Qualys TotalCloud Kubernetes & Container Security
1.33 Release Updates
The 1.33 Release will deliver exciting features with improved Kubernetes visibility, better vulnerability prioritization, and admission controller checks during deployment time
New Kubernetes Inventory
Qualys is releasing a cluster sensor collects real-time, comprehensive inventory data, including information on namespaces, pods, and containers. This feature significantly enhances both visibility and security assessments by providing continuous, in-depth, and real-time insights into the state of your Kubernetes environment. This proactive approach helps maintain a secure, compliant, and efficient Kubernetes infrastructure.
Improved Visibility
- Real-Time Monitoring: Sensors can continuously monitor and report on the state of your Kubernetes environment, providing up-to-date information on deployments, pods, containers and other resources.
- Comprehensive Inventory: Maintaining a comprehensive inventory of all Kubernetes resources, including their configurations, relationships, and states. This detailed visibility is crucial for risk prioritization purposes.
To prioritize security risks, users filter production clusters by using cluster metadata such as cluster name, cloud providers or cloud resource name such as AWS ARN. Once those clusters are pre-selected, users select the workloads that are relevant by filtering the namespace, or pod names as shown in the screenshot below.
Improved Security Assessments
- Vulnerability Detection: By continuously collecting the Kubernetes inventory, sensors can identify vulnerable images, outdated images that could be exploited by attackers.
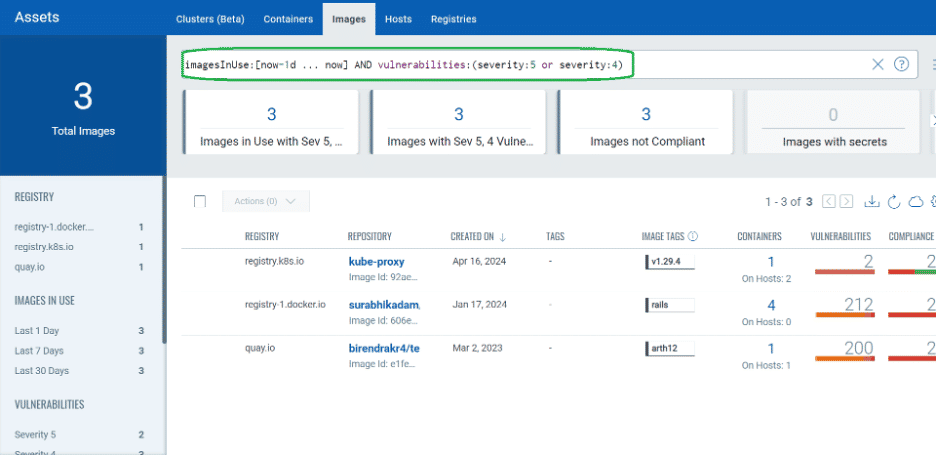
Image-in-Use: Focus on potentially exploitable vulnerability
Navigating through numerous vulnerabilities in container images can be overwhelming. Effective prioritization of these vulnerabilities requires a strategic approach.
The “Image-in-use” feature streamlines this process by helping you focus on the most critical vulnerabilities, enabling you to prioritize and address those that have the highest impact on your runtime environment.
Container image vulnerability management can be daunting due to the sheer volume of potential issues. Effective prioritization is key to addressing the most critical vulnerabilities first.
Our “Image-in-Use” feature cuts through the noise by highlighting vulnerabilities in actively deployed container images. This targeted prioritized approach allows you to:
- Identify high-impact vulnerabilities in your runtime environment
- Prioritize remediation efforts based on actual usage
- Allocate resources more efficiently
By concentrating on vulnerabilities in images currently in use, you can significantly improve your security posture where it matters most—in your active production workloads.
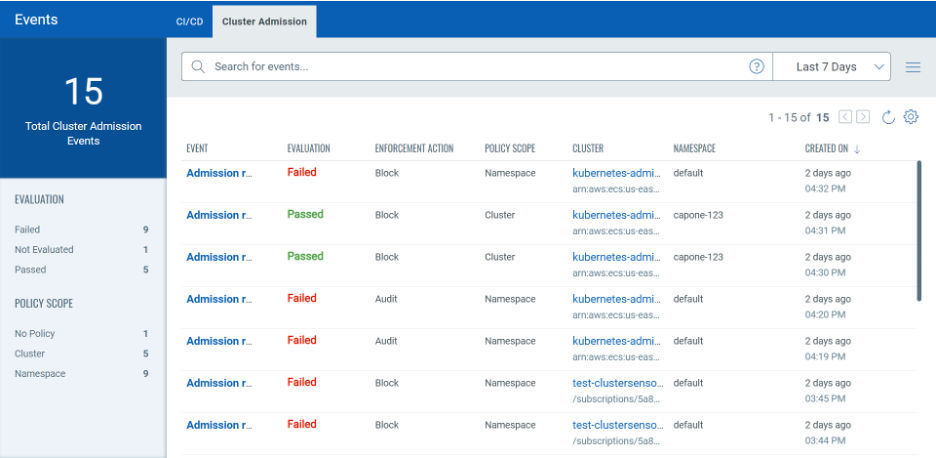
Kubernetes Admission Controller
Qualys K8s Admission control is a powerful proactive security tool that enforces your organization policies on Kubernetes resources and ensures your K8s environment is compliant to your organization policies. This intercepts K8s API requests and evaluates the policies before the Kubernetes resources persist.
Qualys admission control also audits your existing K8s resources when Policies are newly enforced or new policies are introduced. This ensures only compliant resources exist in your K8s minimizing security risks.
Depreciation of Container Runtime Security v1.0
Qualys will discontinue support for Container Runtime Security (CRS) v1.0 in the 1.33 release. In the coming weeks, we will introduce Container Runtime Security (CRS v2.0) based on the latest eBPF technology. We look forward to share details about this upcoming release soon.
If you have any questions, please don’t hesitate to contact our support team. We appreciate your understanding and cooperation as we continue to improve our products and services.
Resources
- Learn more about TotalCloud Container Security
- Online Help for TotalCloud Container Security
- Important Announcement: Container Runtime Security (CRS) v1.0 End of Life
- If you have questions, please contact your TAM or Qualys Technical Support.
Contributors
- Siban Mishra Principal Technical Product Manager