Upcoming Changes in Admission Controller and CI/CD Policies: Kubernetes and Container Security 1.36
Release Date: Mid-February 2025
Exact dates will be available on Qualys Status page – Upcoming Maintenance Tab for details.
Product Update: Kubernetes and Container Security – Version 1.36
Summary
The Kubernetes and Container Security Team is announcing the upcoming release of Kubernetes and Container Security version 1.36. This release introduces enhancements to Kubernetes Admission Controller and CI/CD policies using QScanner. The focus is on strengthening security enforcement and improving compliance management.
Who Benefits from These Updates?
This update is applicable for users who use Qualys – Kubernetes Admission Controller and CI/CD Security using QScanner for enforcing security measures.
Users leveraging the CI/CD Sensor are NOT affected by these changes and can continue using their existing setups without modifications.
What’s New?
1. Pod Security Policies for Admission Controller
Pod Security Policies enforce compliance with organizational security standards by:
- Enhance isolation and security by blocking host process containers, shared namespaces, privileged containers, HostPath volumes, and host ports.
- Reduce attack surface with secure configurations by limiting capabilities, enforcing default /proc mounts, and preventing privilege escalation.
- Strengthen protection with non-root containers and minimize risks of host-level vulnerabilities.
These policies simplify security enforcement while maintaining flexibility for development workflows.
Note: Upgrading to the (1.1.0) version of the Admission Controller is essential to unlock these capabilities.
2. Image Security Policies for Admission Controller and CI/CD Security using QScanner
Image Security Policies ensure secure and compliant container images by:
- Prevent deployment of images with vulnerabilities, and embedded secrets to safeguard your environment (Currently, blocking embedded secrets is supported exclusively through the Admission Controller.)
- Strengthen security by limiting vulnerabilities by severity or CVSS, and blocking known issues with QIDs or CVEs.
- Maintain compliance by enforcing detection score thresholds and restricting unauthorized or untrusted images.
3. Simplified Policy Rule Action
What is Rule Action?
Rule actions determine whether a resource complies with security standards and defines the response:
- Pass (formerly Allow): Approves resources that meet security standards.
- Fail (formerly Deny): Blocks resources that do not meet security standards.
This renaming improves clarity and aligns with stricter compliance enforcement.
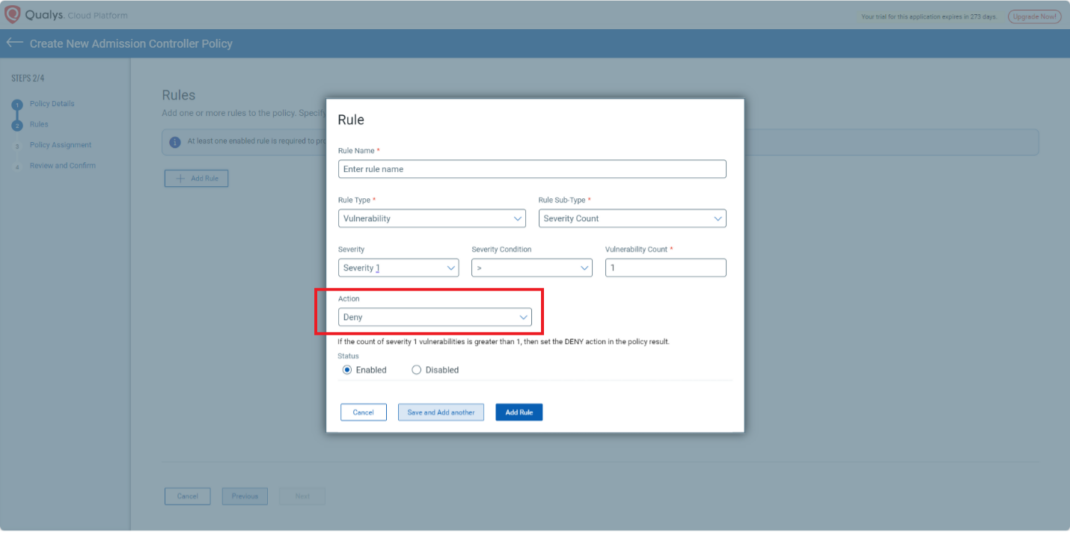
Default Rule Action
Rules now default to “Fail.” Rule actions are no longer configurable to simplify decisions and enforce strict compliance.
