April 2022 Release: New QQL Tokens, New Widgets to Enhance Dashboarding Capabilities, and More
The Qualys Cloud Platform April 2022 release includes Portal 3.11.1.0, which adds support for new QQL tokens and includes several new features and enhancements in Unified Dashboard.
Feature Highlights
Qualys Cloud Platform
New QQL Tokens
This release adds several new QQL tokens to enable you to search for vulnerabilities and assets based on your specified values.
Note: These tokens are available only if you have Qualys Cyber Security Asset Management in your subscription.
1. lastLocation
Now you can search for assets based on their last location and create VM widgets based on the specified location tokens in combination with a vulnerability query. This enables you to narrow down vulnerability-affected assets by location.
For example, you can provide the value for the lastLocation token as shown below:
lastLocation.country:United States
or,
lastLocation.country:[“United States”,”India”]
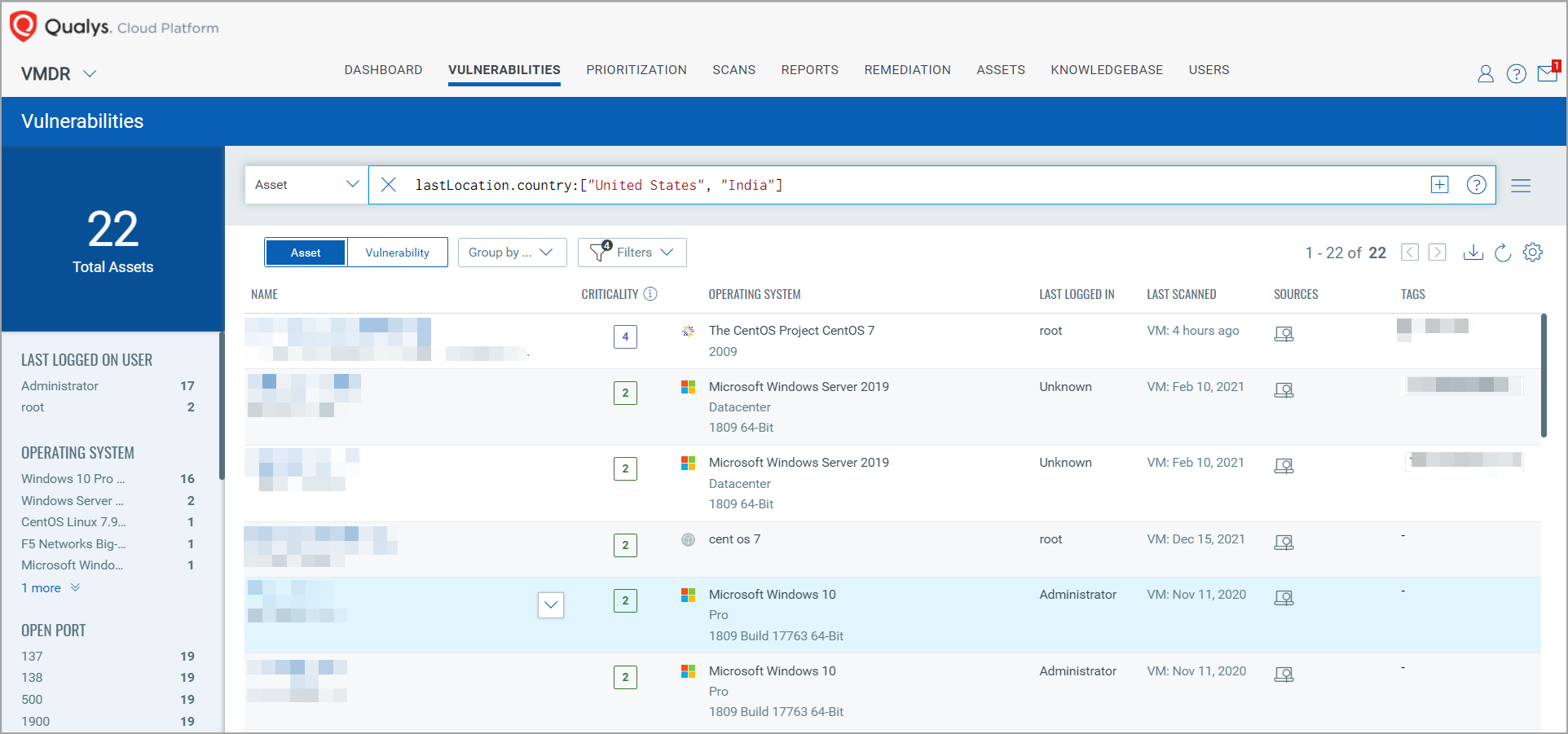
The results include all the assets that were last located in the specified countries, along with important asset and vulnerability details.
