Key Changes in SSL Labs Grading and Qualys CertView
In today’s fast-paced digital landscape, managing SSL/TLS certificates can often feel overwhelming and time-consuming. That’s where Qualys CertView steps in for a robust tool designed to simplify certificate management across your organization. With CertView, you gain real-time visibility into your certificate inventory and assessment, making monitoring expiration dates and compliance status easy. Qualys CertView Assessment offers a comprehensive evaluation of your SSL/TLS certificates, assigning grades based on their security and configuration, helping you identify areas for improvement in a clear and understandable way. Automated alerts and reporting features help reduce the risk of downtime caused by expired certificates, ensuring your operations run smoothly.
What truly sets CertView apart is its integration with Qualys VMDR (Vulnerability Management, Detection, and Response), which enhances certificate management while bolstering your overall security posture. This powerful combination enables you to proactively identify vulnerabilities associated with your certificates and respond swiftly to potential threats. Together, they provide a comprehensive solution to safeguard your digital assets.
Additionally, CertView allows you to launch scans for both internal and external sites, giving you a complete view of your certificate landscape. Elevate your security strategy with the combined power of Qualys CertView and VMDR, ensuring your organization remains secure and compliant in an ever-evolving digital world.
Major Grade Changes in CertView and SSLLabs (Effective Post-March Release)
- Removal of TLS_FALLBACK_SCSV from Grading
Previously, a warning was issued for not supporting TLS_FALLBACK_SCSV. Moving forward, this will no longer impact your grade, simplifying the grading criteria.
- Increased Importance of TLS 1.3
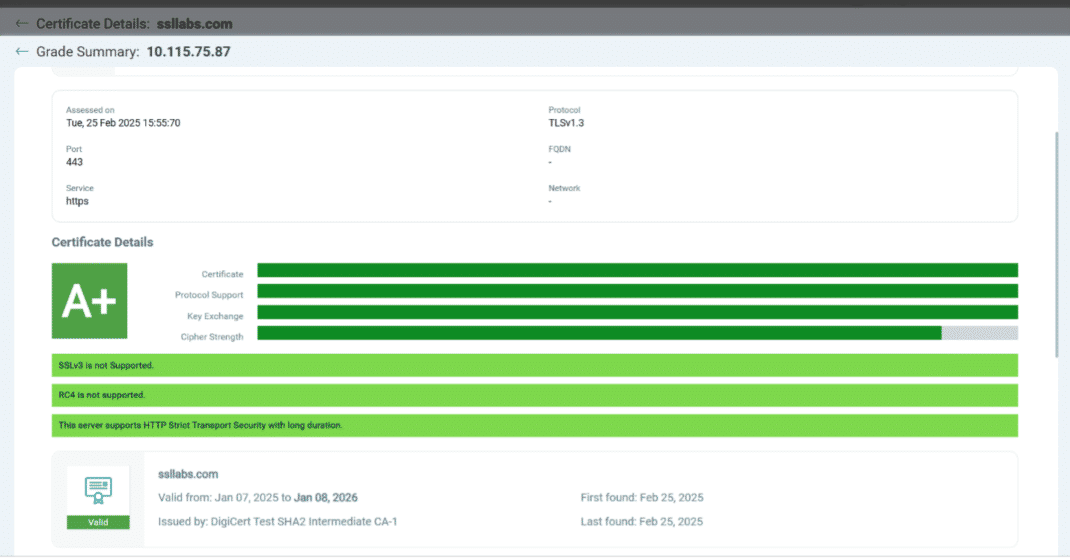
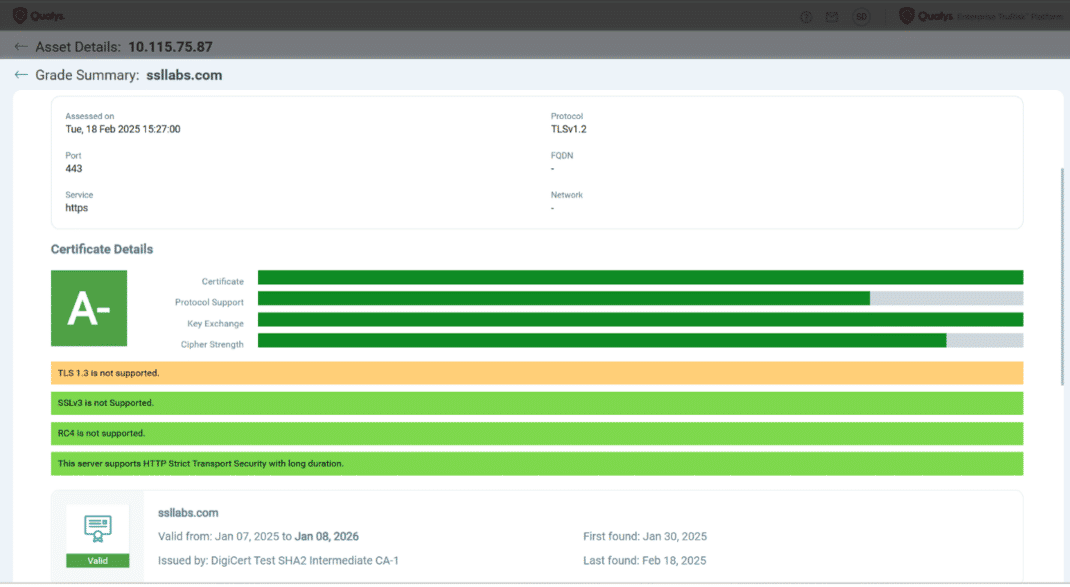
TLS 1.3 is now given higher weight in the grading system. If your server does not support TLS 1.3, you will receive a warning, and your minimum grade will be capped at ‘A-‘. This means that not supporting TLS 1.3 will automatically result in a minimum grade of ‘A-‘. TLS 1.3 is now considered a 100% protocol strength.
- HSTS Status Impact
If HTTP Strict Transport Security (HSTS) is disabled or invalid, your grade will drop from an ‘A’ to ‘A-‘. This change emphasizes the importance of HSTS in maintaining secure connections.
Existing CertView & SSLLab Grading Structure
| Grade | Description |
|---|---|
| A+ | Excellent security with strong configurations |
| A | Good security, minor issues present |
| A- | Acceptable security, some significant issues |
| B | Fair security, multiple issues identified |
| C | Poor security, major vulnerabilities present |
| F | Unacceptable security, immediate action needed |
Deep-Dive into the Expected Changes
Elevating Security with (Transport Layer Security) TLS 1.3
