What’s new in QScanner v4.5.0?
We’re excited to announce that QScanner v4.5.0 will be released soon, bringing with it significant performance improvements and deeper visibility into your container images.
This latest version is designed to be faster and more efficient, helping you scan large image sets with even greater speed. We’ve also enhanced data collection for Go and Java-based images, ensuring more accurate detection of packages, libraries, and vulnerabilities across these ecosystems.
In this blog, we will be covering the major additions to this release.
Support for Secret Scan
We’re excited to announce a powerful new feature in the QScanner: Secret Scanning. This feature is now available to help you discover and remediate sensitive secrets embedded in your container images before they reach production.
Why Secret Scanning Matters
Containerized applications often package more than just code. They can inadvertently include sensitive secrets like:
- API keys
- Passwords
- Cloud credentials
- Private certificates
- Tokens or encryption keys
These secrets pose a critical security risk. If exposed, attackers could gain unauthorized access to infrastructure, data, or services, resulting in breaches, downtime, and compliance violations.
How Qualys Secret Scanning Works
Secret scanning in Qualys is designed to detect these risks before they’re exploited. Here’s how it works:
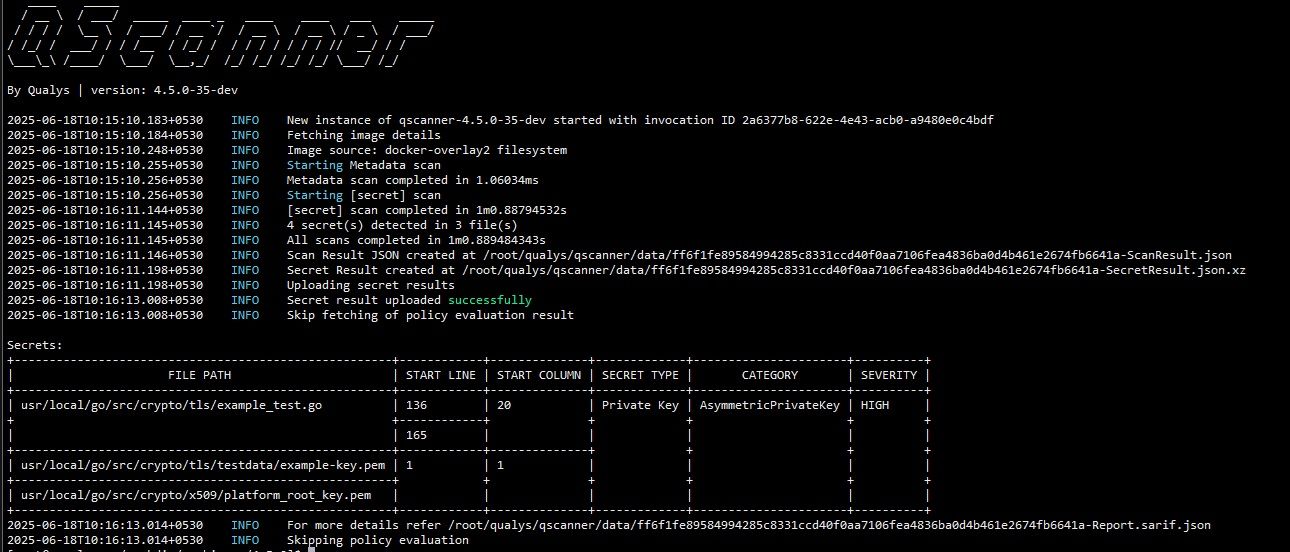
- Filesystem-Based Detection
The scanner inspects the file system of your container image for embedded secrets. It does not rely on environment variables or runtime data, ensuring thorough static analysis. - Comprehensive Rule Set
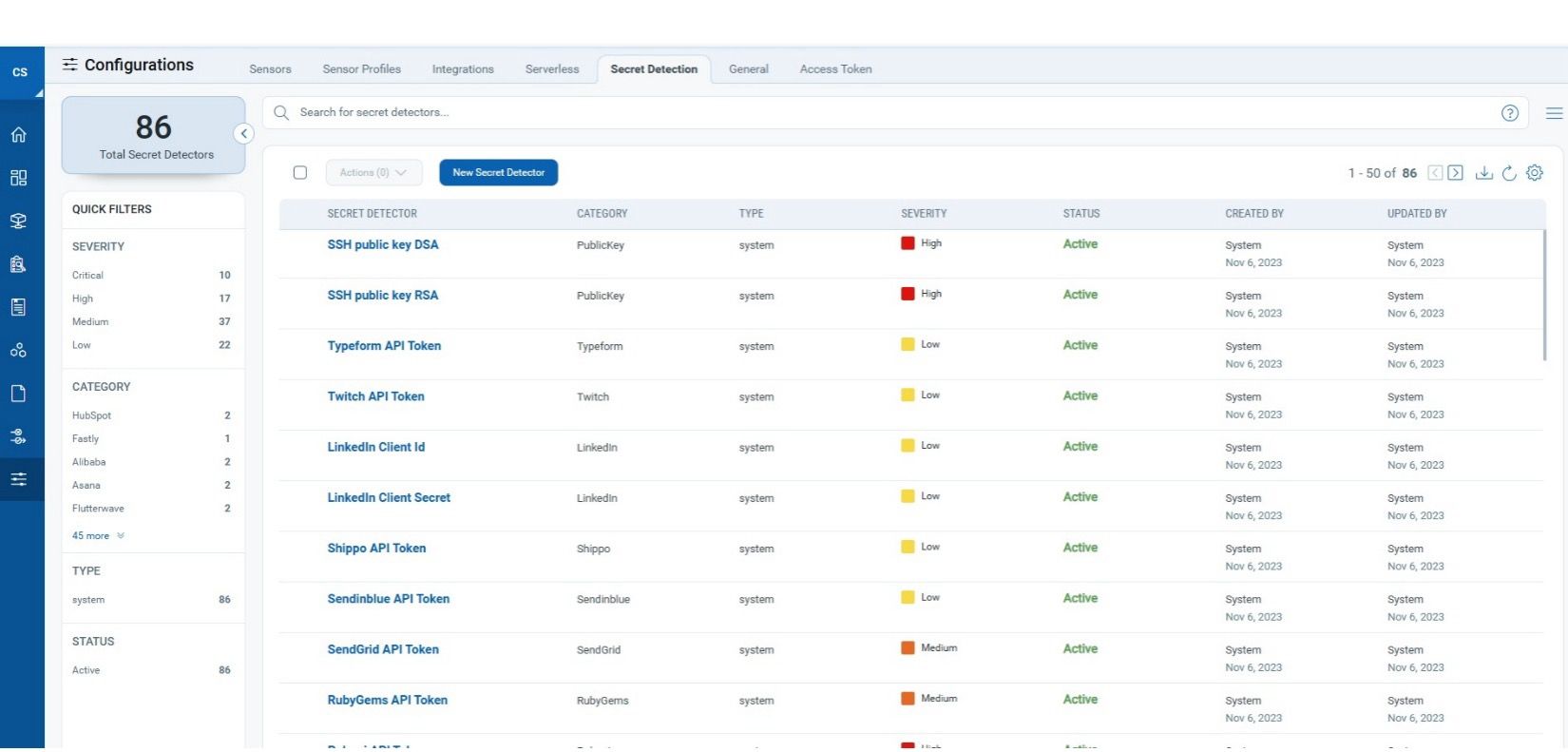
- Out-of-the-box, we include 85+ curated System Secret Detectors that use finely-tuned regular expressions to catch a wide variety of secrets, from AWS keys to database passwords.
- QScanner automatically downloads this secret configuration from the Qualys backend and uses it to scan your container images.
- Want more control? Define custom secret detectors using your own patterns to tailor detection to your environment.
- Flexible Configuration
Secret scanning can be enabled by simply adding the secret option to –scan-types flag of QScanner (–scan-types pkg,secret will scan for OS+SCA packages and secrets). Whether you’re scanning from a registry or within CI/CD pipelines, this feature fits seamlessly into your workflow. - Optimized for Performance
Secret scanning is an expensive operation. QScanner works best when provided with two or more CPUs. With this release, QScanner also makes use of local cache by default, i.e, cache local. If secret data for a layer with the given secret configuration already exists in cache, it avoids rescan of that layer.
