Qualys Cloud Suite 8.4 New Features
This new release of the Qualys Cloud Suite, version 8.4, includes updates for usability and functionality across the platform as well as Vulnerability Management and Policy Compliance.
Feature Highlights
- Qualys Cloud Platform
- Launch Scan from the Host Assets List
- Launch Scan on EC2 Classic Hosts Only
- Delete Networks with Data
- Support for MySQL Authentication
- Show Passing Credentials in Breakdown
- Change Your Time Zone
- New Columns added to the Users List
- Enhanced Support for Restricted View of User Information
- New Extended View of Asset Groups within Workflows
- Improved Asset Group Auto-Complete Widget
- Change Contact Info in Email Notifications
- Qualys Vulnerability Management (VM)
- Ability to Delete Domains
- Find Out when a Host was First Discovered by a Map
- Easily Disable DNS Traffic for Your Maps
- New Ways to Search and View Certificates
- Remediation Policy Rule – Exclude Non-Running Kernels
- Patch Report – Display CVSS Base Scores
- Most Vulnerable Hosts Report – Filter QIDs by Severity
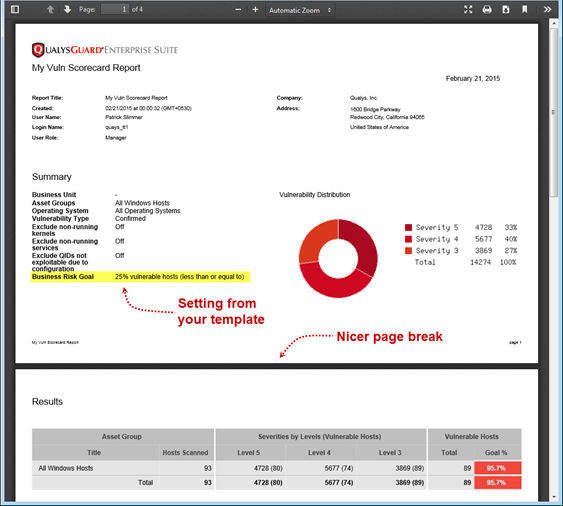
- Vulnerability Scorecard Report – PDF Improvements
- CVSS Vectors added to CSV reports
- Associated Tags added to CSV reports
- Qualys Policy Compliance (PC/SCAP)
Qualys Cloud Suite 8.4 will be released in production in the coming weeks and includes enhancements to Vulnerability Management (VM) and Policy Compliance (PC), the Qualys Cloud Platform and the API.
For release notifications containing details specific to each platform, including the release date, and to subscribe to release notifications for your platform, please see the following:
- <span style="text-decoration: underline;"><span style="color: #0066cc;">Qualys Cloud Suite 8.4 Release Notification – Available Tuesday, April 14, 2015 on US Platform 1</span></span>
- <span style="text-decoration: underline;"><span style="color: #0066cc;">Qualys Cloud Suite 8.4 Release Notification – Available Thursday, April 9, 2015 on US Platform 2</span></span>
- <span style="text-decoration: underline;"><span style="color: #0066cc;">Qualys Cloud Suite 8.4 Release Notification – Available Monday, April 13, 2015 on EU Platform</span></span>
Qualys Cloud Platform Updates
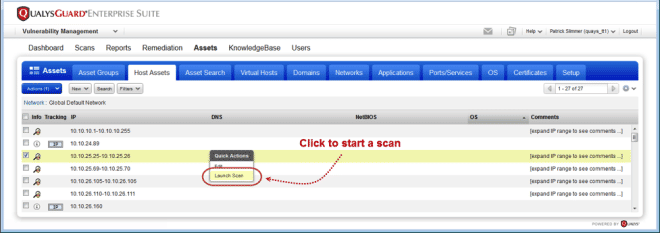
Launch Scan from the Host Assets List
We’ve heard from customers the need to quickly perform ad-hoc scans directly from the host assets list; the following two features will enable that capability.
