Qualys Cloud Suite 8.3 New Features
This new release of the Qualys Cloud Suite includes multiple improvements to Vulnerability Management and Policy Compliance.
Feature Highlights
- Qualys Cloud Platform Updates
- New Getting Started Tutorials
- Forgot Password Workflow
- Expired Password Options
- Ability to Delete Empty Networks
- Cisco IOS Authentication – Support for Cyber-Ark PIM Suite Vaults
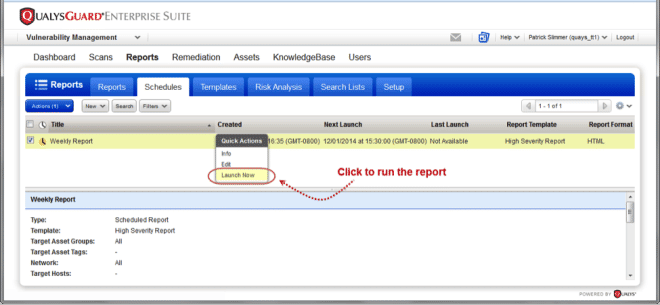
- Run Scheduled Reports on Demand
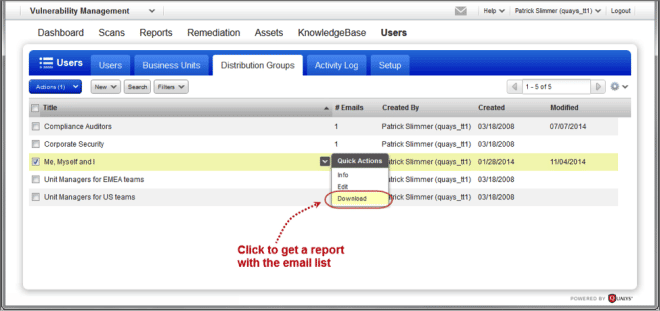
- Download Email List from Distribution Group
- General UI Improvements
- New Authentication Vault API
- Vulnerability Management (VM) Updates
- Policy Compliance (PC) Updates
Qualys Cloud Suite 8.3 will be released in production in the coming weeks and includes enhancements to Vulnerability Management (VM) and Policy Compliance (PC), the Qualys Cloud Platform and the API.
For release notifications containing details specific to each platform, including the release date, and to subscribe to release notifications for your platform, please see the following:
- US Platform 1 Release Notification
- US Platform 2 Release Notification
- EU Platform Release Notification
Qualys Cloud Platform Updates
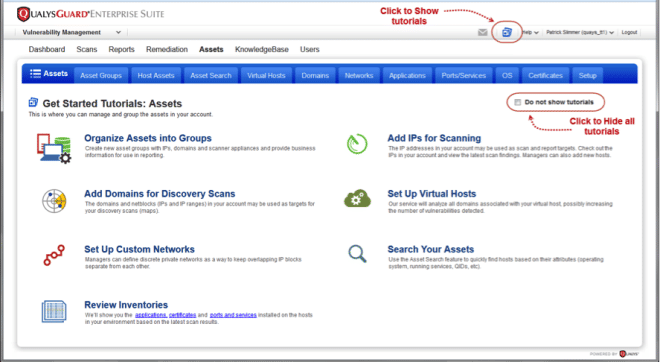
New Getting Started Tutorials: You’ll see Get Started Tutorials as you navigate the main sections of the UI – Scans, Reports, Assets, Users, etc. These appear in VM and PC to help guide you and provide shortcuts.