You can create new widgets by specifying these QQLs in the Query Settings page of the Widget Builder and use the Group By field to view the result grouped by the value you specify.
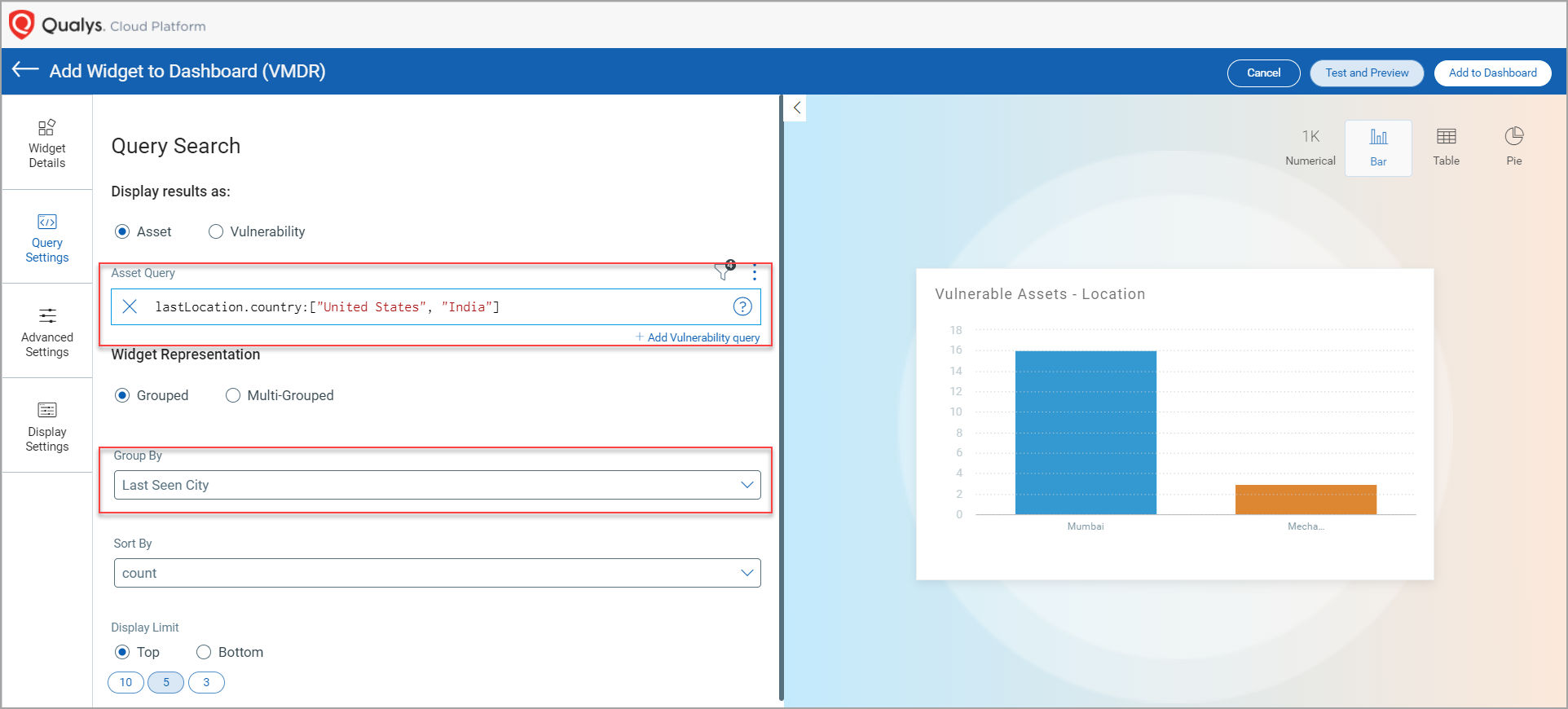
The following new QQL tokens have been added in this release:
- lastLocation.name
- lastLocation.continent