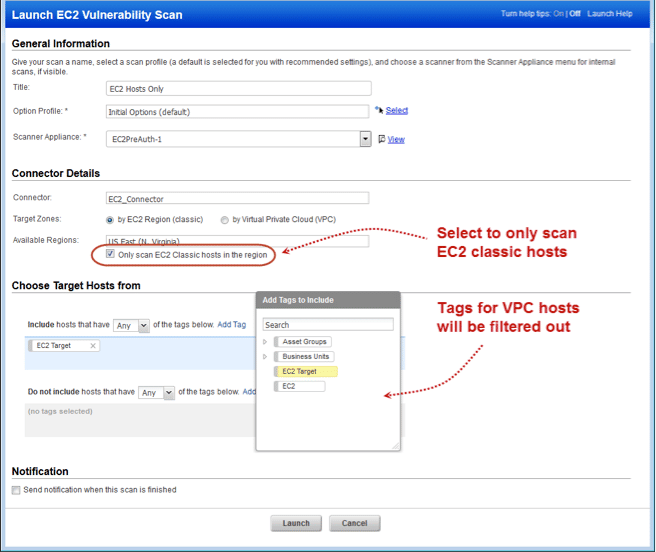
Launch Scan on EC2 Classic Hosts Only
Now you can avoid scanning VPC hosts in a selected EC2 region. Just select the new checkbox “Only scan EC2 Classic Hosts in the region” when defining your EC2 scan.
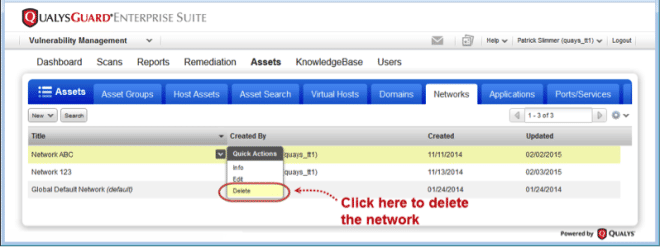
We’ve received feedback that previously deleting networks was a long task due to having to remove the data within the networks first. We’ve now automated that task and provided a wizard to detail what exactly you’re deleting.
Delete Networks with Data
Now you can easily delete networks, even if there is data associated with your network.
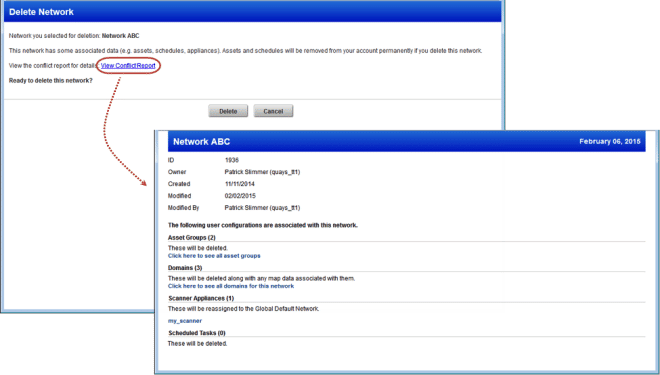
We’ll provide you with a conflict report when the network has data associated with it like assets, schedules and scanner appliances. Review the report for all the details.
Check out this sample report:
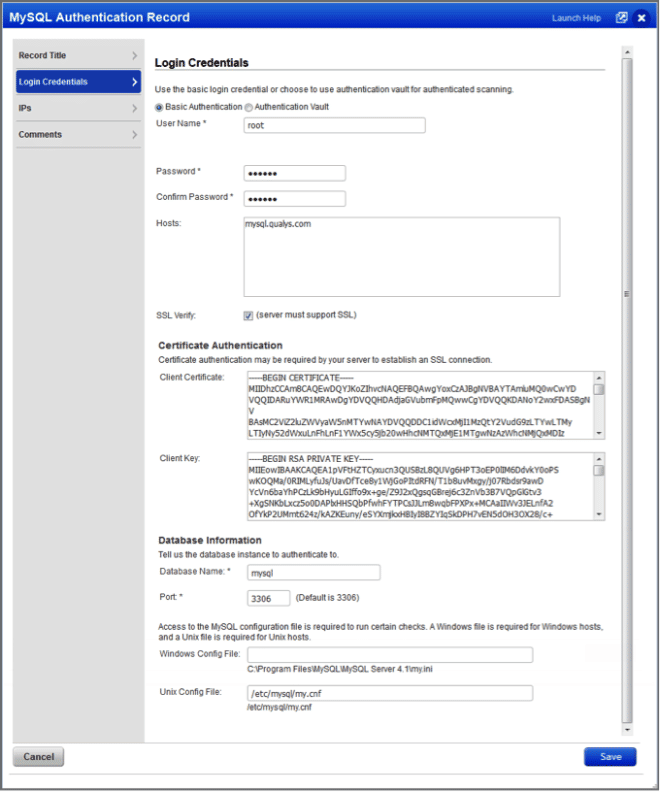
Support for MySQL Authentication
We’ve expanded database authentication to include MySQL databases.