Why is the default action ‘Fail’?
We found that users occasionally created unintended rules that permitted resources with critical vulnerabilities. Since rules are inherently negative in nature, a rule failing to meet security standards indicates an issue. Permitting such resources contradicts security principles. By setting ‘Fail’ as the default, we enforce stronger security and reduce the risk of errors caused by ambiguous configurations.
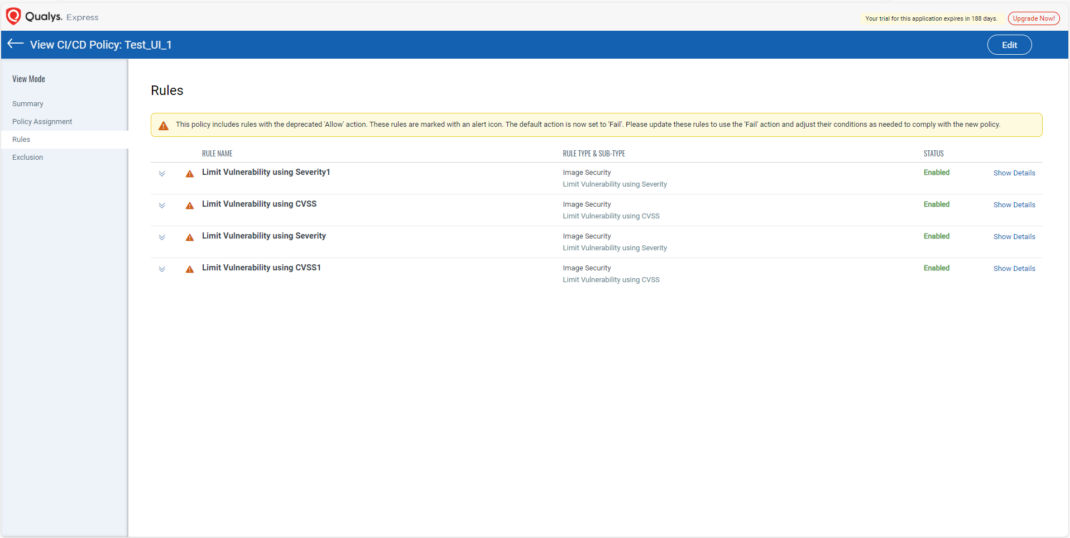
Impact on Existing Policies
- Existing policy rules using “Allow” actions will automatically be treated as “Fail.”
- Users should review and test policies to ensure compliance and avoid disruptions.
Policies that previously allowed risky resources, like “passing the CI/CD build with vulnerabilities”, contradicted security practices. This update enforces strict compliance and removes ambiguities to strengthen security.
Action Required
Note: These changes do NOT affect users who are using the CI/CD Sensor.
CI/CD Policies can only be used with new QScanner-based CI/CD Security.
To know more about QScanner please visit: Elevate Your Container Security with QScanner in 2025.
CI/CD and Admission Policies
Once version 1.36 is published, you can revisit your rules. We will highlight policies that may have potential misconfigurations, making them easier to identify and fix. These highlights will be available on the policy detail page.
Admission Controller
This release significantly enhances the Admission Controller, including new rules, performance improvements, and minor fixes to boost stability and reliability.
We recommend you to upgrade your Qualys Admission Controller to 1.1.0
Compatibility Matrix for Admission Controller Version
| Feature | 1.0.0 | 1.1.0 (Upcoming with CS 1.36) |
| New Pod Security Rules | ❌ | ✅ |
| New Image Security Rules | ✅ | ✅ |
Need Help?
Our support team is ready to assist you with this update. Whether you need help with configurations, rule evaluations, or upgrading your Admission Controller, we’re here to help. You can contact our dedicated support team through the Qualys Support Portal.
We are excited to introduce these new and advanced policies!
Stay tuned for a blog announcement that will provide detailed insights into the new features.
– Kubernetes and Container Security Team