TLS 1.3 is essential for modern security, offering stronger protection by eliminating outdated cryptographic methods and enhancing data transmission safety. Its streamlined handshake process results in faster connections, improving user experience. The protocol simplifies management by reducing complexity, making compliance with security best practices easier. With mandatory forward secrecy, it ensures that past communications remain secure even if a private key is compromised. Additionally, adopting TLS 1.3 helps organizations meet regulatory requirements, avoiding potential penalties. Overall, transitioning to TLS 1.3 not only boosts security but also prepares organizations for the evolving digital threat landscape.
The importance of adopting TLS 1.3
As major browser vendors like Google, Microsoft, Mozilla, and Apple phase out TLS 1.0 and TLS 1.1, it’s time to embrace TLS 1.3, the latest and most secure version. Here are some key reasons to upgrade and make the switch:
- No Downgrade Attacks: TLS 1.3 eliminates the risk of downgrade attacks, enhancing security.
- Stronger Cipher Suites: It excludes outdated and insecure cipher suites like RC4 and DES, ensuring only robust options are available.
- Designed for Security: Built from the ground up, TLS 1.3 addresses previous vulnerabilities, offering a more secure protocol.
- Improved Performance: With 1-RTT for initial connections and 0-RTT for session resumption, TLS 1.3 reduces latency and speeds up connections.
- Simplified Cipher Suite Selection: It uses just three cipher suites, all featuring perfect forward secrecy and modern encryption methods, making security clearer and more reliable.
- Enhanced Privacy: TLS 1.3 improves privacy by minimizing the amount of cleartext protocol information transmitted, which helps prevent protocol ossification and supports future TLS versions. It also hides content length, reducing the visibility of user information on the network.
- Confidential Client Authentication: Unlike previous versions, where client authentication could expose identity unless renegotiated (adding extra round trips and CPU costs), TLS 1.3 ensures that client authentication is always confidential.
Understanding SCSV (Signaling Cipher Suite Value)
SCSV (Signaling Cipher Suite Value) is a security feature that helps prevent downgrade attacks during the TLS handshake, ensuring that connections remain secure by signaling supported cipher suites. Qualys CertView & SSLLabs previously issued warnings for not supporting TLS_FALLBACK_SCSV, which could affect your security grade. However, this will no longer impact your grade, simplifying the grading criteria and allowing you to focus on more critical security aspects.
What is TLS_FALLBACK_SCSV?
TLS_FALLBACK_SCSV (Hex value 0x5600) is a cipher suite designed to prevent “Protocol Downgrade Attacks.” These attacks occur when a malicious actor, often referred to as a Man-in-the-Middle, interferes with the TLS handshake, forcing a connection to use a lower or less secure protocol version. For instance, downgrading from TLS 1.2 to TLS 1.1 is undesirable, especially when both the server and client support a higher version.