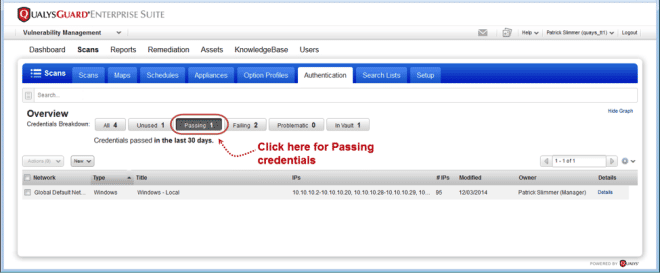
Show Passing Credentials in Breakdown
With one click you can find authentication records with credentials that were successful 100% of the time (in the last 30 days). Tip – The credentials breakdown is a great way to learn about your records – which ones are failing, problematic, unused, etc.
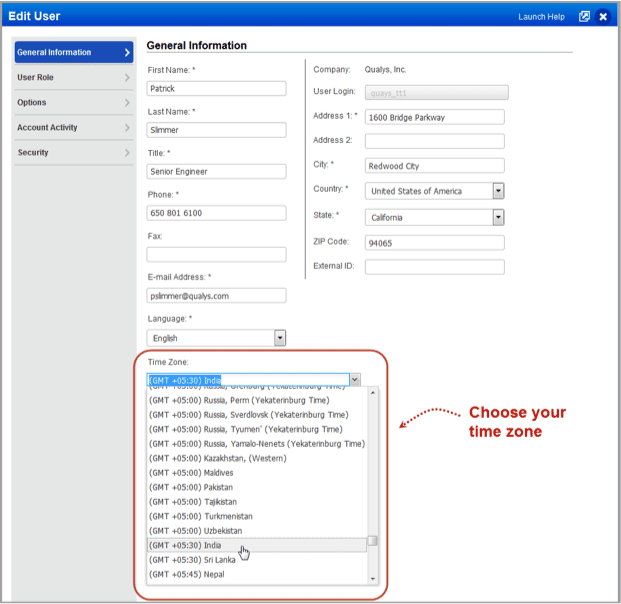
Change Your Time Zone
Your time zone setting affects how dates/times will be shown in the UI and reports. By default it’s set to your browser’s time zone (Auto). Your time zone selection will be the default for new schedules. You can override the time zone in the Scheduling details.
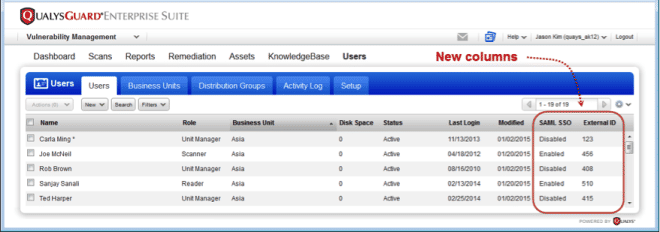
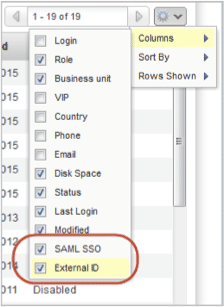
New Columns added to the Users List
The SAML SSO column identifies whether SAML is enabled for the user’s account. The External ID column shows the external ID assigned to the user, if any.
New columns are hidden initially. When the option is selected to show the columns in the list, the details will appear in downloaded reports. You can quickly find users that have SAML SSO enabled or disabled by using the Search and Filter options above the Users list.
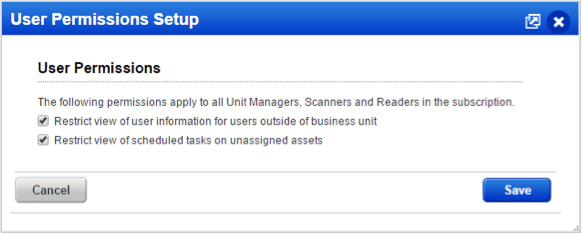
Enhanced Support for Restricted View of User Information
We’ll no longer show a user’s email address and phone number in the Users list to users outside of their Business Unit. This is in addition to the following information which is already hidden: fax, address, SAML SSO and external ID. Managers can restrict the view of user information.