Here are a few examples:
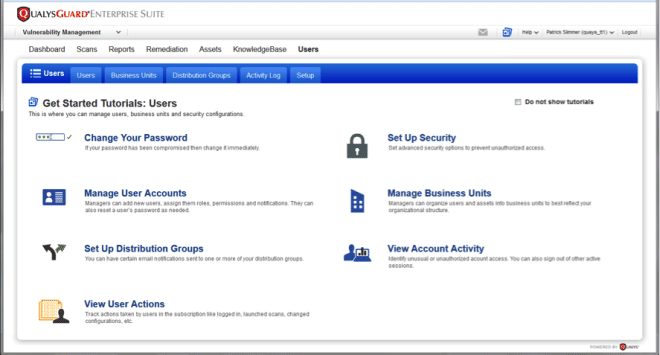
Here is a look at the Users section:
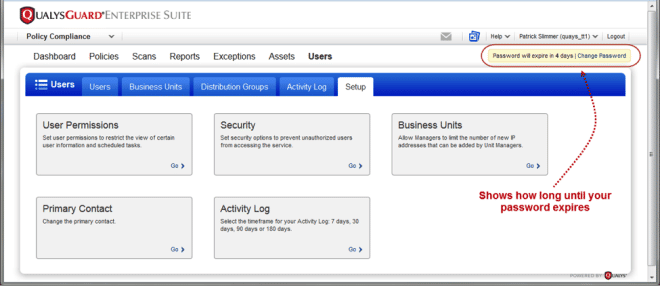
Forgot Password Workflow: Can’t remember your password? No problem. We’ll help you get a new password in just a few steps. Simply click the Forgot Password link, give us your email address and follow the instructions.
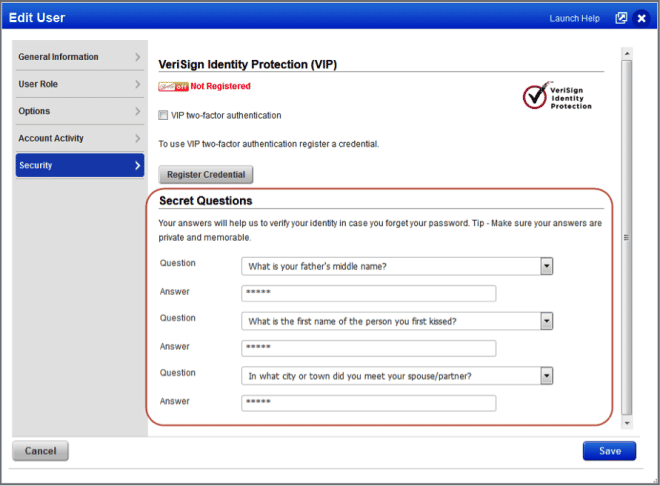
This release introduces secret questions to help you when you forget your password. Go to the Security section in your user account and choose three secret questions and answers.
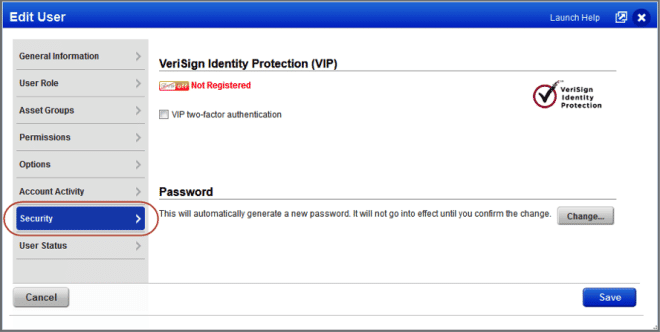
We’ve moved the VIP two-factor authentication and Change Password options to a new Security section. Managers and Unit Managers will see this when editing another user’s account.
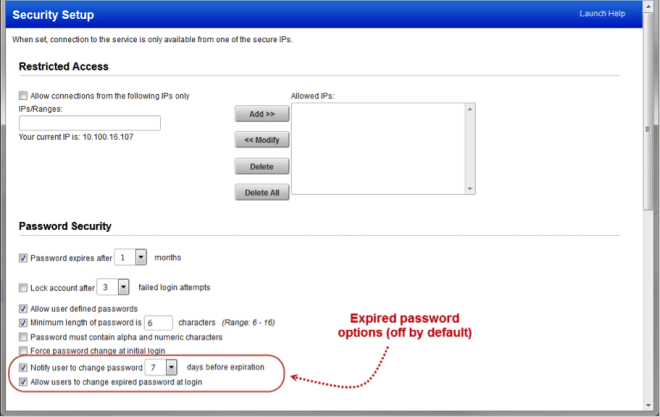
Expired Password Options: Managers can set new options for expired passwords:
- notify users when their password is going to expire
- prompt users to change their password at login after it has expired.