Viewing and Acting on Results
Once secrets are detected, you can view them directly on the console.
All this is aimed at giving your teams early visibility and faster remediation of credential exposures.
Real Security Gains
By integrating secret scanning into your container workflows, you can:
- Shift left on security: catch secrets during development and CI/CD.
- Prevent leaks: avoid pushing vulnerable images into registries.
- Improve compliance: ensure no sensitive information makes it into production.
- Reduce risk: actionable findings make it easy to fix what matters most.
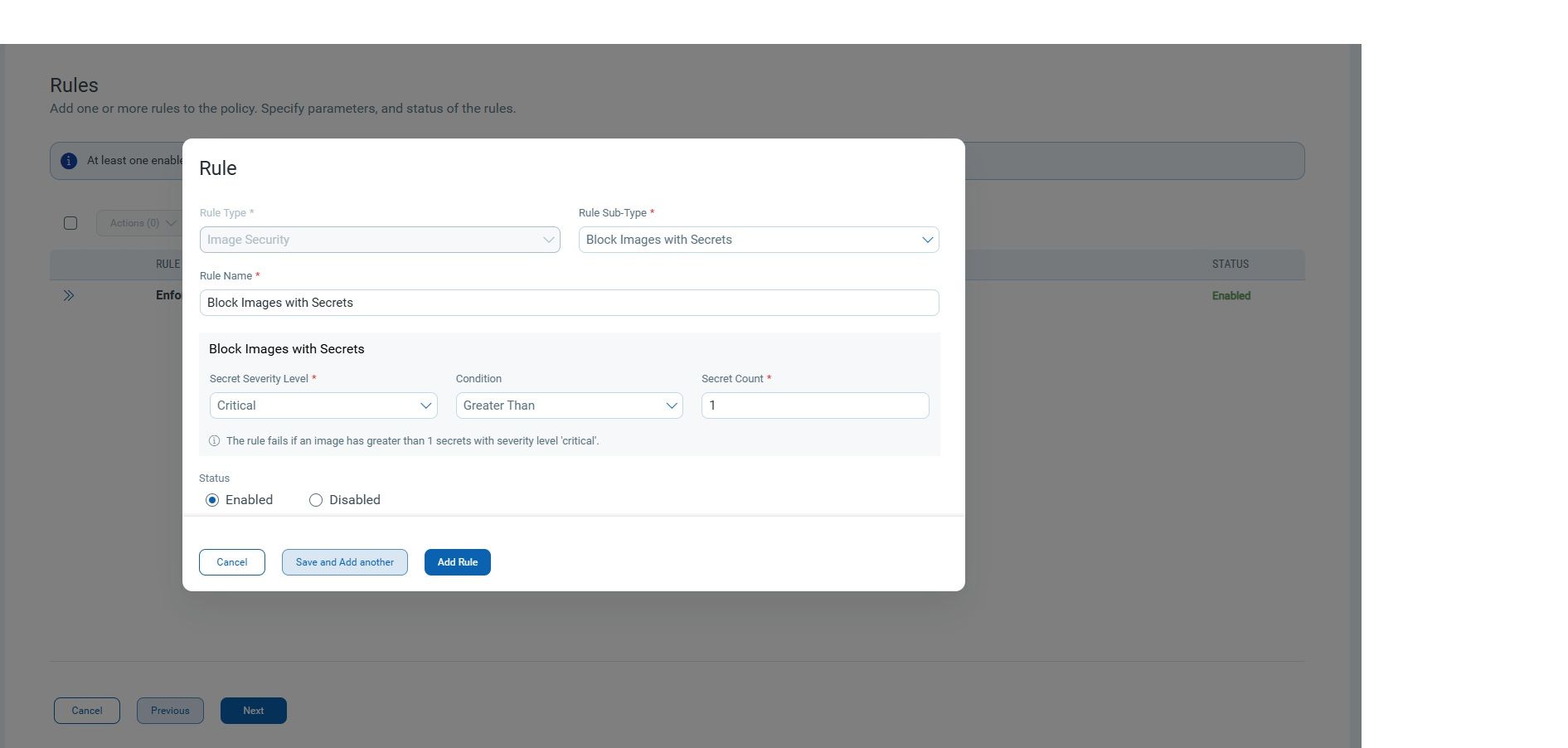
Policy evaluation on detected secrets
You can also leverage the centralized policy evaluation engine.