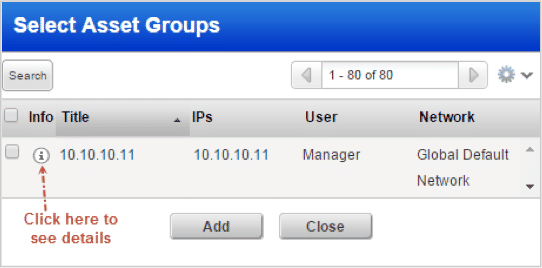
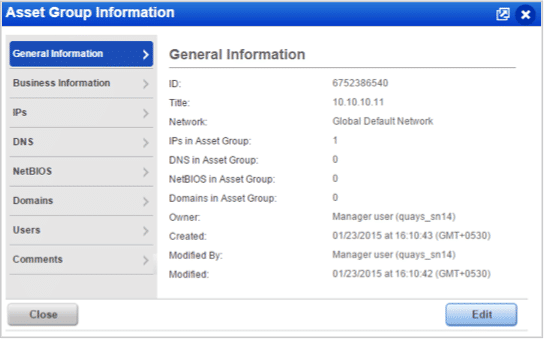
New Extended View of Asset Groups within Workflows
Users will now be able to view the asset group information when they need it – while selecting asset groups for scans and reports. Starting with release 8.4, we have made enhancements by adding an extra column named “Info” in the Select Asset Groups window. This column provides a clickable information icon against every asset group listed in the window.
The detailed information displays in a separate frame within the “Select Asset Groups” window. Users with permissions to edit asset groups can also edit the asset group.
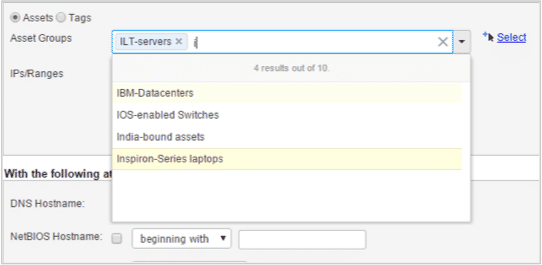
Improved Asset Group Auto-Complete Widget
We have added improved auto-complete functionality to the Asset Groups widget for asset group selection in Scans, Assets, Reports, and other launch pages. The new multi-select combo box provides features like auto-complete, multiple selection of items, clearing all items in one go, and adding or removing the selected items. The combo box expands as the number of items increase allowing you to view all selected items without scrolling inside the component.
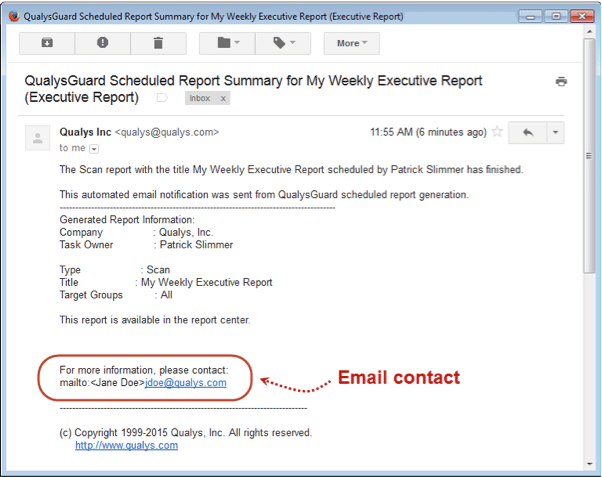
Change Contact Info in Email Notifications
You may want to change the contact that appears in email notifications to ensure users are reaching out to the appropriate person or group. Managers can provide a single contact for the subscription, and they can allow Unit Managers to override the contact for each business unit.
As a Manager, you can change the name and email address to display for a contact.
Vulnerability Management (VM)
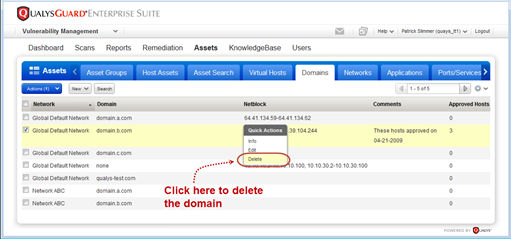
Ability to Delete Domains
While the ability to delete domains has been available by request from support, we’ve now added the ability for our customers to delete those domains themselves.
Managers can now delete domains from the subscription. Any domain can be deleted except for the system-provided domain “qualys-test.com”.
What happens next?
- The unique domain (network/domain) will be removed from the account along with any map data associated with it. This data cannot be recovered once deleted.
- Any scheduled maps on the domain will be deactivated at the next scheduled launch time.
