Automatically Identify Internet-Facing Assets
As the volume and risk of cyberattacks continue to rise, the internet-facing devices in an organization stand out as the most vulnerable assets. Cyber threat actors are continuously scanning the internet for vulnerable systems to launch attacks and campaigns. An organization’s internet-facing systems represent much of their attack surface area. However, the efforts to identify all such assets across the organization and keeping a tab on their security could be enormous.
To address the security challenges related to these vulnerable assets in your network, Qualys has introduced an innovative way of auto-detecting such internet-facing systems based on Asset Inventory and vulnerability scanning data, so that you can prioritize their remediation.
The new system-defined tag, named Internet Facing Assets, includes pre-defined ranges of publicly routable IP addresses. This tag is automatically applied to assets with IPs that fall within the specified ranges, for all VM and VMDR customers.
With the upcoming VMDR release, users will be able to use the Internet Facing Assets tag to prioritize vulnerabilities in the VMDR reports.
The public-facing assets can be easily identified using this tag; which in turn, would help expedite the process of addressing vulnerabilities in them.
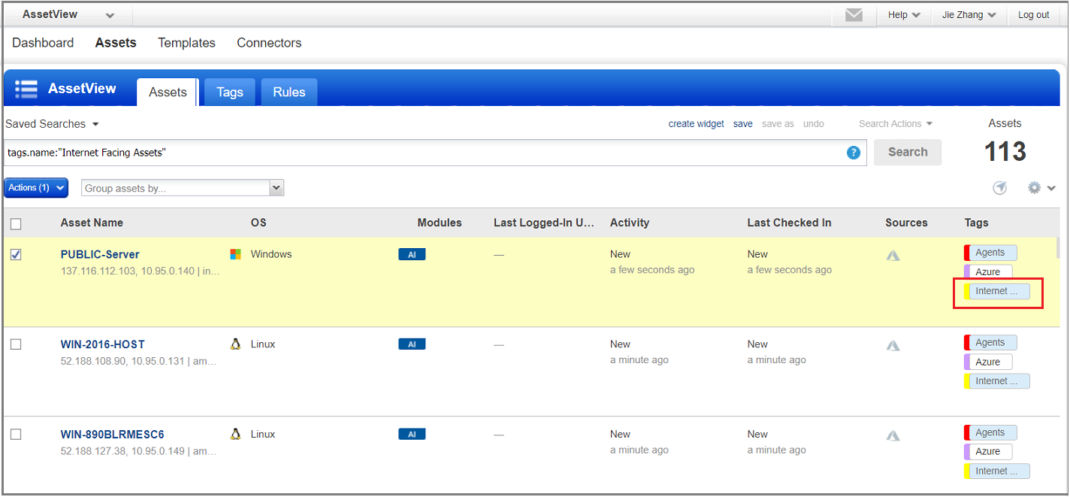
To view the range of IP addresses included in the scope of the tag, select the tag in the Assets > Tags page and then from the Quick Action menu, select View. The IP address ranges are listed in the Tag Rule tab.
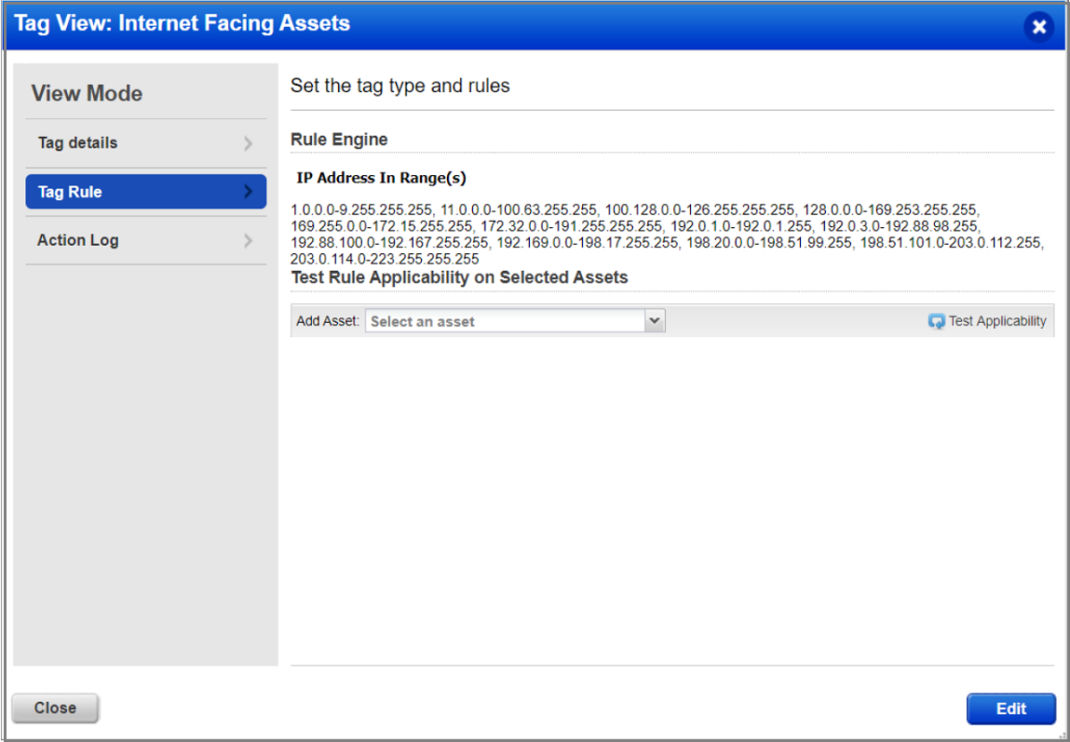
The Internet Facing Asset tag is a system-defined tag and it cannot be modified or deleted. If you need to modify the IP range as per your organization’s unique network environment or compliance requirements, you may contact your Technical Accounts Manager or the Qualys Support team.
Note: The option to edit or expand the scope of the tag from the UI will be introduced in a later release of Qualys VMDR.
The Qualys Cloud Platform v3.0.2 Release Notes have been updated with this feature information.
This is frustrating, this tag will be less than useless. Where organizations have used public addresses internally (I haven’t been at a company yet that hasn’t done this) it will incorrectly identify assets as Internet facing. As well, where traffic is NAT’ed to a host by network routing infrastructure it will not identify these as Internet facing.
A better move would have been to provide your customers guidance on how to correctly identify these assets in Qualys. Naming conventions for external scans identify the externally available surface. Pulling information from infrastructure teams or from logs of external scans would provide the internal addresses of hosts with services available by NAT.
This is just another step I will be required to take to clean the Qualys data of false information before providing it to internal teams, and a communication I will have to continue making to the users of every system that consumes Qualys data to allow them to make corrections to the Qualys data because it isn’t trustworthy as provided.
Hi, while it is good to see proactivity in identification of ‘Internet Facing Assets’, I am afraid the logic of the tag is incorrect.
I give you an example:
– An externally accessible server must be accessible via a public IP
– A server with an interface having public IP may not be Internet accessible – some companies use non-RFC1918 internally. As such this tag will be wrongly tagging systems that are internal
A much better approach would be to tag assets that were scanned using External Qualys scanner, or a selected Qualys scanner.
Can you make it so we can edit this tag or not use it at all?
I agree with all the comments to this post. It is a detriment to the usefulness of Qualys in our organization, with no option (as far as I know, yet) other than to purchase CSAM which includes EASM.
Addendum: I just discovered that the Internet Facing Assets tag CAN be edited, in GAV (free). Thank you Qualys! I rescind my previous comment.