- Define security policies that explicitly disallow container images containing hardcoded secrets.
- Automatically evaluate every image scan result against your defined policies.
- Fail builds or block promotions of non-compliant images in CI/CD pipelines or registries.
- Prioritize remediation based on severity, type of secret, or custom business logic.
By combining Secret Detection with Policy Evaluation, QScanner empowers teams to go beyond visibility and build truly secure and compliant container pipelines — by design, not by accident.
Streamlined Vulnerability Reporting: Cleaner, Sharper, and More Actionable
As part of our continuous effort to improve clarity and prioritization in vulnerability management, we’ve rolled out a refreshed report format in QScanner that makes it easier for teams to focus on what truly matters — fixing the right vulnerabilities, faster.
What’s changed?
QDS (Qualys Detection Score) replaces “Severity”
Severity values (e.g., 1–5 or Low/Medium/High) often lacked the precision needed to prioritize effectively. The new QDS field provides a more contextual and intelligent risk score — factoring in exploitability, asset context, CVE maturity, and real-world threat signals.
Why it matters: QDS helps cut through the noise. Focus on vulnerabilities that pose the highest risk, not just the highest CVE score.
Vulnerability Age
Knowing how long a vulnerability has existed in an image can be critical for both risk assessment and compliance.
Why it matters: A critical flaw that’s been present for 6+ months is more urgent than one introduced yesterday. Age helps drive time-aware remediation strategies.
Removed Columns: Severity and Layer SHA
To simplify the report and avoid overloading the view with low-action-value data, we’ve removed:
- Severity: Replaced by QDS, which is more dynamic and meaningful.
- Layer SHA: While technically useful, it’s been de-prioritized in favor of actionable fields.
Both of these parameters will still be available in the JSON and SARIF reports.
Designed for Actionability
The redesigned report aligns with how modern DevSecOps teams operate:
- Focus on vulnerable software (not just the CVEs).