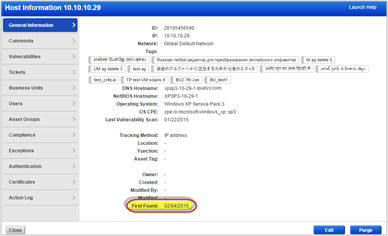
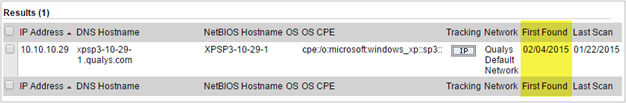
Find Out when a Host was First Discovered by a Map
The Host Information window provides the detailed information including the “First Found” date.
If a dash is displayed, your host was not discovered by a map, or it was discovered before December 2011, which is when we started saving the first found date.
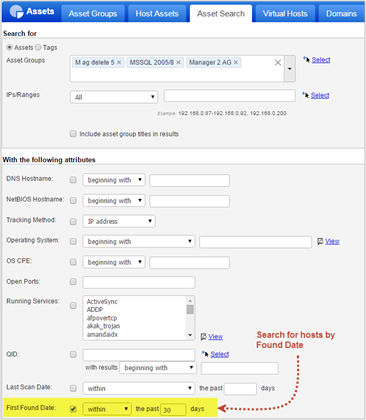
You can also use the Asset Search to list hosts found within a certain time frame, for example hosts found within the last 30 days.
On clicking Search the Asset Search Report opens.
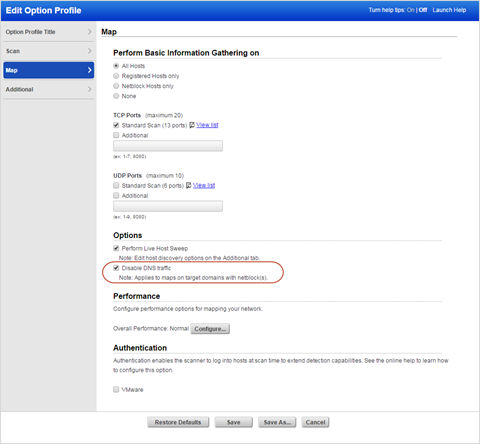
Easily Disable DNS Traffic for Your Maps
If your maps are generating too much DNS traffic, overwhelming your DNS server(s), or you want to get a map back quickly, you can disable DNS traffic in an option profile and run your maps using that profile. This option applies only to maps on target domains with netblock(s), e.g. none:[10.10.10.2-10.10.10.100].
How it works
We’ll perform network discovery only for the IP addresses in the netblocks:
- No forward or reverse DNS lookups, DNS zone transfers or DNS guessing / bruteforcing will be made
- DNS information will not be included in map results
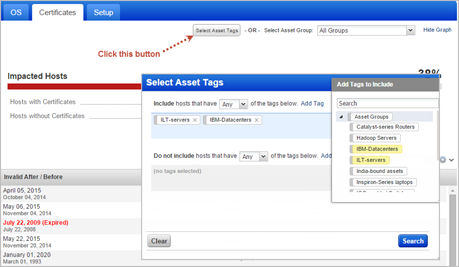
New Ways to Search and View Certificates
Tag-based Certificate Search: This new option on the Certificates dashboard allows you to filter the list to only show certificates for hosts with certain tags. If you don’t see this option, Asset Tagging is not enabled for your account. Please contact your Account Manager or Support to get this feature.
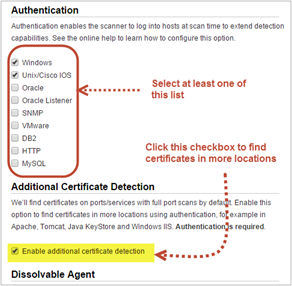
Additional Certificate detection via Option Profile: Finding certificates is no longer limited to the ports only. With this new option (and the use of authentication) we can find certificates in more locations on your hosts, like in Apache, Tomcat, Java KeyStore, and Windows IIS.
Newly discovered certificates will be added automatically to your certificates list as new scan results are processed. Certificate details will include the location where the certificate was found. A certificate may be found on a port, on a location or both. A new search option lets you quickly find certificates found exclusively on ports.
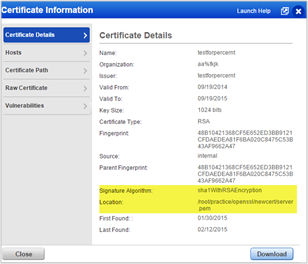
View the Signature Algorithm: You can now view the signature hash algorithm in the Certificate Information page.
Note – You must run new vulnerability scans on your hosts to get this information.
New information details – signature algorithm and location – will also appear in the CSV report when you click Download.