- lastLocation.country
- lastLocation.state
- lastLocation.city
- lastLocation.postal
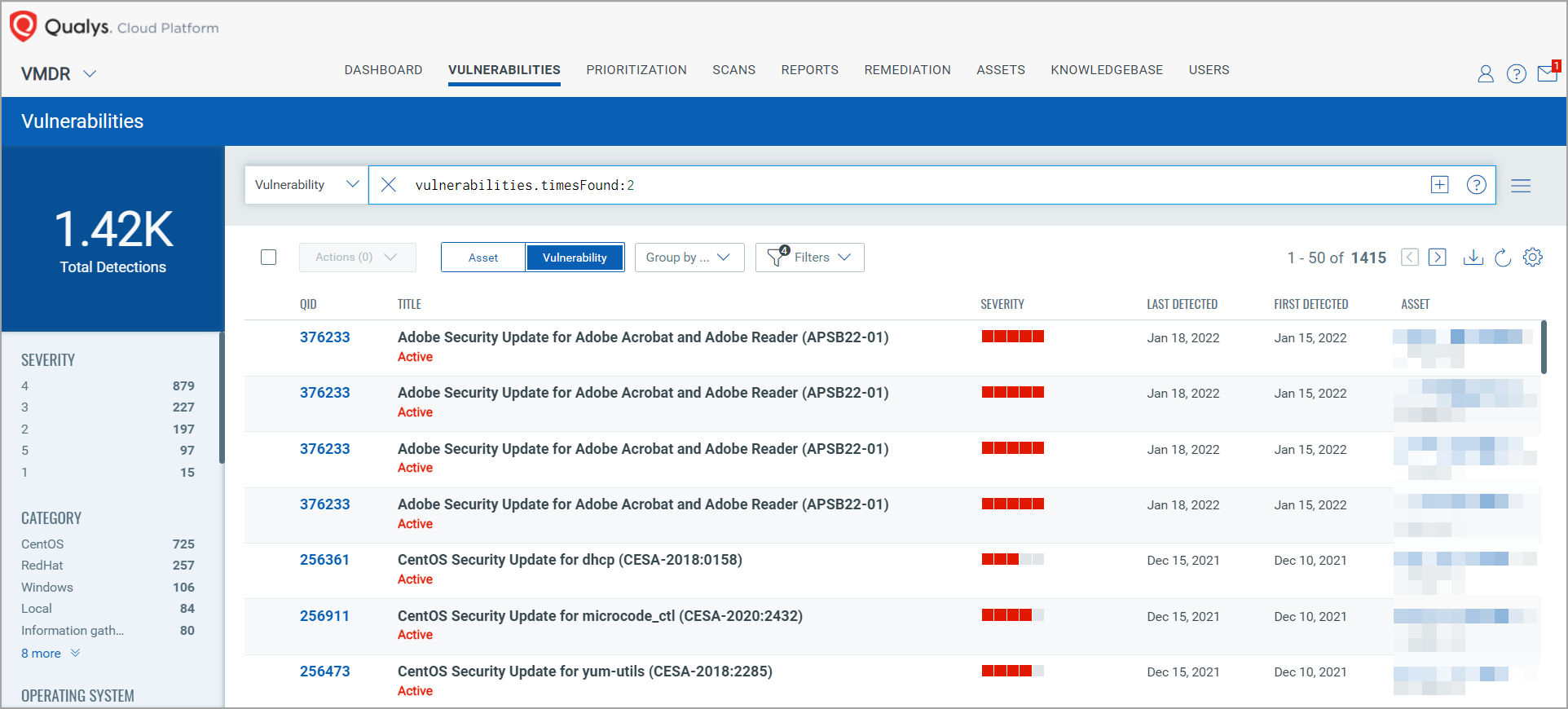
2. vulnerabilities.timesFound
You can now use the vulnerabilities.timesFound token to search for vulnerabilities that have been detected on your assets the number of times that you specify.
