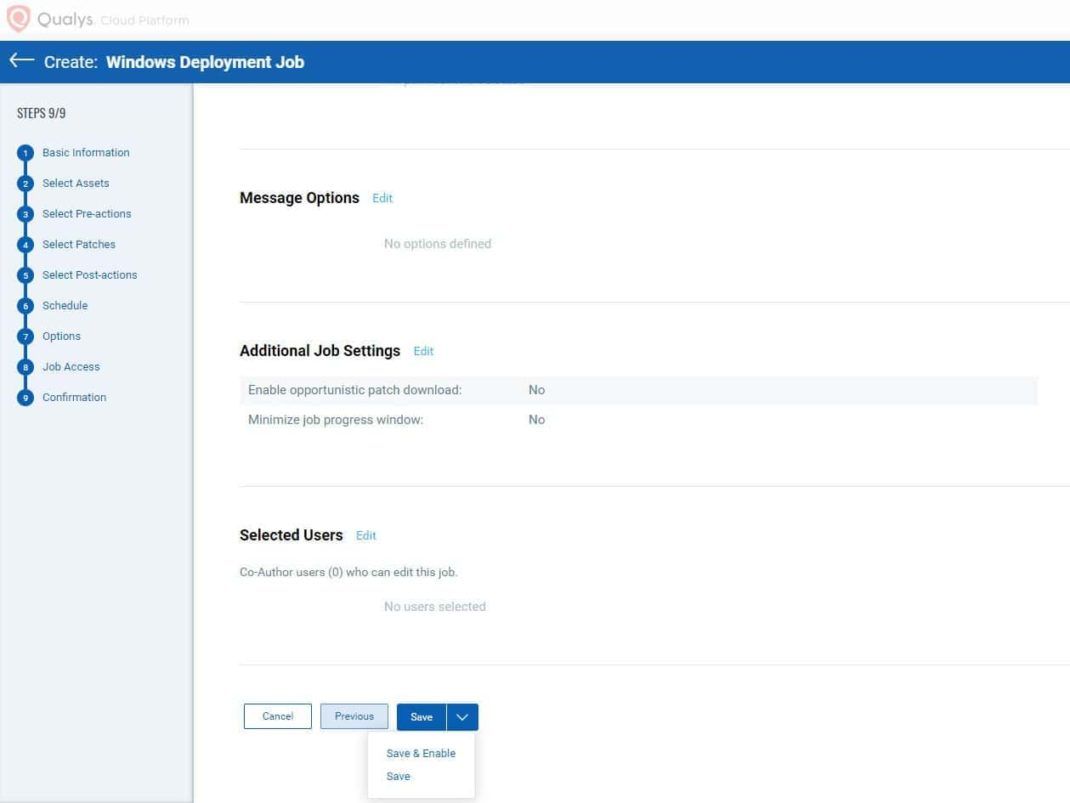
- The patch job will execute. Wait for the successful completion of the job.
* Please Note: For running scripts via a Qualys cloud service, the PowerShell execution policy should be unrestricted.