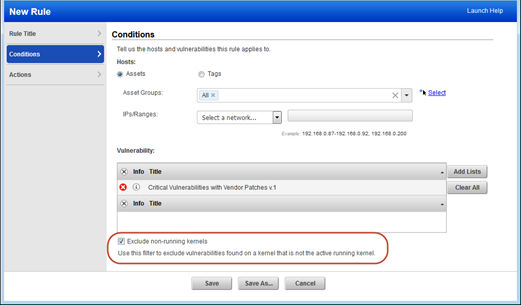
Remediation Policy Rule – Exclude Non-Running Kernels
By selecting this option, you can be sure tickets are only created for vulnerabilities found on the running Linux kernel. Sound familiar? That’s because this filter already exists in your scan report templates for filtering vulnerabilities from your reports.
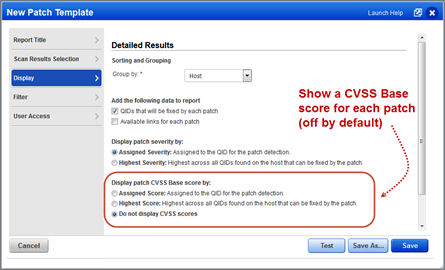
Patch Report – Display CVSS Base Scores
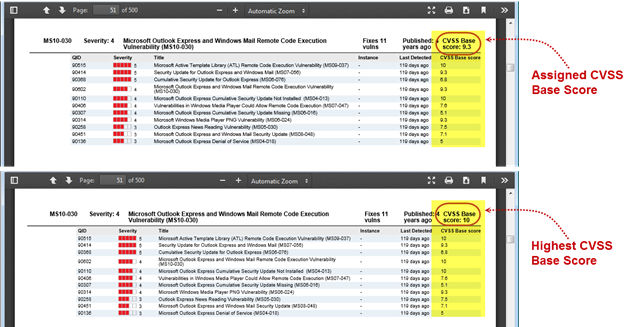
A new option is available in the patch report template to display CVSS base scores. For each patch, you can show the assigned score for the patch detection or the highest score across all QIDs fixed by the patch. You’ll also see the score for each QID in your report (when you choose to display QIDs).
Check out the following samples. The assigned score for patch MS10-030 is 9.3 and the highest score is 10. Also note the CVSS Base score for each QID fixed by the patch.
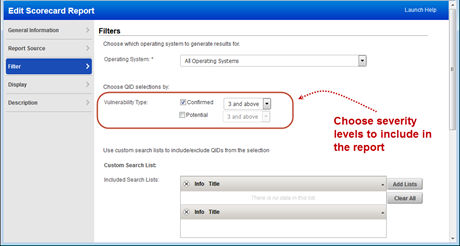
Most Vulnerable Hosts Report – Filter QIDs by Severity
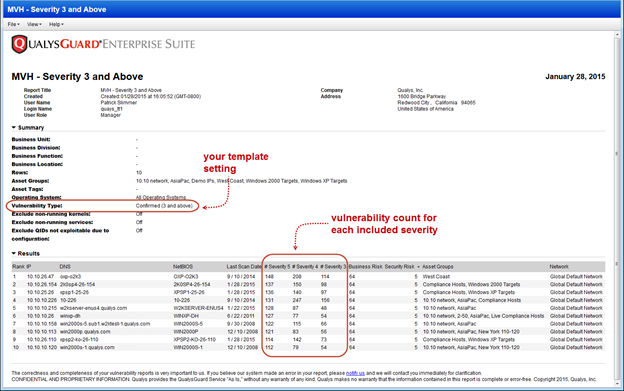
Your Most Vulnerable Hosts Scorecard Report will now include confirmed vulnerabilities with severity 3 and above by default (previously this report included severity 4 and 5 only). Edit the filter settings in your scorecard template to include more or fewer severity levels. When you choose to filter QIDs by severity level, you cannot also filter QIDs by search list.
This sample report shows the 10 most vulnerable hosts – the hosts with the highest number of vulnerabilities with severity levels 3, 4 and 5. When you include confirmed and potential vulnerabilities, we’ll add them together and show the sum for each severity level.
Vulnerability Scorecard Report – PDF Improvements
You’ll notice these improvements to the PDF version of the Vulnerability Scorecard Report: 1) we now display the Business Risk Goal setting and 2) nicer page breaks.
