New Exploit Sources Added to Vulnerability Management
Table of Contents
As a comprehensive vulnerability management solution, Qualys VMDR uses several indicators to detect and mitigate exploit-related threats. Thanks to Real-time Threat Indicators (RTIs) and threat intelligence feeds, you can detect and respond to exploits in real-time.
RTIs provide comprehensive insight into your IT environment’s security posture by mapping exploits. Identifying the vulnerabilities most likely to be exploited can help you prioritize your remediation efforts and reduce the overall risk of a successful attack.
In addition to RTIs, VMDR integrates with various threat intelligence feeds to provide real-time information on emerging threats, enabling you to detect and respond to exploits as they occur.
VMDR also offers Qualys TruRisk for accurately measuring cyber risk based on multiple contributing factors, including CVSS Base Score, CISA Known Exploitable Vulnerabilities, Exploit Code Maturity, Real Threat Indicators (RTI) and Exploit Type, Malware, Threat Actors, and Trending Risk.
TruRisk evaluations use exploit code maturity to assess the exploitability of a given vulnerability. This could be a Proof-Of-Concept (POC) indicating a theoretical exploit exists, or it may already work against systems or be weaponized. In the latter case, the exploit code is considered very mature and can easily compromise a system. The algorithm rates weaponized exploits higher than POC exploits. Over 190,000 CVEs are tracked from 25+ exploit and threat intelligence sources, such as Canvas, Metasploit, ExploitDB, and many others.
What’s New?
In the upcoming release, we are introducing significant enhancements related to exploitability information that will benefit you in several ways:
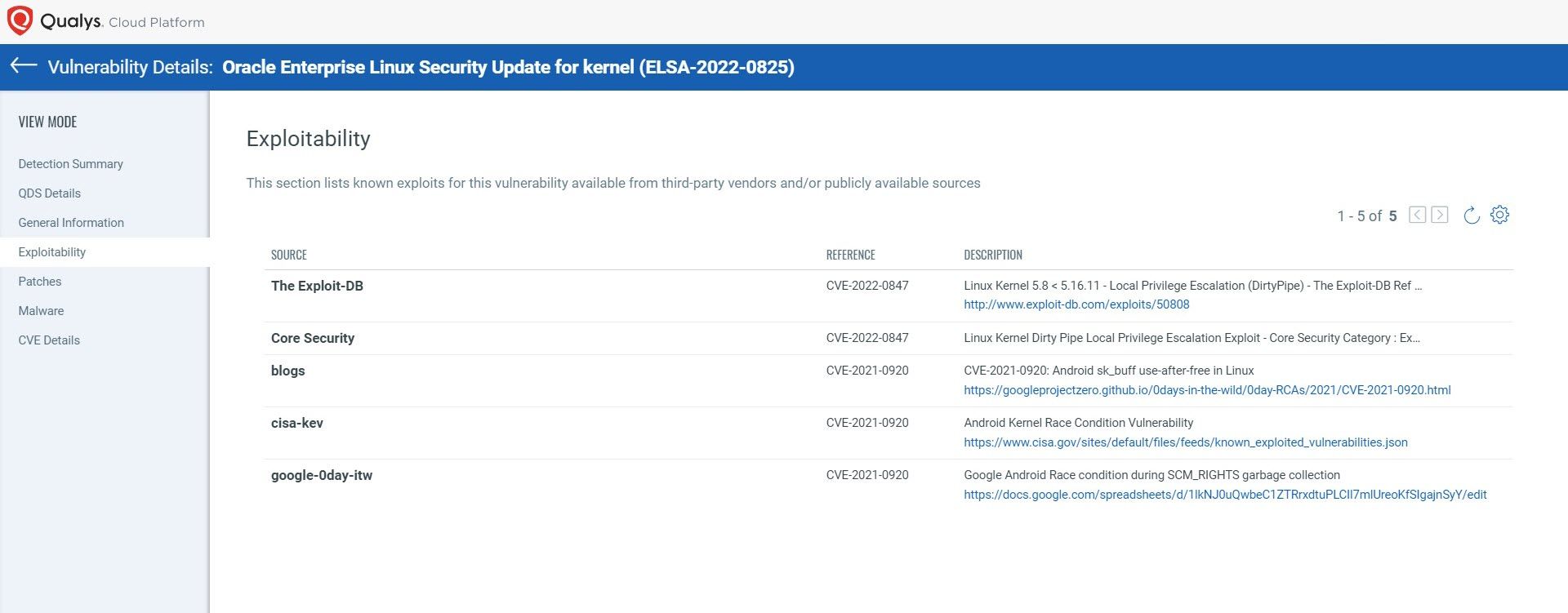
- To increase transparency, exploits will now be mapped to vulnerabilities or QIDs. You can view exploits for a particular vulnerability in the vulnerability details.
