Qualys Cloud Suite 8.5 New Features
This new release of the Qualys Cloud Suite, version 8.5, includes updates for usability and functionality across the platform as well as Vulnerability Management and Policy Compliance.
Cloud Platform: You can now add multiple scanners to a scan, simplifying the balancing of scans across devices in large deployments. Also, a number of improvements have been added making it easier to work with and report on Authentication Records along with several improvements to notifications.
Vulnerability Management: There are several scanning and reporting improvements in this release, along with the initial capabilities for SSL Labs integration into VM.
Policy Compliance: There are several improvements to make it easier to use Policy Compliance by hiding unneeded technologies and policies throughout the UI. You can also now create a CSV Report of your policy configuration, a feature many have been asking for! Platform support has been expanded with coverage for new technologies and the UDC has been enabled for 8 new versions of popular OS’s.
Feature Highlights
- Qualys Cloud Platform
- Qualys Vulnerability Management (VM)
- Qualys Policy Compliance (PC/SCAP)
- Ability to Deactivate Policies
- View Preferred Technologies with Configurable Account Filters
- Platform Support for Apache Tomcat and Microsoft SQL Server 2014
- UDC Support for: Windows 2012 R2, Windows 8.1, Mac OS X 10.9/10.10, RedHat 7, centOS 7, Oracle Enterprise Linux 7
- Export Policy Configuration Details to CSV
- Evidence Details Added to SCAP CSV Report
Qualys Cloud Suite 8.5 will be released in the coming weeks. For release notifications containing details specific to each platform, including the release date, and to subscribe to release notifications for your platform, please see the following:
- Qualys Cloud Suite 8.5 Release Notification – Available Monday, August 10, 2015 on US Platform 1
- Qualys Cloud Suite 8.5 Release Notification – Available Tuesday, July 28, 2015 on US Platform 2
- Qualys Cloud Suite 8.5 Release Notification – Available Thursday, July 30, 2015 on EU Platform
Qualys Cloud Platform Updates
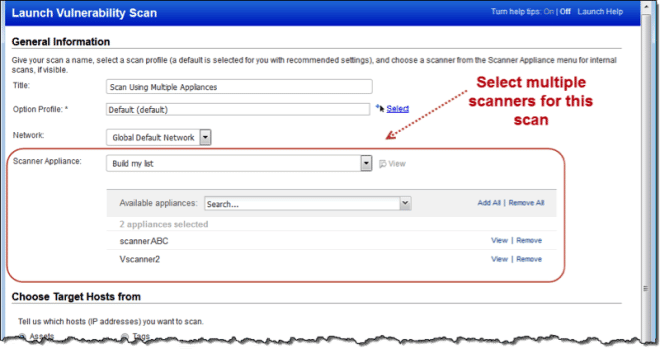
Select Multiple Scanner Appliances for Scans
With this release you can select multiple scanner appliances for your internal vulnerability and compliance scans (PC and SCAP). This is especially useful when scanning a large number of hosts because it allows you to distribute the scan task across scanner appliances.
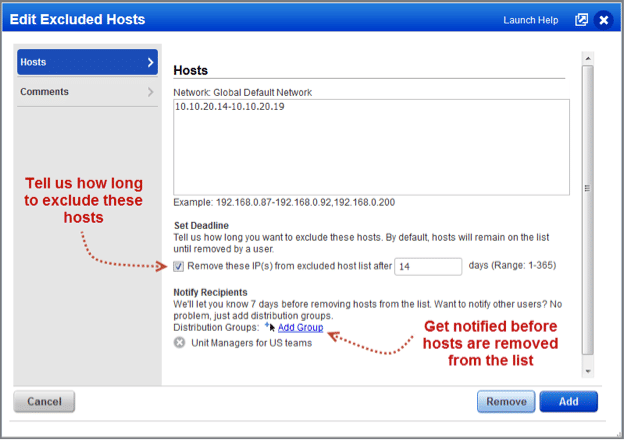
Set Expiration Date for Excluded Hosts
You can now set an expiration date when adding IPs to the Excluded Hosts list. When the date is reached, the IPs are automatically removed from the list and made available again for scanning. We’ll send you an email 7 days before removing the IPs, allowing you time to change the date if you want. To notify other users, simply add distribution groups and the email will be sent to them as well.