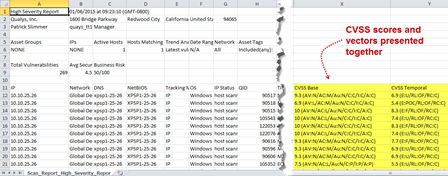
CVSS Vectors added to CSV reports
Your vulnerability scan reports in CSV format will now show the CVSS vector for each CVSS Base and Temporal score. The vector is a string of abbreviated metrics and values that describe the components used to calculate the score. For example, you might see:
CVSS Base
9.3 (AV:N/AC:M/Au:N/C:C/I:C/A:C)
In this example, the base vector includes these metric values: Access Vector: Network, Access Complexity: Medium, Authentication: None, Confidentiality Impact: Complete, Integrity Impact: Complete, Availability Impact: Complete.
Want to know more? Go to CVSS v2 Complete Documentation
Here’s a sample report:
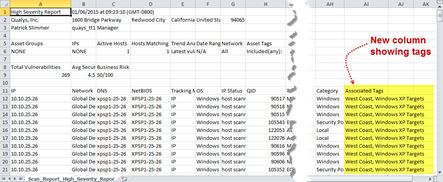
Associated Tags added to CSV reports
With this release vulnerability scan reports in CSV format will show asset tags associated with each host listed in the report. Tags appear in a new “Associated Tags” column when your report target includes asset tags and your report template is configured for host based findings (automatic data). Associated tags already appear in other report formats like HTML and PDF.
Here’s a sample report:
Policy Compliance (PC)
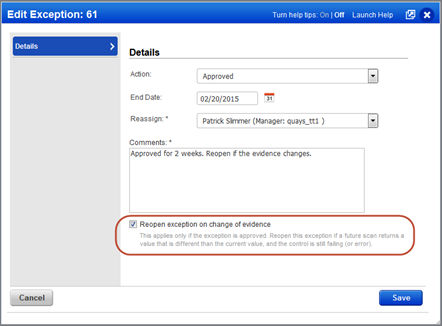
Reopen Exceptions when Evidence changes
With this option, we’ll automatically reopen an exception if a future scan returns a value for the control that is different than the value at the time of the original approval when the control is still failing.
For example, let’s say CID 1071 “Status of the ‘Minimum Password Length’ setting” has an expected value of 8 and your host returned a value of 5, which is failing. You request an exception for the host and it gets approved. The next scan of the host returns a value of 6 which is an improvement but still failing. If the reopen feature was enabled, then the exception status changes from Approved to Pending. The exception will need to be re-evaluated and approved again.
You can choose this option when requesting the exception or when approving it.
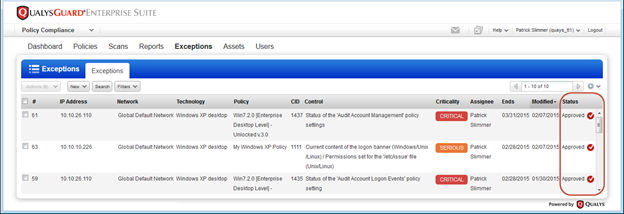