- Several new exploit sources are being integrated to enrich the exploitability information for vulnerabilities. This will allow you to prioritize vulnerabilities more effectively.
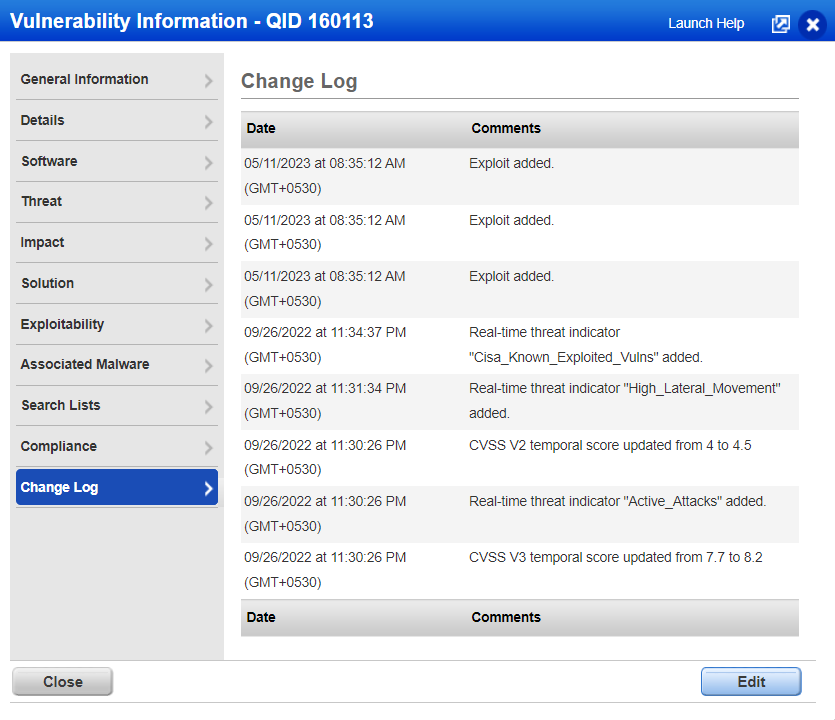
You can review the change logs to confirm the addition of new exploit sources:
What Impact Do These Enhancements Have on You?
The following are some changes that might result from these enhancements:
- There may be an increase in the number of RTIs mapped to Easy Exploit, Exploit Kit, Exploit Kit Name, Public Exploit, and Public Exploit Name and their associated vulnerabilities. This increase will also be reflected in VMDR Prioritization when applying RTIs.