The Shift with TLS 1.3
With the higher precedence of TLS 1.3, the requirement for using TLS_FALLBACK_SCSV for downgrade attack prevention has been removed. This means that for servers supporting only TLS 1.3, QualysCertview & SSLLabs does not check for TLS_FALLBACK_SCSV, and its absence is not considered an exceptional configuration in grading. While TLS_FALLBACK_SCSV played a crucial role in earlier versions of TLS, its relevance diminishes with the adoption of TLS 1.3, allowing organizations to focus on more pressing security concerns without the worry of downgrade attacks.
HTTP Strict Transport Security (HSTS):
HTTP Strict Transport Security (HSTS) is essential for securing your website by ensuring that browsers only connect via HTTPS, preventing potential man-in-the-middle attacks. In Qualys CertView & SSLLabs, if HSTS is disabled or invalid, your security grade will drop from an ‘A’ to ‘A-‘, highlighting the importance of this feature. To fix this, ensure your web server sends the correct HSTS header, such as Strict-Transport-Security: max-age=15779000; includeSubDomains, which enforces secure connections for 6 months. Regularly you need to check your HSTS status in CertView to maintain a strong security posture.
Comparison of Certificates Supported with TLS 1.2 and TLS 1.3: Grade Changes
When comparing certificates, it’s crucial to recommend TLS practices that prioritize modern, secure protocols like TLS 1.3, as they offer stronger encryption and improved performance over older versions like TLS 1.2. This shift not only enhances security but also ensures compliance with industry standards, ultimately protecting sensitive data more effectively.
| Server Configuration Supporting Recommended TLS Practice | Grading Structure | ||||
| TLS.1.1 | TLS.1.2 | TLS1.3 | HSTS status impact | Existing Grades (Before March 2025 Release) | Expected Grades (Post March 2025 Release) |

|

|

|

| B | B |

|

|

| A+ | A+ | |

|

|

| B | B | |

|

| A+ | A+ | ||

|

|

| B | B | |

|

| A+ | A- | ||

|

| B | C | ||

|

|

| B | B | |

|

| A- | A | ||

|

| B | B | ||

| A- | A- | |||

|

| B | B | ||

| A- | A- | |||

| C | C | |||
These recent updates to SSLLabs and CertView emphasize the increasing focus on modern security standards. As older protocols fade, having full support for TLS 1.3 is becoming essential for maintaining top-tier security. Similarly, proper HSTS configurations are now crucial for higher grades, underscoring the importance of secure headers. The grading process now pushes administrators to adopt the latest and most robust security measures. Staying up to date with these requirements is key to ensuring a secure and trusted online environment.
Reference
- Qualys CertView
- Qualys SSL Labs
- https://www.cloudflare.com/learning/ssl/why-use-tls-1.3/
- https://securityboulevard.com/2018/12/why-tls-1-3-is-a-huge-improvement/
- https://www.cloudflare.com/learning/ssl/why-use-tls-1.3/
- https://github.com/ssllabs/research/wiki/SSL-Server-Rating-Guide