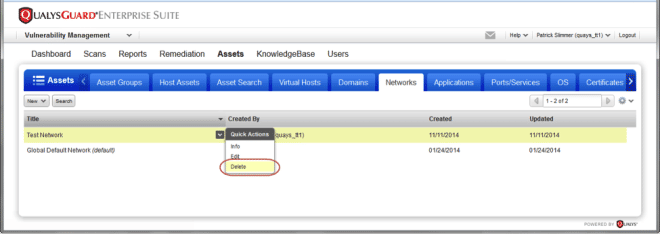
Ability to Delete Empty Networks: Managers can now delete empty networks from the subscription. A network is empty if it does not have scanner appliances, associated asset groups, scheduled tasks or hosts with scan data. If the network has any account data associated with it, then it cannot be deleted from the UI. You also can’t delete networks if the subscription All group is assigned to any business units or sub-users.
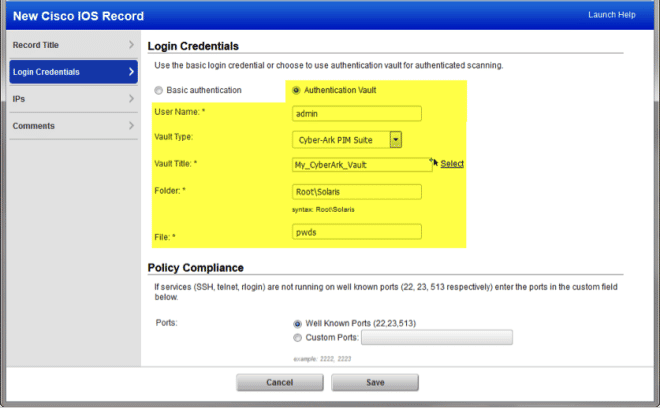
Cisco IOS Authentication – Support for Cyber-Ark PIM Suite Vaults: This release introduces the ability to use your Cyber-Ark PIM Suite password vault when authenticating to Cisco IOS devices. Note – We already support Cyber-Ark vaults for other technologies, including Unix and Windows.
Run Scheduled Reports on Demand: You can now run scheduled reports as needed instead of waiting for the next scheduled launch time.
Download Email List from Distribution Group: You can now easily download the list of members assigned to a distribution group so you can verify the list easily outside of Qualys.
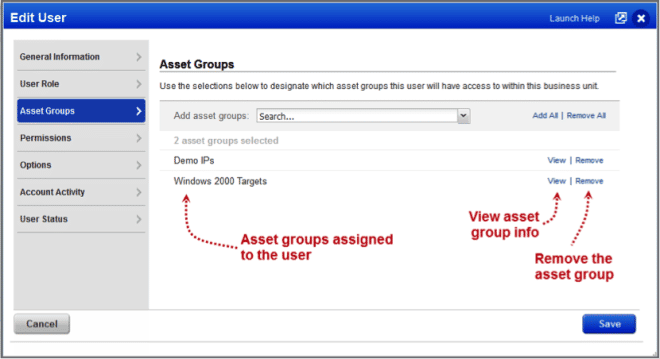
General UI Improvements: A number of improvements have been made to make Qualys 8.3 easier to use. Throughout the UI you’ll notice an improved list selector. For example, when assigning asset groups to a user, you’ll now see:
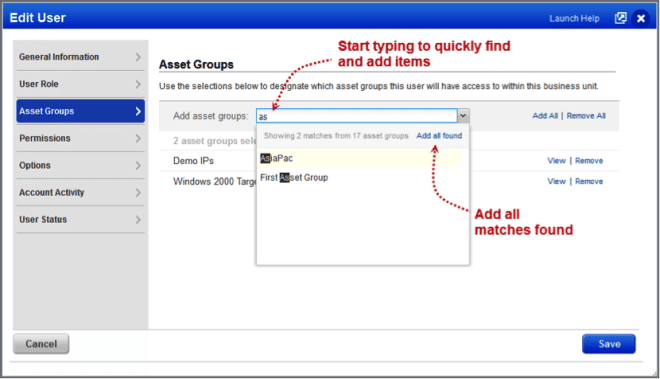
Use the Search field to quickly find asset groups and add them to the user’s account. Just start typing the asset group name and we’ll show you matches. Then add all matches with one click.