How to Disable Auto-upgrade on Assets without DigiCert G4 Certificate Only (click to expand)
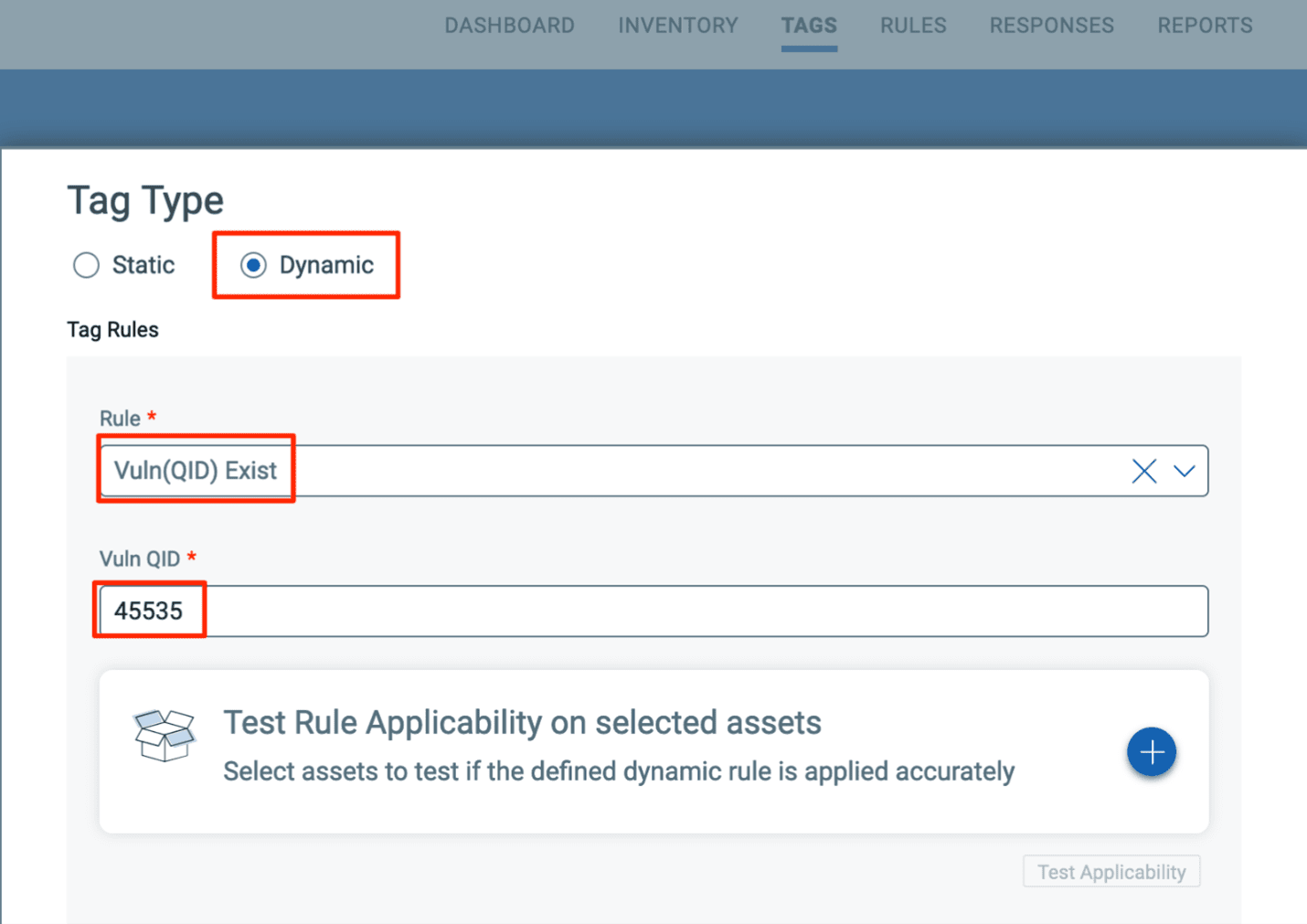
Create Dynamic Tag
In Global AssetView > Tags > Create Tag
Name: Required Certificate Not Present on Host for Windows Qualys Cloud Agent Version 4.8 and Later
Tag Type: Dynamic
Rule: Vuln(QID) Exist
Vuln QID: 45535
Assign Tag to Agent Configuration Profile
In Cloud Agent > Agent Management > Configuration Profile > New Profile > Assign Hosts
Select tag created from Create Dynamic Tag step
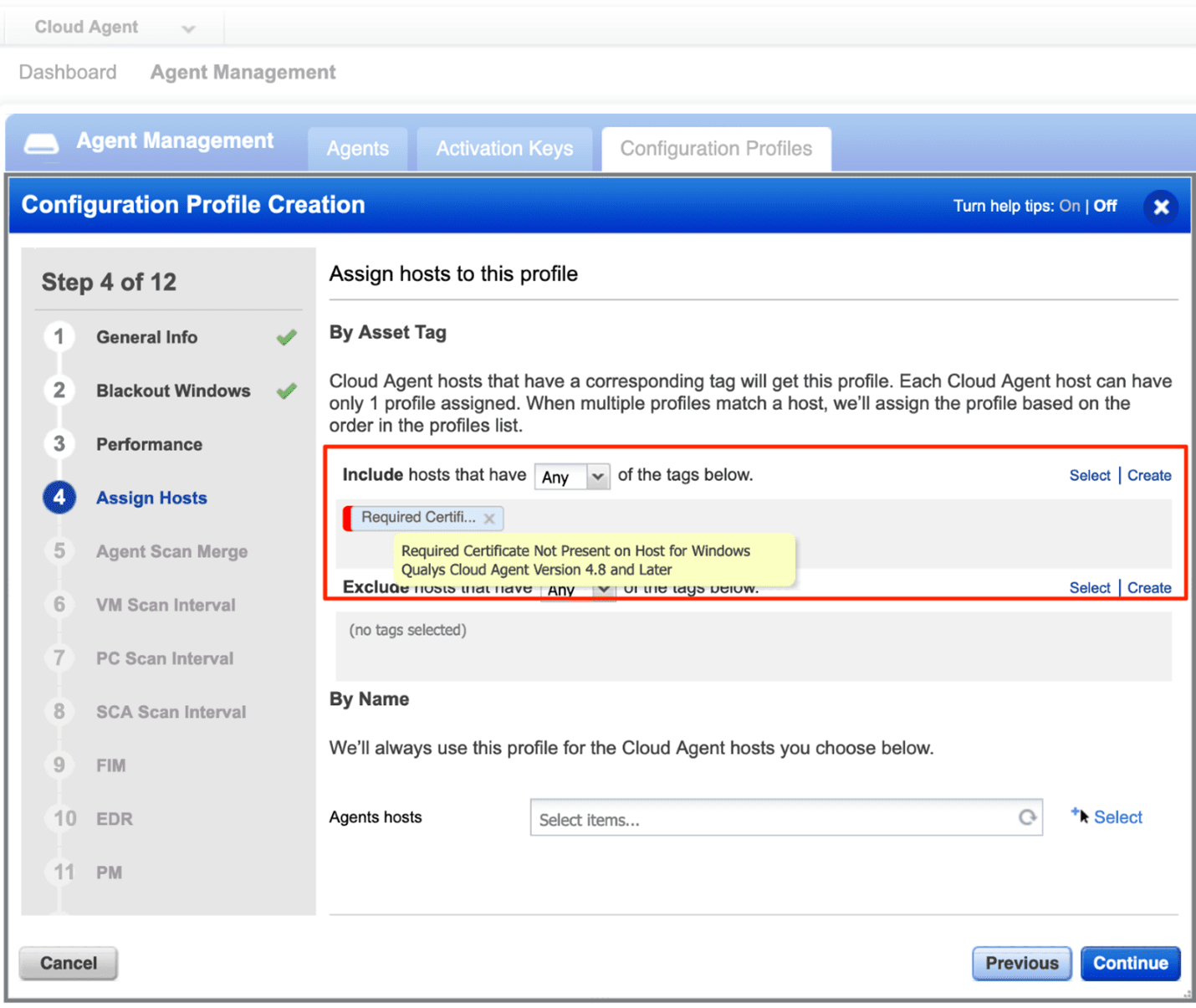
Note: Configuration Profiles are applied in the order in which they are ranked. Ensure this Configuration Profile is at the top.
Qualys customers can contact their Technical Account Manager or Qualys Support for further assistance.
“Starting May 28, 2021” – is this a typeo? should it be 2022?
I agree Darryl the wording is a little misleading, with the word “will” suggesting that this is something yet to happen.
Given this blog was written in 2022, i would expect it to read “Beginning May 28, 2021, DigiCert required the code-signing…..”, dropping the word “will”…..
https://knowledge.digicert.com/alerts/code-signing-new-minimum-rsa-keysize.html