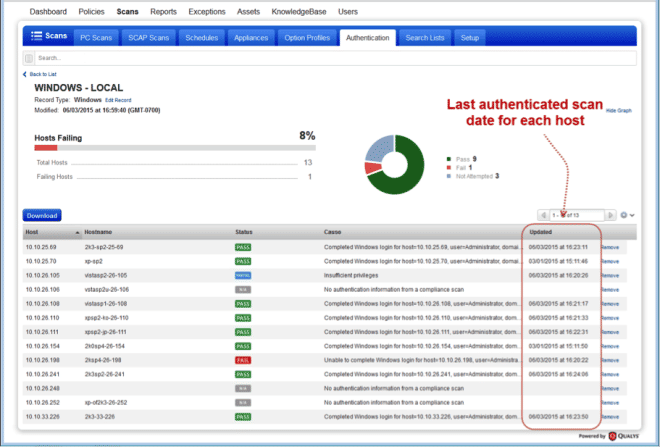
Last Scan Date added to Authentication Record Details
Drill down into authentication record details to see the date/time of the last authenticated scan for each host in the record. This is when the Pass/Fail status was last updated for the host.
The Credentials Breakdown options (on the authentication dashboard) only consider hosts scanned in the last 30 days. Now you can easily identify hosts that aren’t being counted because they were scanned more than 30 days ago.
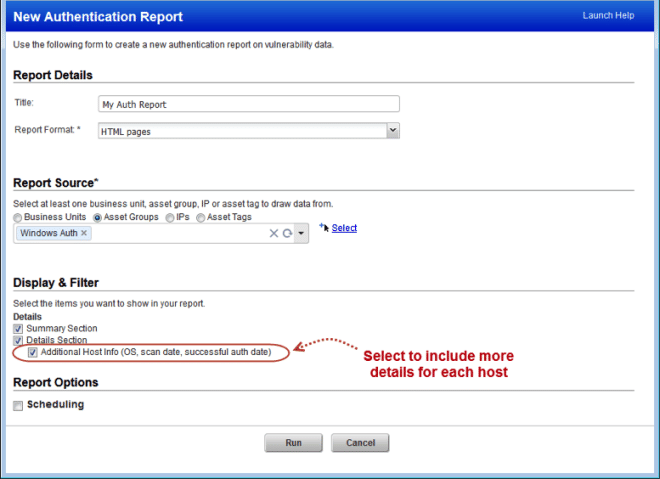
More Host Info in Authentication Reports
The following information has been added to the report for each host: 1) the host’s operating system, 2) the last time you scanned the host with authentication, and 3) the last time authentication was successful.
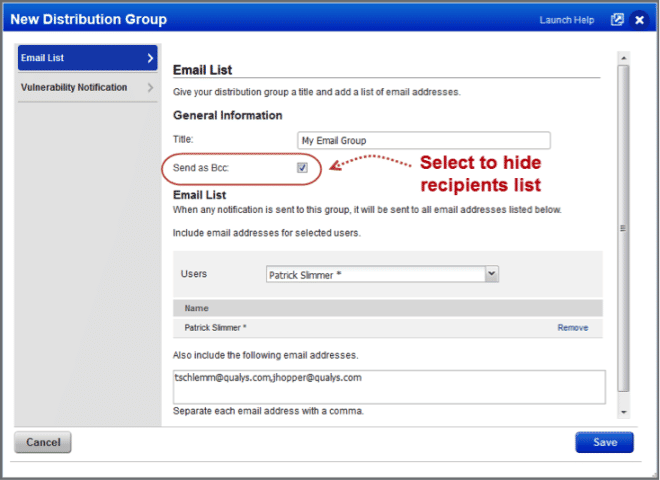
Send Email Notifications to Bcc List
You can now select “Send as Bcc” in your distribution group settings. We’ll hide the list of recipients any time the distribution group is selected for a notification – scan notifications, report notifications, vulnerability notifications, etc.