For example, you can provide the value for the vulnerabilities.timesFound token as shown below:
vulnerabilities.timesFound:2
vulnerabilities.timesFound>5
vulnerabilities.timesFound<10
The results show the vulnerabilities that were detected the number of times you have specified across your asset system, the corresponding QIDs, their severity, last and first detected dates, along with the asset name on which the vulnerabilities were found.
Unified Dashboard
Unique Count of Vulnerabilities Across Your Assets
With this release, you will be able to view the unique count of vulnerabilities impacting your hosts across the network as opposed to the total count of vulnerabilities that was previously supported. The Unique Count check box has been added in the Query Settings page of the Widget Builder, which enables you to choose to view the unique vulnerability count across your hosts. The Unique Count feature is supported for Count widgets and is available only when you select the Vulnerability option for Display results as in the Query Settings page.
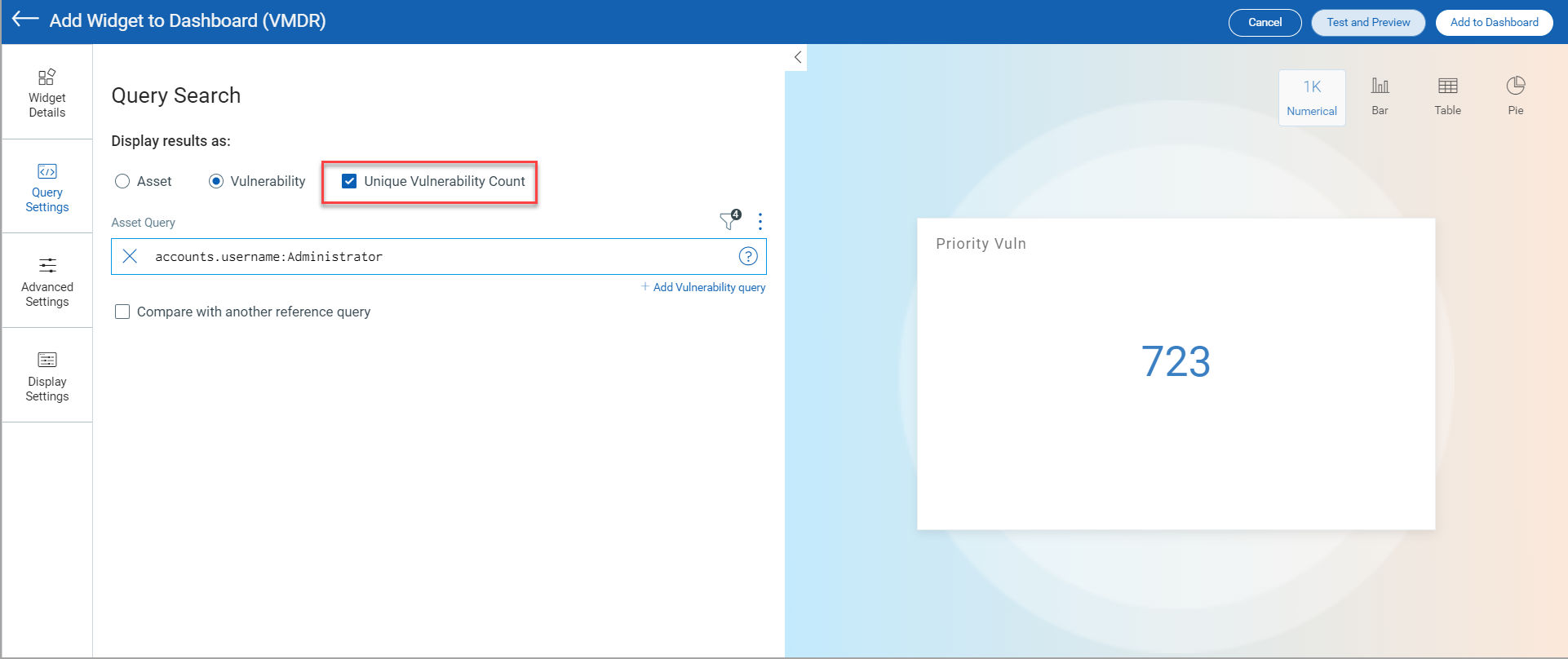
When you select the Unique Count check box, the widget will pull the total count of each QID detected in your environment. The unique count does not consider the number of times a particular vulnerability is found in single or multiple assets.
Note: Options for Trending Data and Targeted Vulnerabilities Search (Individual Detection) are currently not supported when you enable Unique Count.
Additional Columns for Table Widget for Group By Title
Previously, while creating Table widgets for vulnerability, only Title and Count columns were displayed when you selected Title in the Group By drop-down list. With this release, you can select any of the following columns to be added while a table widget to fetch vulnerability data:
- Published Date
- Updated / Modified Date
- Category
- Patch Available
- Qualys Patchable | YES / NO
- Severity
- CVSS Score
- Count
- QID
- CVE Ids
- OS
- Criticality
- Title
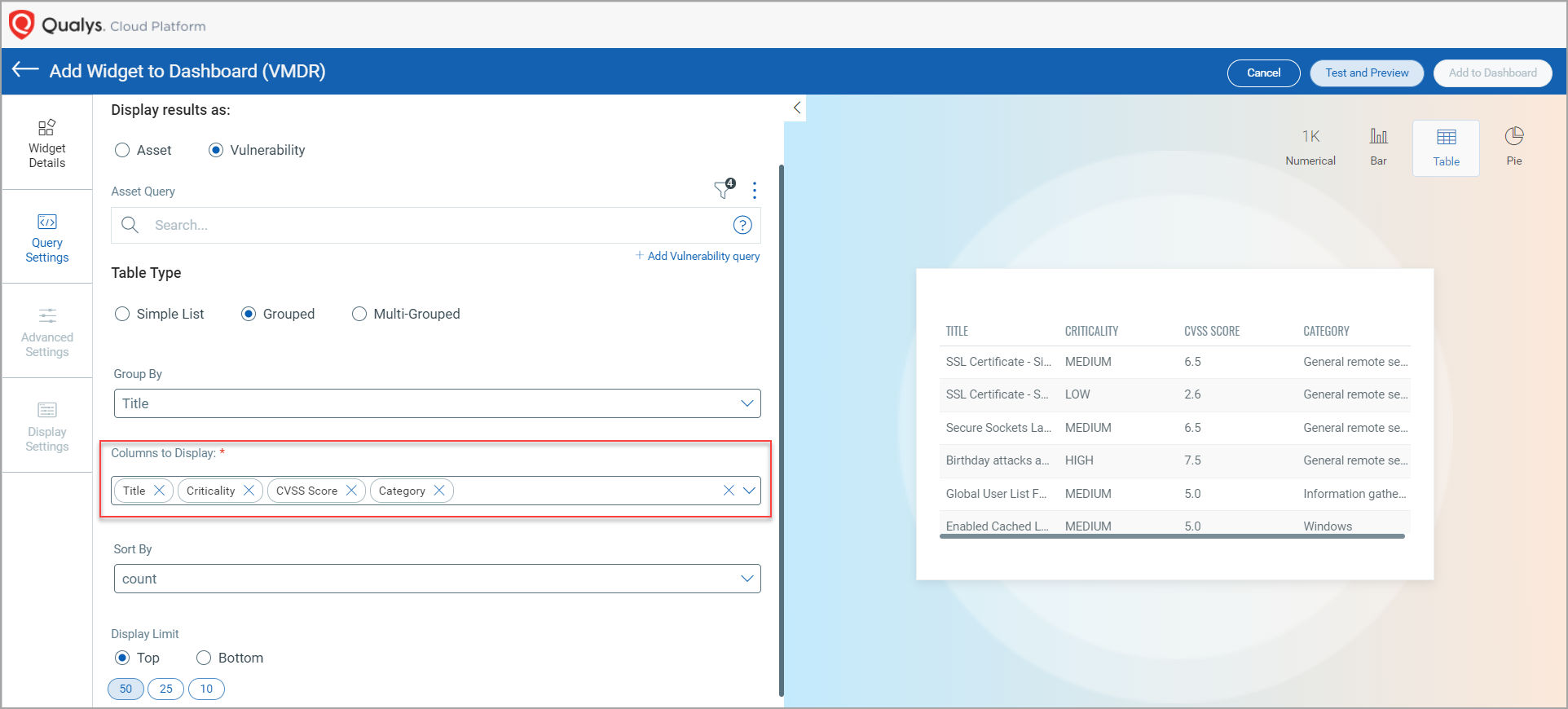
Note: The Trending Data and Multi Group-By options are currently not supported.
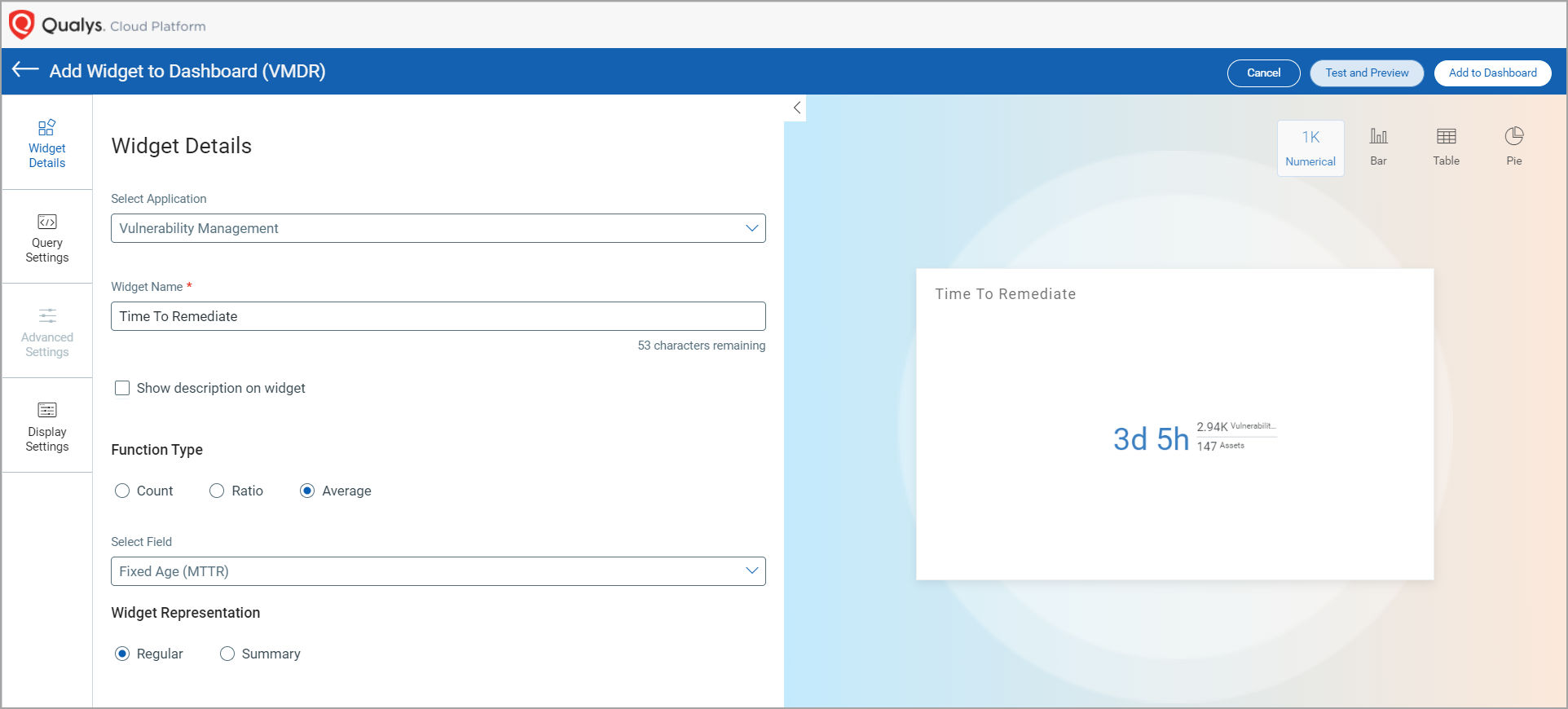
Widgets to View Mean Time to Remediation for Vulnerabilities
Now you can calculate the mean time to remediation for a vulnerability and search for vulnerabilities based on the average time taken from the day it was discovered to the day it was remediated. This new feature would help you create widgets and find vulnerabilities by the average time taken to remediate; thus, enabling you to access granular vulnerability information on your assets.