You’ll see these improvements when searching the KnowledgeBase and when selecting list criteria for your dynamic search lists.
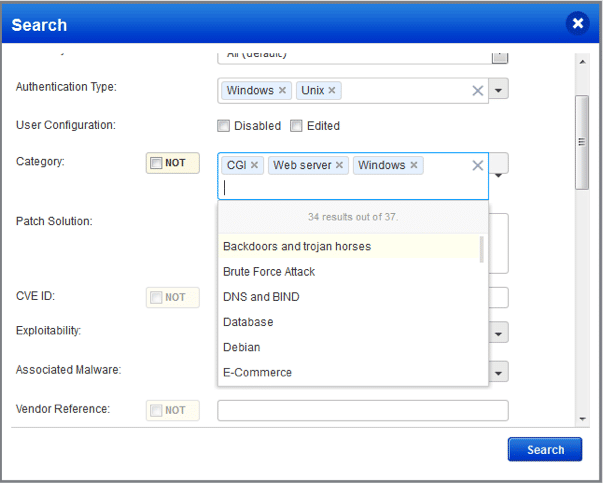
It’s easier to select multiple items. Just start typing or select from a drop-down. Also, you can now choose multiple categories where you were previously limited to one. We’ll use OR logic when multiple items are selected. For example, CGI OR Web server OR Windows.
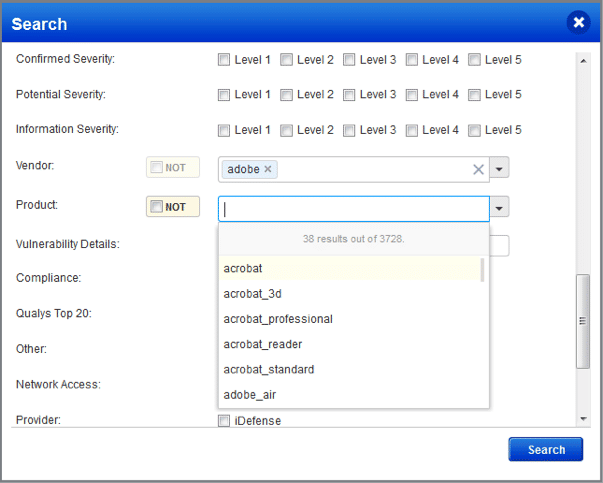
The Vendor and Product fields are now tied to each other. If you pick Adobe from the Vendor list, you’ll only see Adobe products in the Product list. If you select more than one vendor, like Adobe and Microsoft, then you’ll see products for both.
New Authentication Vault API: The new Authentication Vault API (/api/2.0/fo/vault) allows you to manage authentication vaults for authentication records that use them. Using this API you can list vaults, create new vaults, update and view vault settings, and delete vaults. For more details, see the Qualys Cloud Suite 8.3 API Release Notification.
Vulnerability Management (VM)
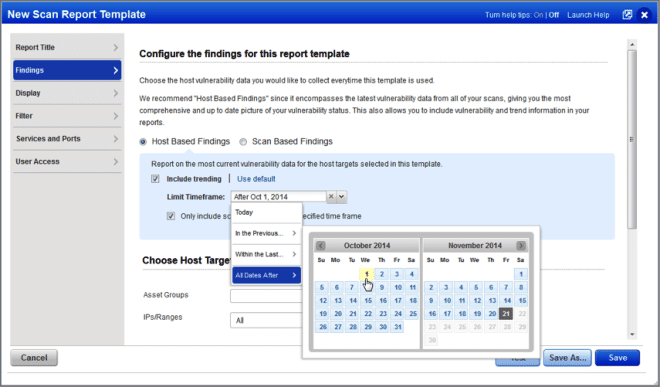
More Date Filtering Options for Host-Based Scan Reports: With this release it’s easy to create scan reports with host-based findings within a specific timeframe. In the scan report template under Host Based Findings just choose the date range you’re interested in – starting on a specific date, or the date the report is run (today).