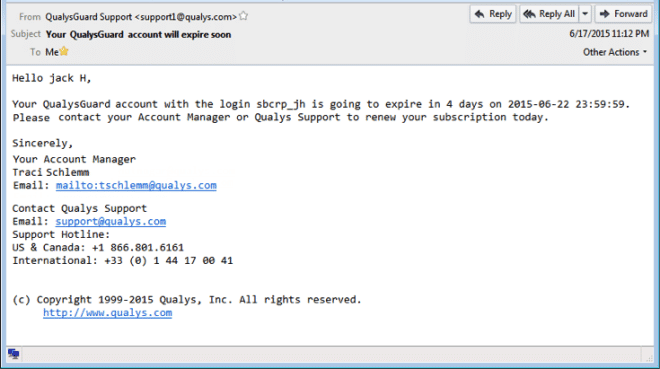
Get Notified Before Your Account Expires
The Manager Primary Contact (for the subscription) will now receive an email notification when the account is going to expire with details on how to renew. The email is sent 45 days, 30 days, 14 days and 7 days before the expiration date, and every day after that until the expiration date.
Vulnerability Management (VM)
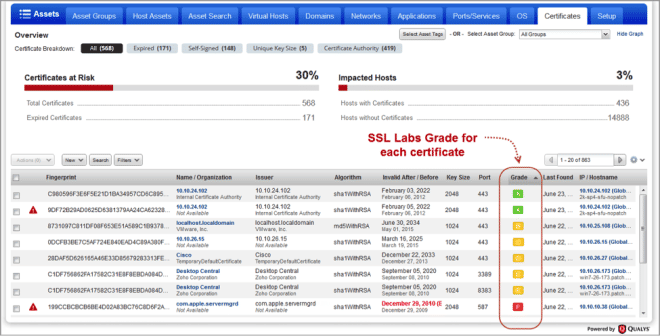
SSL Labs Grade added to Certificates List
We’re excited to announce that we’ve integrated SSL Labs with Qualys VM. When enabled, you’ll get a letter grade (A+, A, A-, B, C, D, E, F, T, M, NA) for each certificate on your certificates list. Grades are updated automatically each time new vulnerability scan results are processed for your hosts. Please Note – The SSL Labs Grade feature must be enabled for your subscription. Please contact your Technical Account Manager or Support to get this feature.
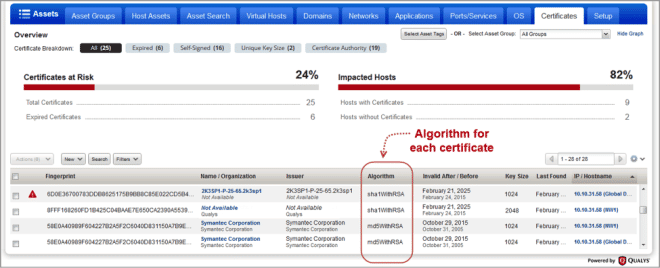
Algorithm added to Certificates List
For each certificate you’ll see the algorithm (sha1WithRSA, md5WithRSA, etc) in the new Algorithm column. Just go to VM > Assets > Certificates to see it.