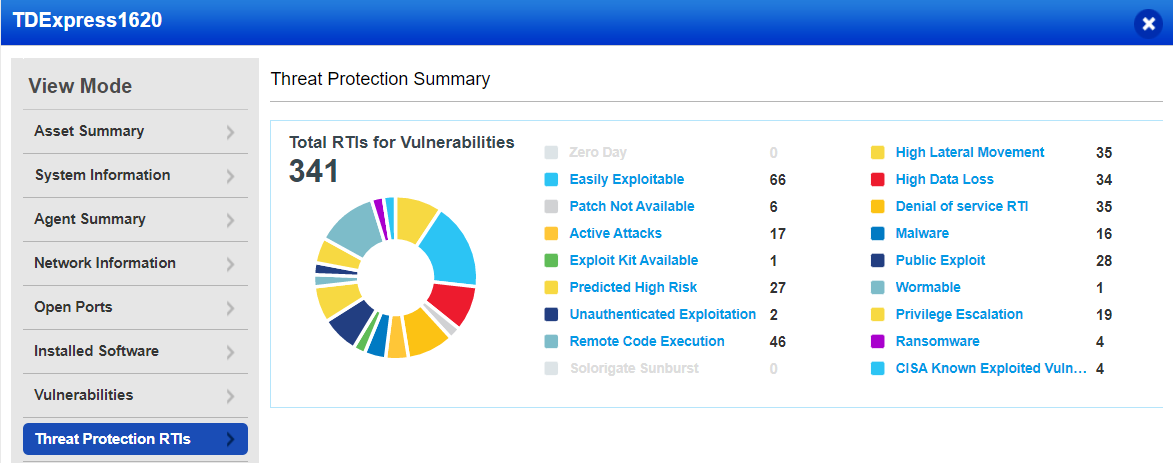
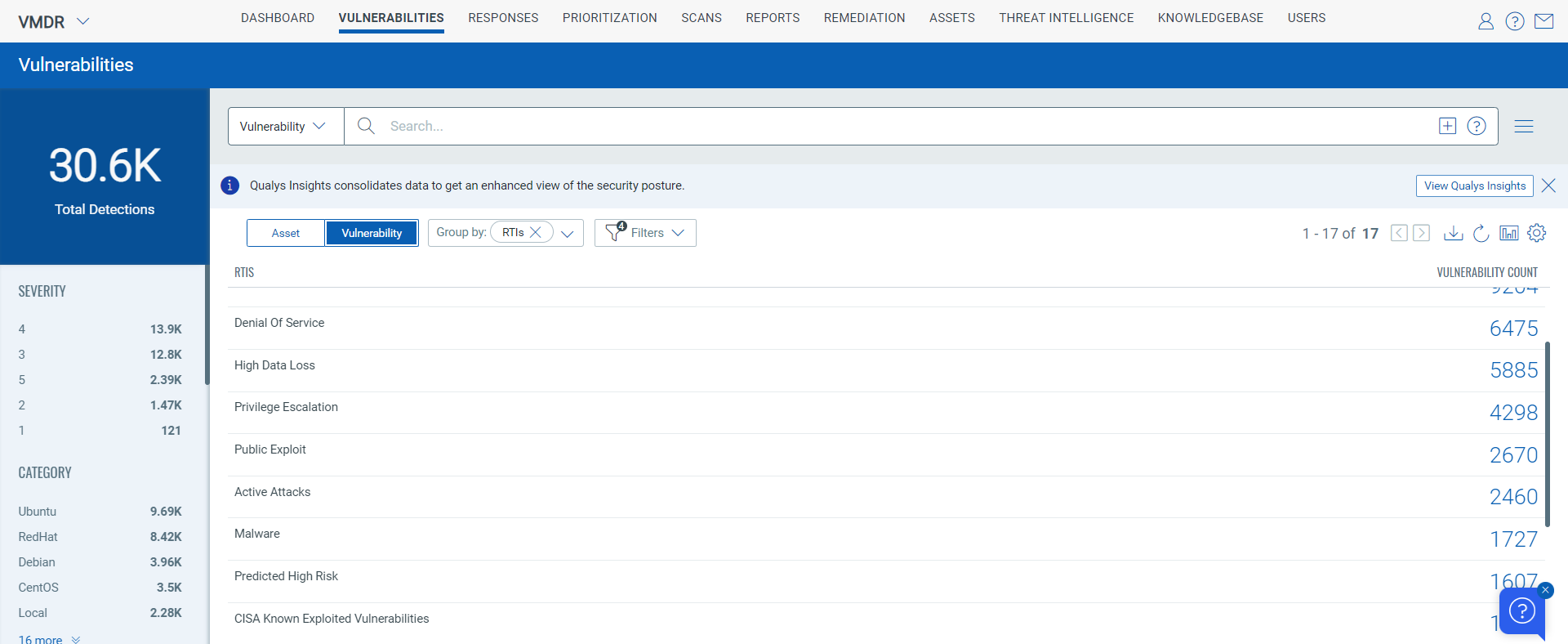
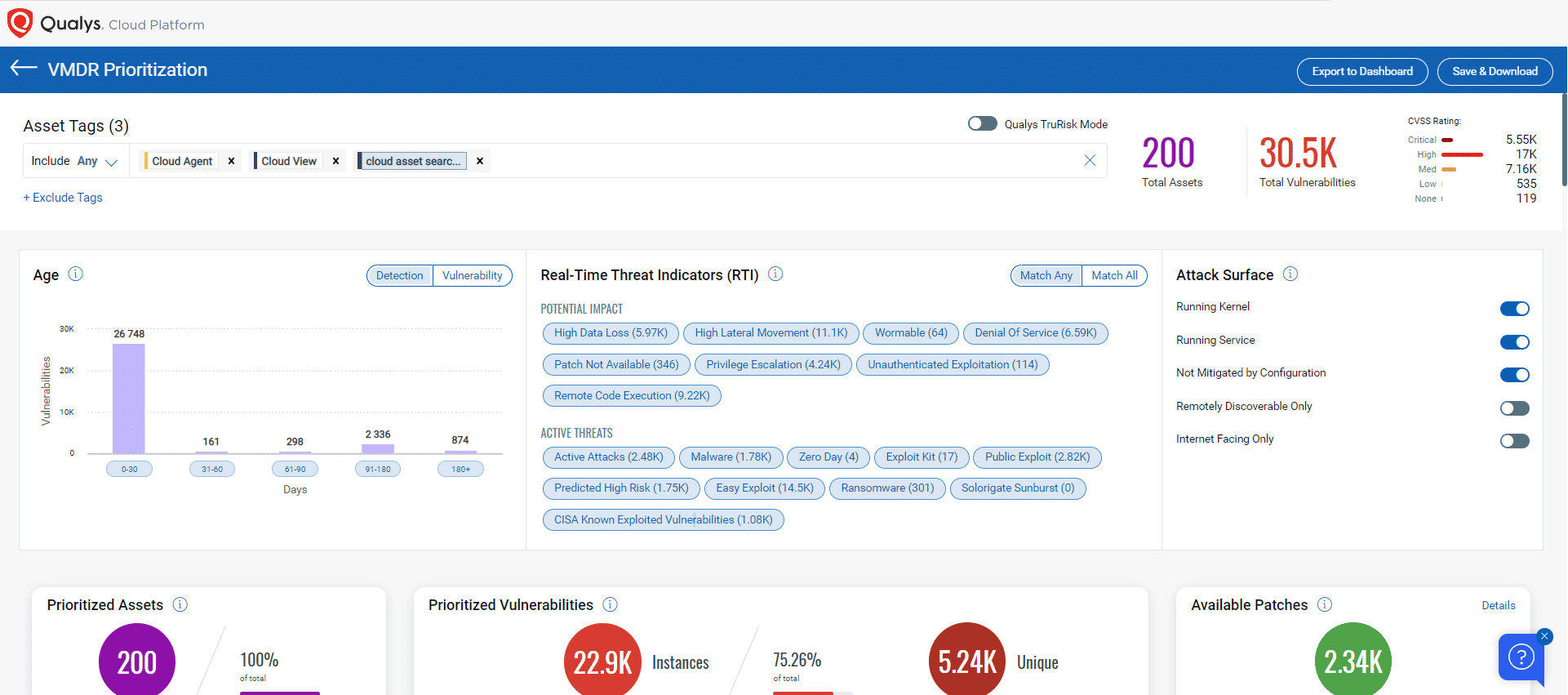
- New exploit sources may increase the number of Medium-rated feeds in the Threat Protection application.
- There may be an increase in the number of QIDs with the Exploit Available flag in the Knowledgebase.
- Vulnerability reports such as Scan Results and Host-based/Scan-based template reports will contain more vulnerabilities with exploitability mappings. This can be observed in the Exploitability column of the report.
If you have any questions regarding these improvements or would like to learn more about them, contact your Technical Account Manager or Qualys support.
See Also,
This is a welcome update, long overdue. Given the Exploit sources are known, may I ask why Qualys chose not to include the Exploit Source information in the change log?
For example, the second image above (change log image) suggests three (3) exploitability-related information updates, but there are five (5) sources in the first image (QID exploitability tab). How does the user determine which three (3) of the five (5) were newly added?