- Prioritize based on real-world risk (via QDS).
- Track exposure over time (via Vulnerability Age).
- Drive faster remediation, especially in CI/CD pipelines.
This format is more readable, scalable, and aligned to risk-based remediation — whether you’re scanning a handful of images or managing an enterprise-scale container fleet.
Introducing QDS threshold: Filter Vulnerabilities by Risk Score
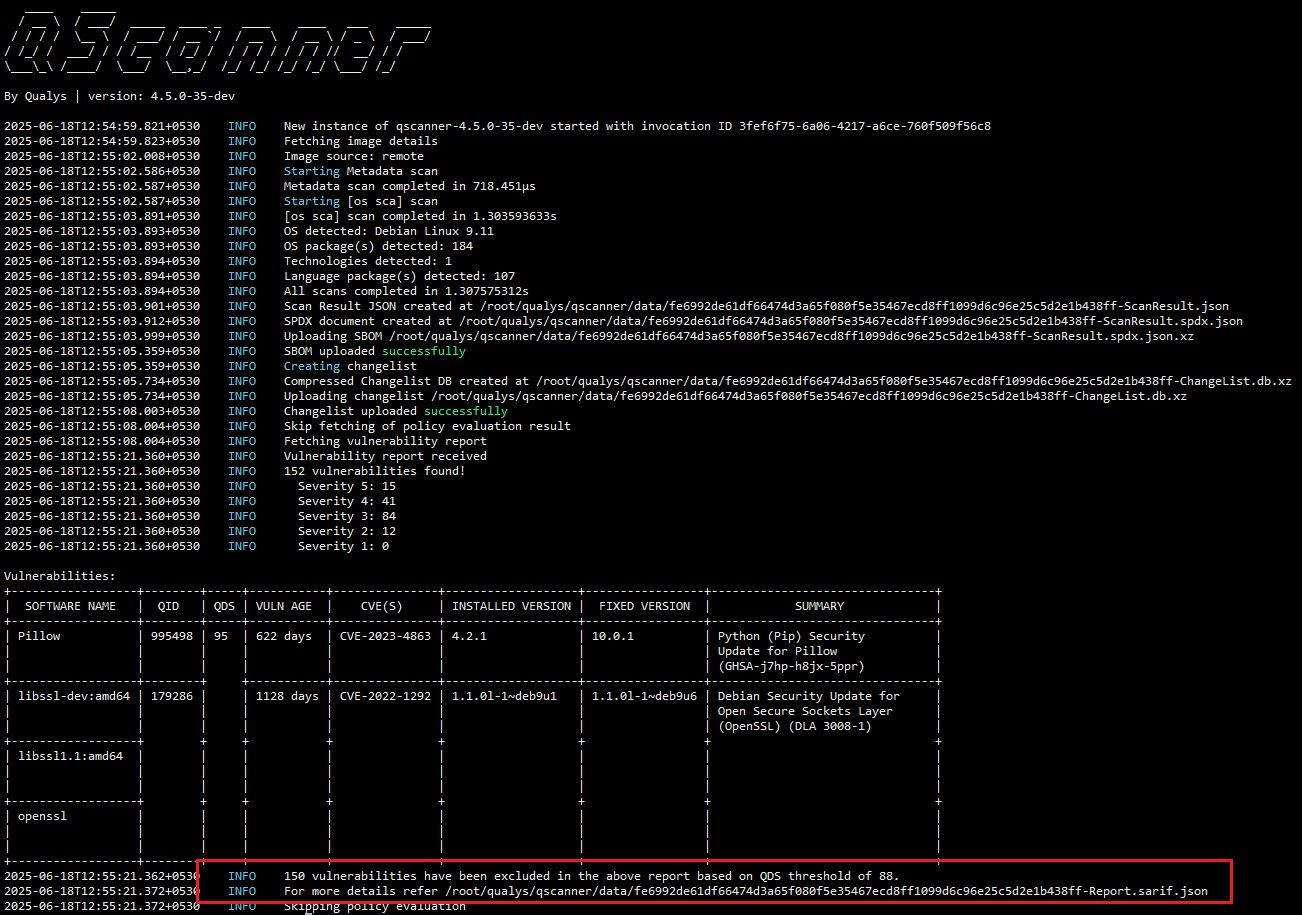
To help teams focus even more precisely on high-risk vulnerabilities, we’ve introduced a powerful new flag in QScanner: –qds-threshold
This flag allows users to filter the vulnerabilities shown in the tabular report based on their Qualys Detection Score (QDS), our intelligent, context-aware risk scoring system.
How It Works?
When you specify a QDS threshold using this flag –qds-threshold 88.
Only vulnerabilities with a QDS > 88 will be included in the final tabular report output. This is especially useful for:
- Reducing noise in reports during triage
- Prioritizing remediation based on real risk
- Aligning with internal security SLAs or gating policies
- Streamlining CI/CD decisions by focusing on critical findings only
By combining the QDS-based scoring with the –qds-threshold flag, you now have a highly targeted, risk-centric approach to vulnerability reporting and remediation.
NOTE: Please note that this filter is only applicable for tabular report and will not impact the results of centralized policy evaluation in any way.
For more details on QDS, please refer to TruRisk Score and QDS in Container Security.
How to Get Started
- Learn more about QScanner: https://docs.qualys.com/en/qscanner/release-notes/qscanner/qscanner_introduction.htm
- Try QScanner for free: https://www.qualys.com/forms/container-security/qscanner/
- Download QScanner: https://www.qualys.com/downloads/qscanner/
- Check out the latest blog on QScanner: https://blog.qualys.com/product-tech/2024/11/07/elevate-your-container-security-with-qscanner-in-2025
- Get online help: https://docs.qualys.com/en/qscanner/latest/get_started/get_started.htm
- Speak to an expert about Kubernetes & Containers Security: https://www.qualys.com/forms/totalcloud/