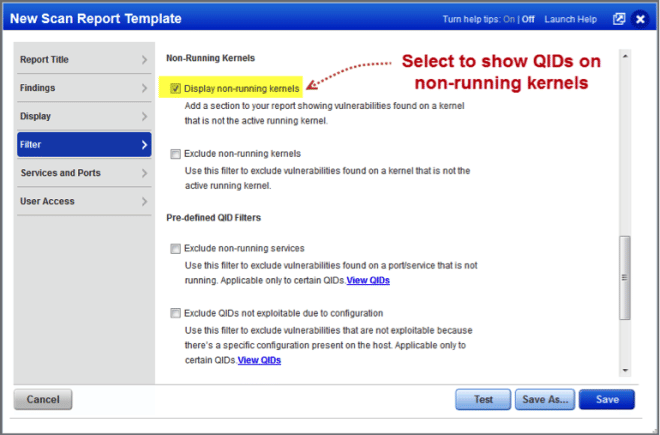
Identify Vulnerabilities on Non-Running Kernels
With this release, users can create reports that show non-running kernels in the vulnerability details. This way you can identify vulnerabilities found on a kernel that is not the active running kernel.
A new option “Display non-running kernels” has been added under “Non-Running Kernels” on the Filter tab of report templates for scan, patch, and scorecard reports.
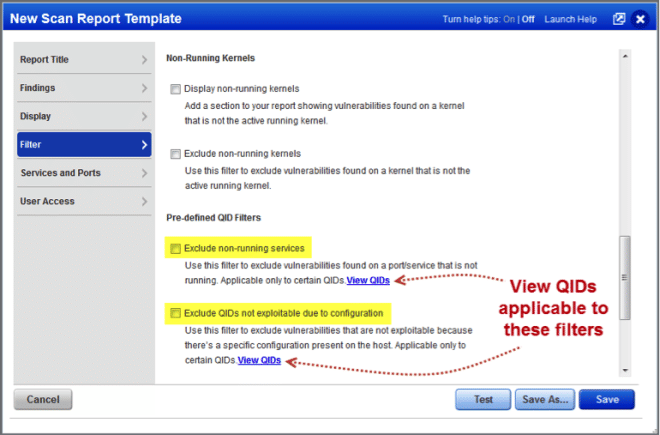
View QIDs Applicable to Report Filters
With this release you can identify the vulnerabilities that apply to these report template filters: “Exclude QIDs on non-running services” and “Exclude QIDs not exploitable due to configuration”. These filters appear in templates for scan reports, patch reports and scorecard reports. You can also find these QIDs in the KnowledgeBase and create a search list based on these options.
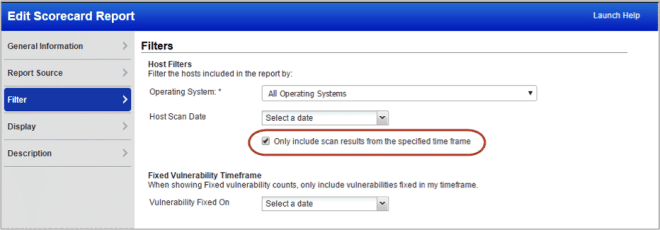
Select time frame for Scorecard Reports
We have enabled time frame selection for Scorecard reports. This means only the scan results during the period defined by you will be displayed in the Scorecard Report. Using the Host Scan Date you have options like today, all dates before, all dates after, date range, in the previous day, week, month, year, etc, to define the time frame.
Policy Compliance (PC)
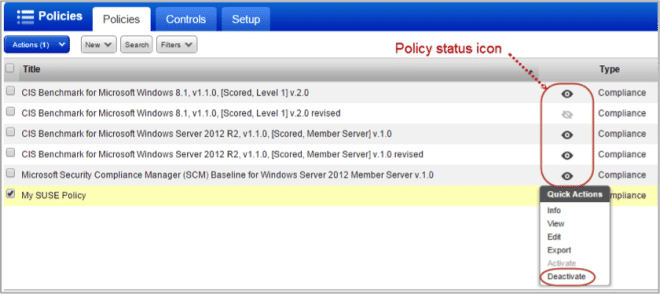
Ability to Deactivate Policies
You can now mark policies that you are not using in your account as Inactive. Policies that are in inactive state will not be scanned or reported on.
You may want to hide a new policy while you’re working on it and then publish it at a later time. Or let’s say a policy has become out of date and you want to edit the policy before republishing it. In such cases you mark the policy inactive and make the required changes. Only after you activate the policy, it will be available for scanning and reporting.
When you deactivate a policy:
– No posture evaluation will take place for the policy
– The policy will be hidden from your dashboard, reports and exceptions
– Any policy report schedules for the policy will be deactivated
– The policy will be removed from compliance scorecard reports
– The policy will be removed from option profiles (with the Scan by Policy option enabled)
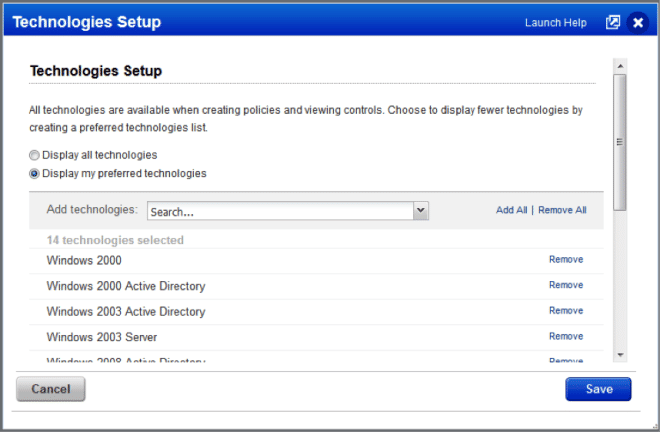
View Preferred Technologies with Configurable Account Filters
You can now hide technologies that you do not use on a regular basis. By hiding these technologies, you no longer need to go through the whole list of all the available technologies to select the ones you want. This is especially useful while searching controls by technologies. Only the controls related to the preferred technologies are displayed and are available for search.
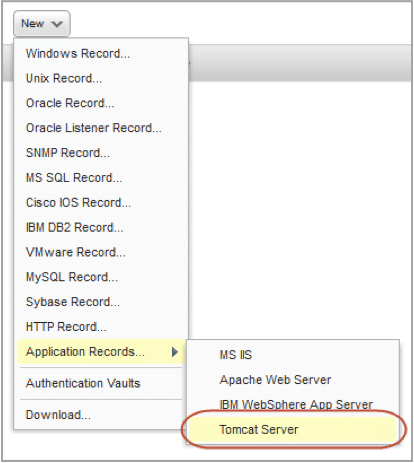
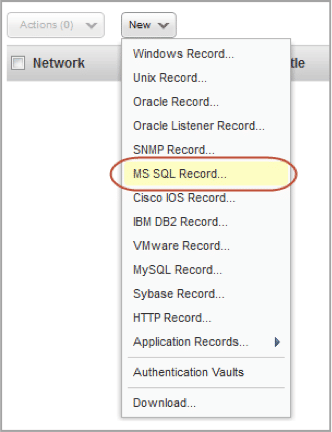
Platform Support for Apache Tomcat and Microsoft SQL Server 2014
We now support compliance scans for tomcat servers running on Unix hosts. Simply create a new Tomcat Server authentication record with details about your Tomcat installation and instance. Unix authentication is required so you’ll also need a Unix record for the host running the server.
Instance-based support has been added for Microsoft SQL Server 2014. You will use the same Authentication Records and configuration as you have in the past for older supported versions of Microsoft SQL Server.
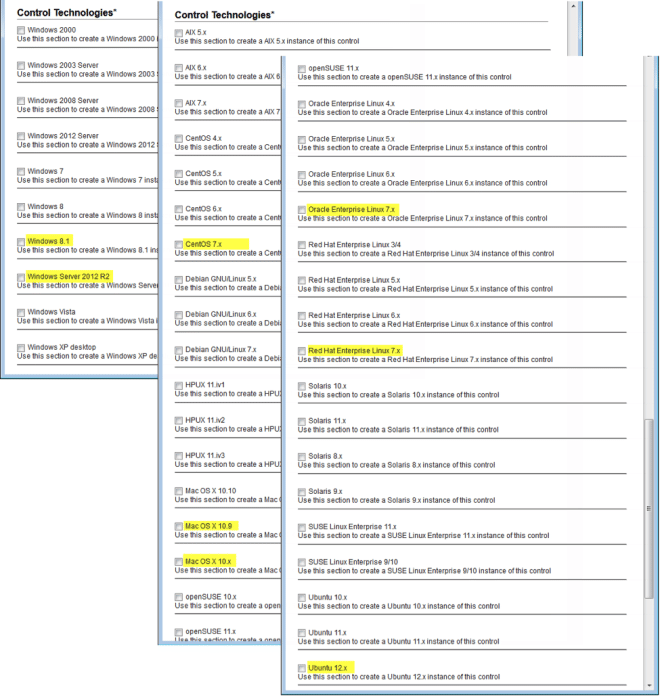
Extended UDC Support for New Technologies
These technologies are now supported for user defined controls:
- Windows 8.1
- Windows Server 2012 R2
- Mac OS X 10.10
- Mac OS X 10.9
- Red Hat Enterprise Linux 7.x
- Oracle Enterprise Linux 7.x
- CentOS 7.x
- Ubuntu 12.x
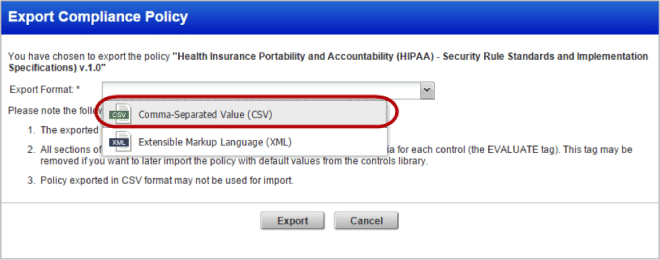
Export Policy Configuration Details to CSV
You can now export a policy to your local system in CSV format. This lets you quickly and easily share the policy and compare it to other policies you may have. A policy exported in CSV format will display information about Sections, Controls and Expected values.
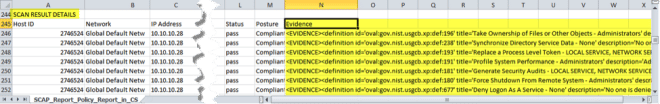
Evidence Details Added to SCAP CSV Report
Evidence Details have been added to the SCAP CSV Report. By reviewing the evidence you can determine why a rule passed or failed for a host. The evidence content includes nodes (definitions and test sections) that represent the logic of the rule and the scan tests performed on the host
Example:
<EVIDENCE>
<definition id="oval:gov.nist.usgcb.xp:def:45" title="Access Audit for Global System Objects Disabled" description="Audit the access of global system objects is disabled" result="Pass"/>
<AND result="Pass">
<definition id="oval:org.mitre.oval:def:105" title="Microsoft Windows XP is installed" description="The operating system installed on the system is Microsoft Windows XP." result="Pass"/>
<test id="oval:gov.nist.usgcb.xp:tst:9" comment="Registry key HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Control\\Lsa\\AuditBase Objects matches oval:gov.nist.usgcb.xp:var:45" result="Pass">
<expected>type : reg_dword ^(0|1)$</expected>
<actual>HKEY_LOCAL_MACHINE System\CurrentControlSet\Control\Lsa AuditBaseObjects reg_dword 0 32_bit </actual>
</test>
</AND>
</EVIDENCE>Release Schedule
For release notifications containing details specific to each platform, including the release date, and to subscribe to release notifications for your platform, please see the following:
- <span style="text-decoration: underline;"><span style="color: #0066cc;">Qualys Cloud Suite 8.5 Release Notification – Available Monday, August 10, 2015 on US Platform 1</span></span>
- <span style="text-decoration: underline;"><span style="color: #0066cc;">Qualys Cloud Suite 8.5 Release Notification – Available Tuesday, July 28, 2015 on US Platform 2</span></span>
- <span style="text-decoration: underline;"><span style="color: #0066cc;">Qualys Cloud Suite 8.5 Release Notification – Available Thursday, July 30, 2015 on EU Platform</span></span>