You’ll see a check mark next to the Approved status when the option “Reopen exception on change of evidence” is enabled for the exception.
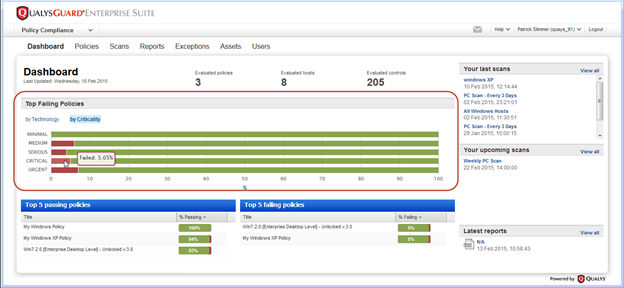
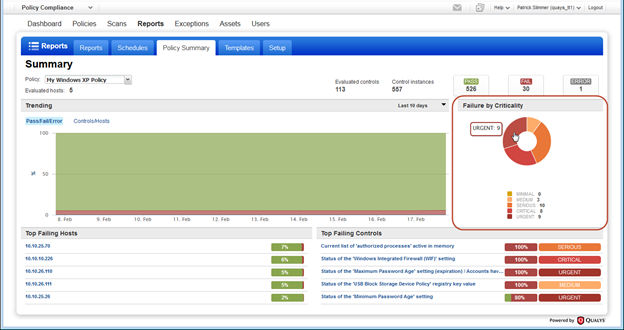
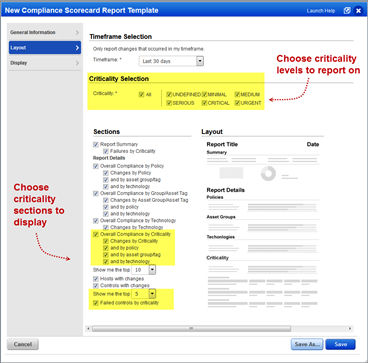
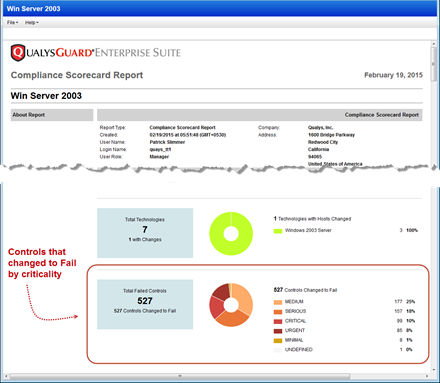
Criticality added to Dashboard and Reports
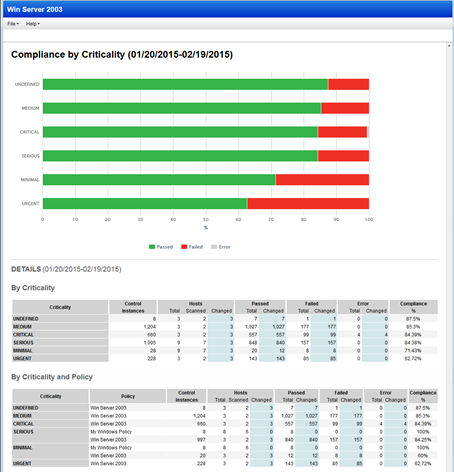
Get trend information and control statistics broken down by criticality. Check out the changes we made to the Dashboard, Policy Summary and Scorecard Report.
Dashboard: Get passed/failed statistics across all your policies for each criticality level.
Policy Summary: This new pie chart shows the number of failed control instances at each criticality level.
Scorecard Report: Edit your scorecard report template to select the criticality levels and sections to include in your reports.
Here’s a sample scorecard report. Check out the new pie chart in the Report Discoveries section.
Scroll down further to see the Compliance by Criticality section.
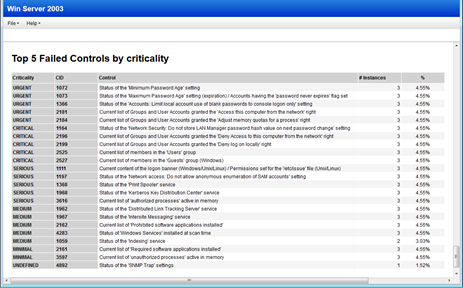
The last section of the report shows the Top 5 failed controls for each criticality level.
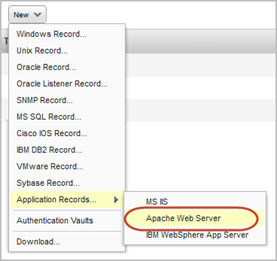
Apache HTTP Server 2.4 Support
We’ve extended our support for Apache Web Server authentication to include Apache HTTP Server 2.4. These technologies are already supported: Apache HTTP Server 2.2, IBM HTTP Server 7.x and VMware vFabric Web Server 5.x.
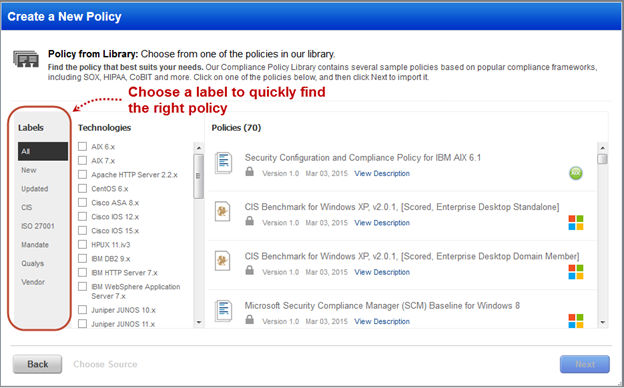
Policy Library Content and Label Updates
Finding the policy you want in our Compliance Policy Library is easier than ever. Just choose one of the new labels on the left to filter the list. “New” policies were added in the last 90 days and “Updated” policies were changed in the last 90 days.
We’ve also removed the unlocked versions of the CIS Benchmarks, and older content that has been replaced with newer versions of policies.
Release Schedule
For release notifications containing details specific to each platform, including the release date, and to subscribe to release notifications for your platform, please see the following: