Qualys Kubernetes & Container Security: What’s New in 1.37 & 1.38
Securing modern Kubernetes and container environments requires more than just strong detection—you need clear insights that speed up remediation, enable better ownership, and help enforce policy at scale. In versions 1.37 and 1.38, we’re bringing major updates that give security and DevOps teams the context they need to act with confidence.
Remediation-Driven Vulnerability Insights
You already trust Qualys for best-in-class vulnerability detection. Now, we’re introducing deeper insights to accelerate triage, reduce mean time to remediate (MTTR), and assign ownership more effectively.
Image Layer Vulnerability Attribution
In containerized environments, not all vulnerabilities are equal—or owned by the same team.
With 1.38, you can now:
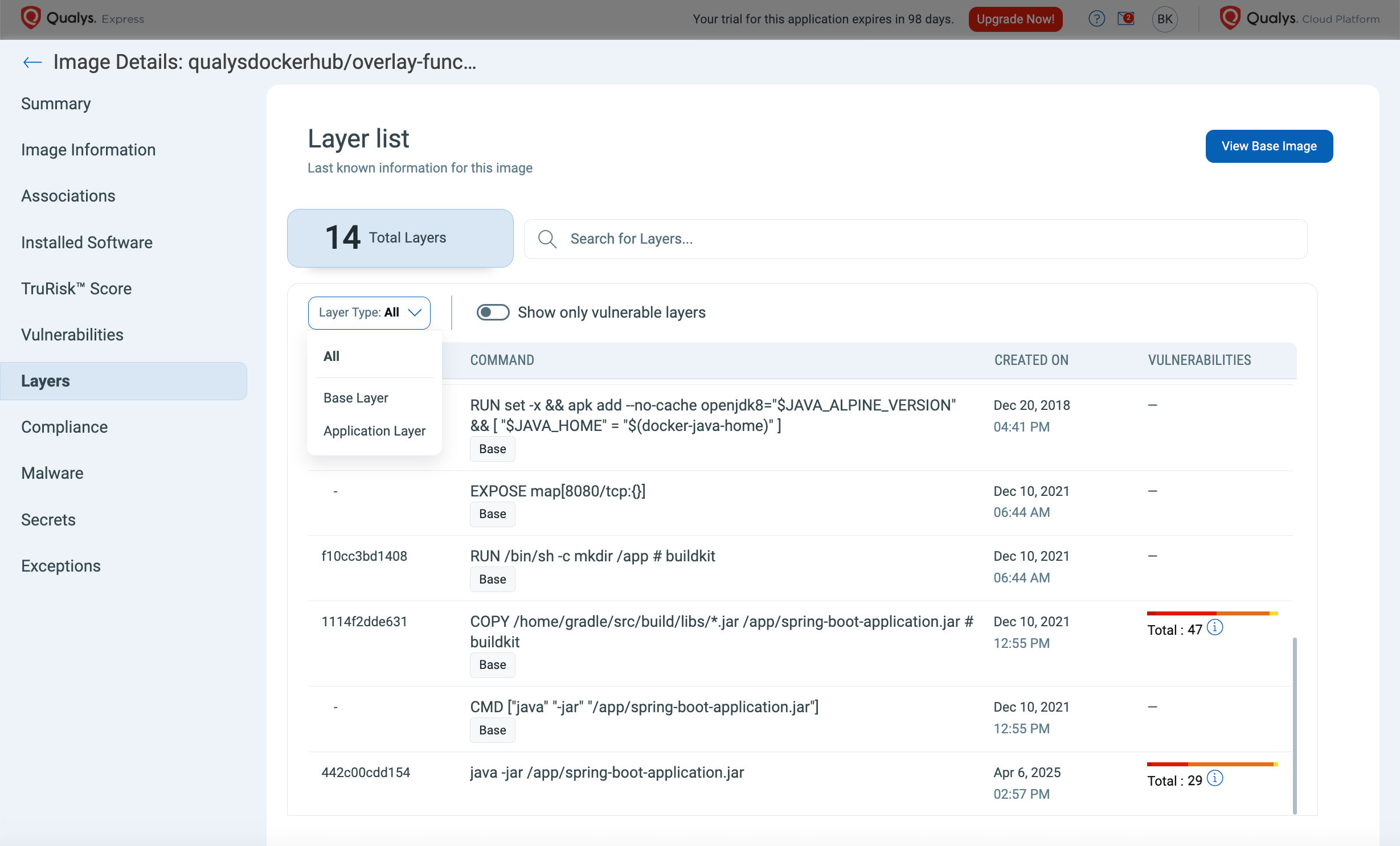
- Identify which layer of an image a vulnerability originated from—base layer (typically maintained by SecOps or platform teams) vs. application layer (owned by Devs)
- Filter by layerSha using QQL to pinpoint vulnerable base images reused across multiple services
- Align remediation workflows to the right owners and reduce finger-pointing between teams
This granular visibility helps break down silos and speeds up patching efforts across your CI/CD pipeline.
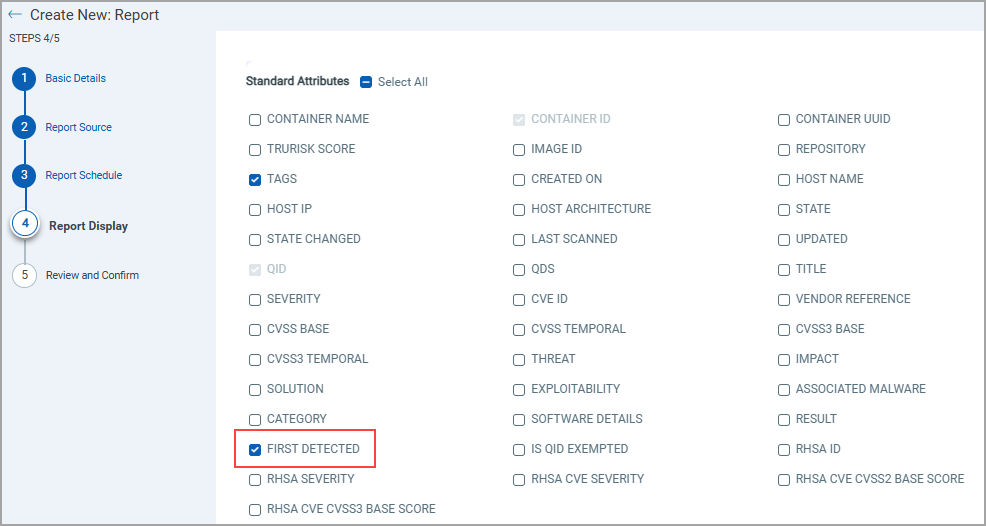
New Fields in Vuln Reports:
- Red Hat Vulnerability Scanner Details: Validate findings using Red Hat-certified metadata—especially useful for OpenShift deployments
- First Detected Date: Ensure SLA compliance by knowing exactly when a vuln was first seen
- Host Architecture Info: Know whether issues apply to x86, ARM, or other architectures for better targeting
- Ability To See Exempted Vulnerabilities: Customers can now choose whether to see exempted vulnerabilities in image vulnerability and container vulnerability reports or not
Kubernetes Security Posture Management (KSPM)
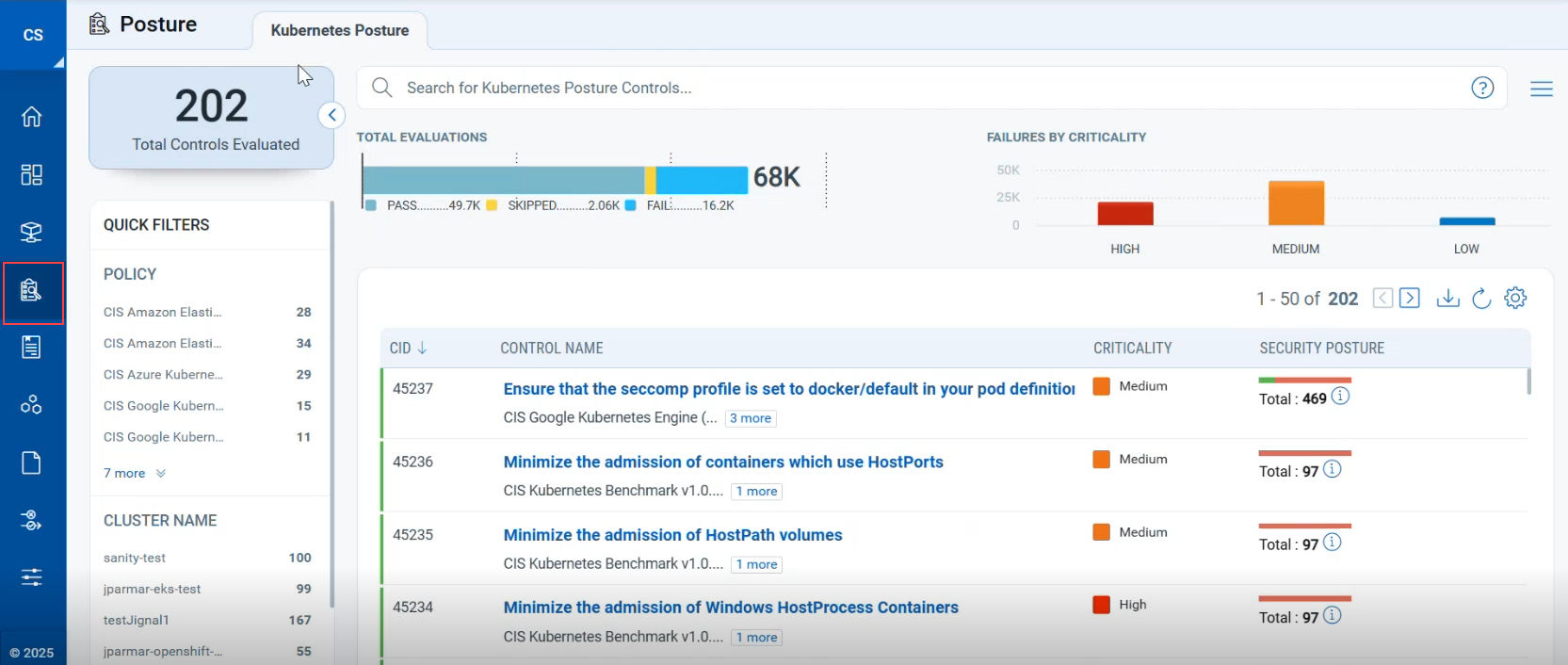
Traditional cloud compliance tools often focus only on node-level settings or CSP configurations, leaving a massive blind spot: the Kubernetes control plane and Kubernetes-native configurations. These include RBAC policies, API server configurations, admission controls, and network segmentation—many of which are misconfigured or insecure out of the box.
With Qualys KSPM, you get full visibility into these critical control layers to ensure your clusters are secure and compliant.
Why it matters:
- The Kubernetes API server is frequently exposed with permissive access
- RBAC misconfigurations grant excessive permissions across pods, namespaces, and clusters
- Network segmentation is often missing, enabling lateral movement within a cluster
- These are not covered in typical VM or cloud-focused compliance tools
What’s included:
Audit against industry-standard CIS Benchmarks for:
- Kubernetes (upstream)
- Amazon EKS
- Azure AKS
- Google GKE
- Red Hat OpenShift
Quickly identify gaps in your control plane, enforce hardening policies, and ensure continuous compliance across hybrid and managed Kubernetes environments.