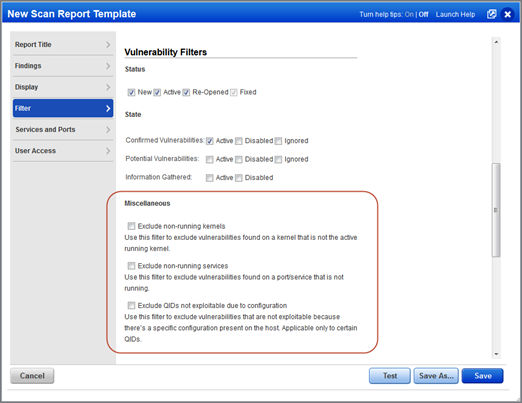
Additional Vulnerability Filters in Scan Reports: New vulnerability filters allow you to exclude certain vulnerabilities from your reports like vulnerabilities found on a port/service that isn’t running, and vulnerabilities that can’t be exploited because of a host configuration. Apply these filters to your scan reports, patch reports and scorecard reports.
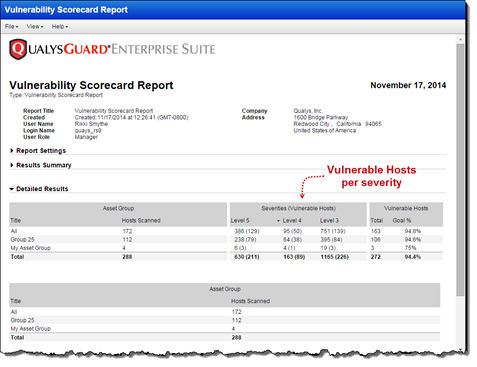
Vulnerability Scorecard Report – New Vulnerable Hosts per Severity: The Vulnerability Scorecard Report now shows you the number of hosts affected by the vulnerability severities (Level 5, 4, 3).
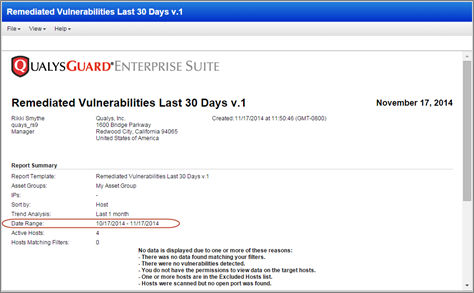
Remediated Vulnerabilities Report – Improvements: This report tells you about vulnerabilities that have been remediated in your account within the last 30 days. We’ve made improvements to the report for this release. We’ll always show the full date range for the report, even if there are no remediated vulnerabilities for the selected hosts.
Policy Compliance (PC)
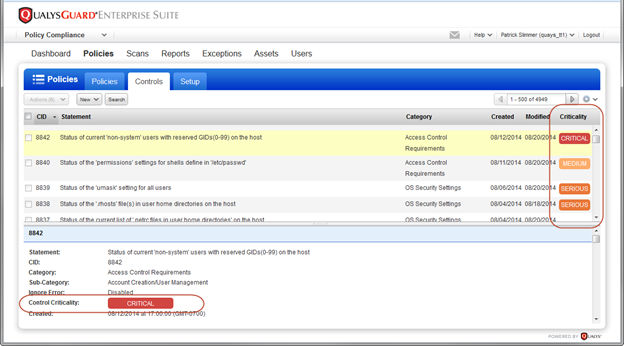
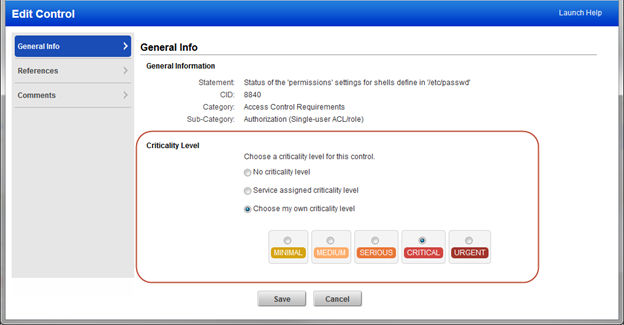
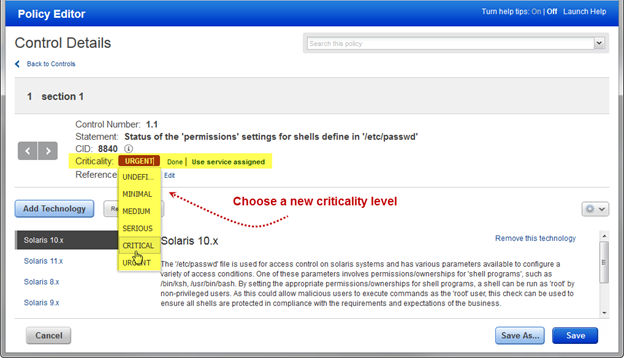
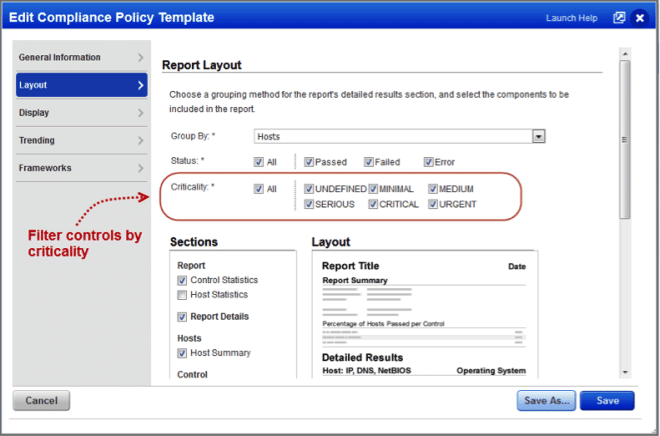
Introducing Control Criticality: Control Criticality is a new feature in Policy Compliance that provides ratings for controls, including the ability to customize ratings at the control level and at the policy level. When enabled, you’ll see criticality wherever control details appear – in the controls list, in your policies and reports.
Customizing Control Criticality in a control:
Customizing Control Criticality within a Policy:
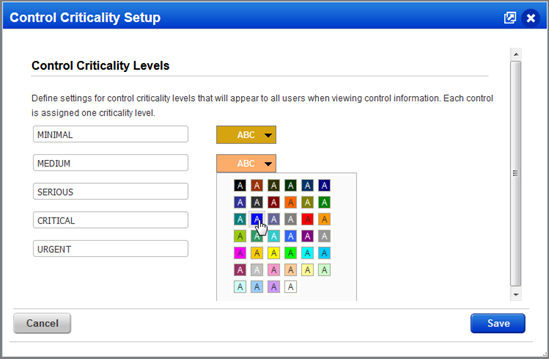
You can also customize the labels associated with the different control criticality levels:
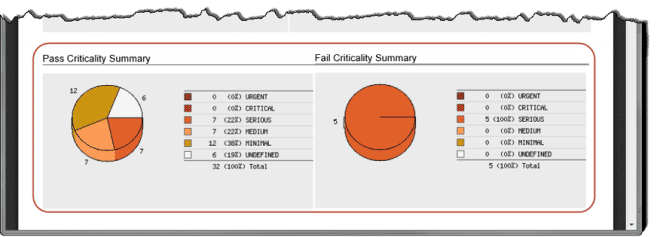
You’ll see criticality in the Control Statistics table (as shown below) and in the Detailed Results section where control details appear.
We’ve also added 2 new pie charts to your policy report to show the number of passed and failed controls at each criticality level. Controls without a criticality level are counted as “Undefined”.
You can also filter your reports by Criticality:
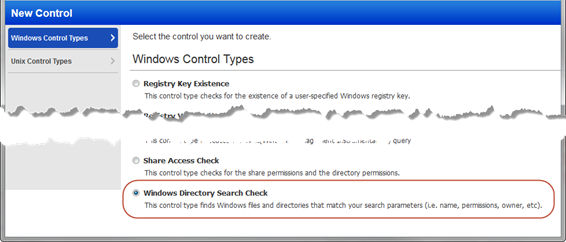
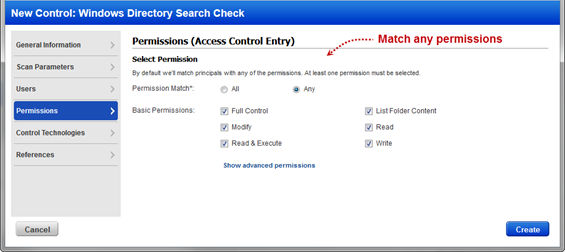
New Windows Directory Search UDC: This release introduces a new User Defined Control (UDC) called Windows Directory Search Check. Configure this control to find files and directories that match certain parameters (name, permissions, etc). You’ll tell us where to search and what you’re looking for, and we’ll return a list of matches in your scan results.