Attack Path Enhancements Including Integration of Identity-Based Risks
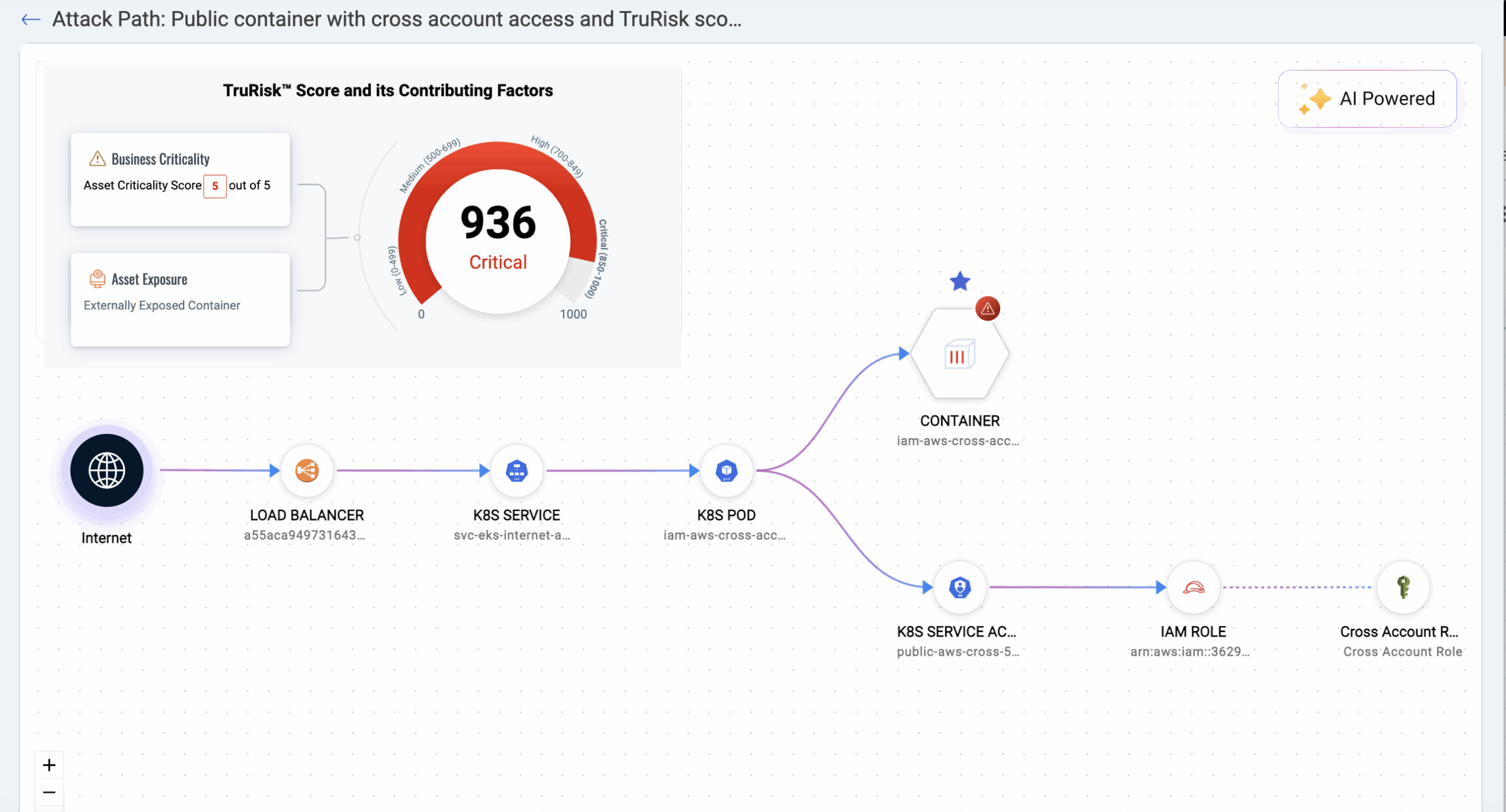
In 1.35, Attack Path was released to identify toxic combinations of risk and appropriately prioritize. Now, with 1.38 and TotalCloud 2.16, new risky combinations are being added.
Identity is the new perimeter—and Kubernetes RBAC, when over-permissive or misaligned with cloud IAM, opens real attack paths.
New in 1.38:
- Visualize paths where public-facing pods are tied to over-permissive service accounts
- Correlate Kubernetes RBAC with cloud IAM roles to reveal hidden identity risk
- See how attackers can pivot from a compromised container to critical data stores
This helps teams prioritize what’s actually exploitable over theoretical risk.
Block Older Images
Your last line of defense shouldn’t be guesswork. With enhanced admission controller policies, you can now block image deployments based on when they were created. Older images may introduce more risk and may not meet certain SLAs. In addition, with CI/CD policies and Admission Controller policies, you can block images in your dev pipelines and pre-Kubernetes deployments, respectively, including images with:
- Critical or unauthorized vulnerabilities
- Non-compliant software
- Secrets
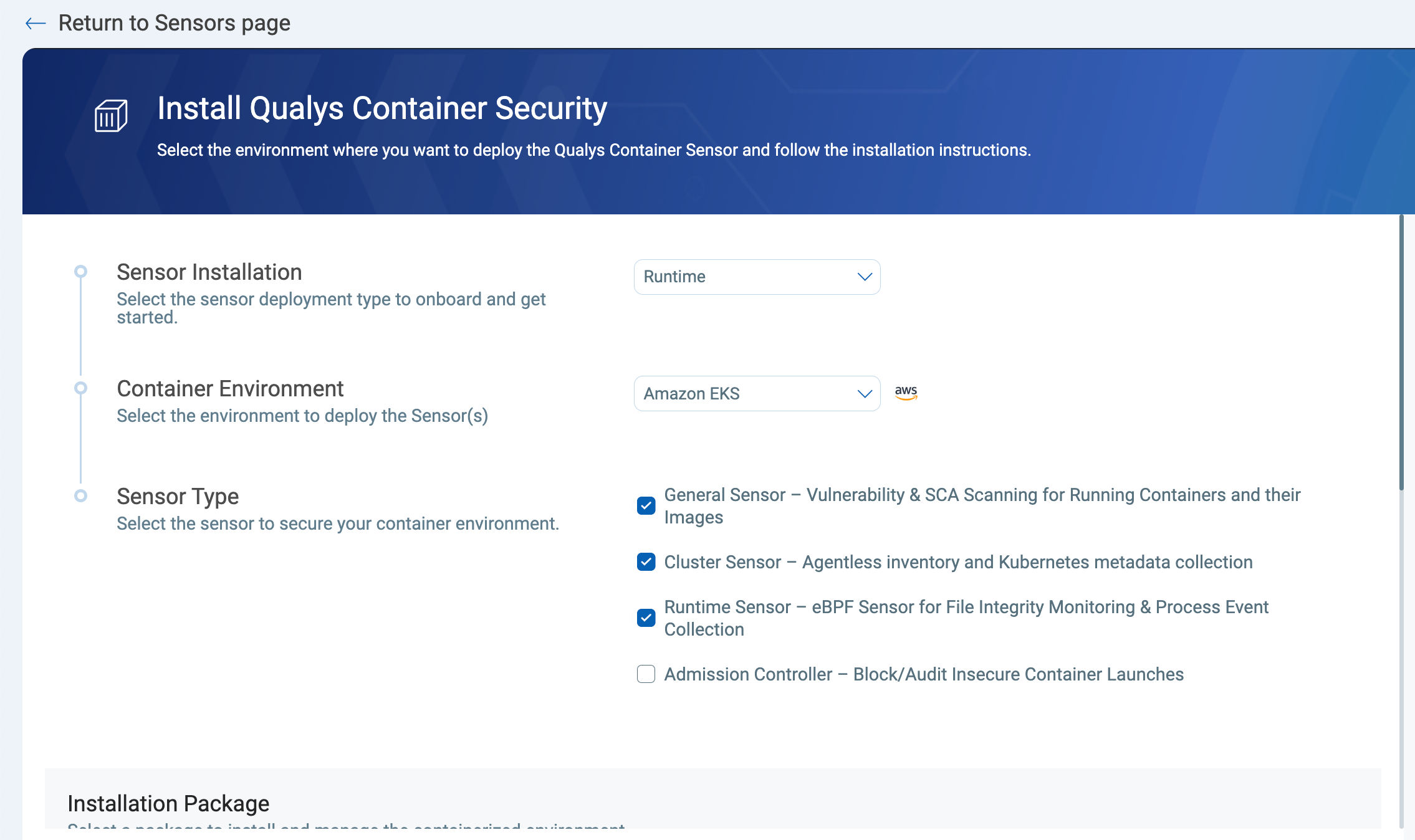
Smarter Sensor Onboarding and Platform Support
Getting started—and scaling—shouldn’t require guesswork. We’ve made onboarding and compatibility smoother across clouds and platforms.
New Sensor Onboarding Wizard
- Select your deployment environment (EKS, ECS, OpenShift, etc.)
- Automatically get the right Helm chart parameters and feature flags
- View all Helm install commands at once—no toggling needed
Sensor Enhancements (1.37 & 1.38)
- Overlay driver support for Docker runtime (previously only for containerd) → Improved scanning performance
- Support for OCI Registry scanning → Broader visibility into modern registry types
- General Sensor support for Podman → Beyond just registry scans
These releases continue our mission to help security and platform teams secure containers and Kubernetes workloads end to end—from image to runtime, from CI/CD to compliance.
Resources
- Learn more about TotalCloud Kubernetes & Container Security
- Speak to an expert about container security
- Online Help for TotalCloud Container Security
Contributors
- Siban Mishra, Principal Technical Product Manager, Qualys