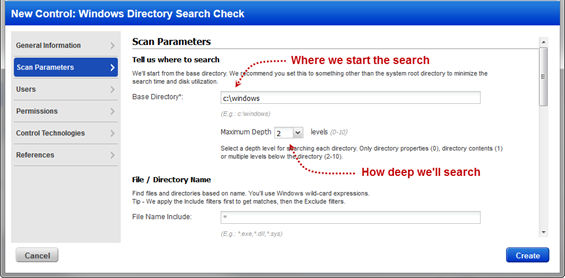
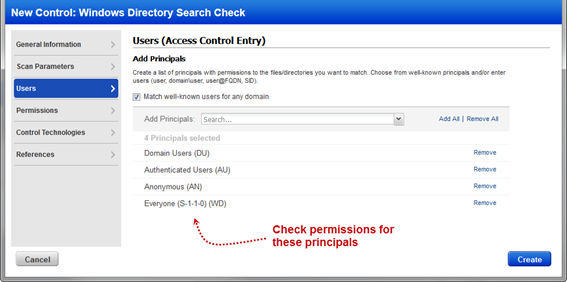
You can specify directories, recursion depth, and filename patterns as well as user and permission information to look for:
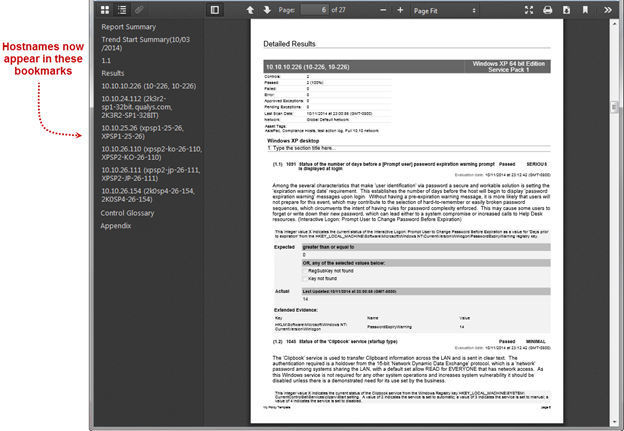
Policy Report – Hostnames Appear in PDF Bookmarks: The list of bookmarks in your PDF policy reports will now include the hostname for each host. Click any bookmark to jump directly to the host details in the report.
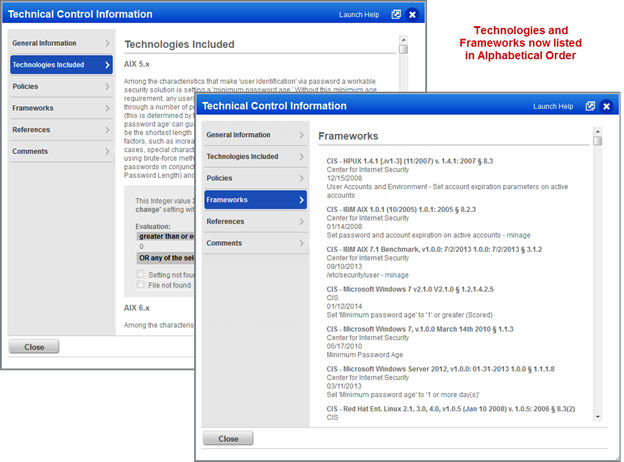
Control Technologies and Frameworks in Alphabetical Order: You’ll see that the technologies and the frameworks listed in the Control Information page are now in alphabetical order, making the information you want easier to find.
Release Schedule
For release notifications containing details specific to each platform, including the release date, and to subscribe to release notifications for your platform, please see the following: